Welcome back, my hacker novitiates!
Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or service.
The Story of Max Vision
For example, the gray-hat hacker, Max Bulter, aka Max Vision, the founder of arachNIDS who's now serving 9 years in federal prison, found that the Aloha Point-of-Sale (POS) system had installed a remote backdoor to all their systems in order to provide technical assistance purposes to their customers.


These Aloha systems are used by small-to-medium sized restaurants that take thousands of credit card numbers each year. Knowing this, Max set a computer program to constantly scan the U.S. for systems that had port 5505 open. This would indicate that the computer was running Alaho's POS system, as port 5505 is not used by any other common service, and that the vulnerable service was open and available.

When he found the port open, he would then execute an exploit against that port and service and scavenge all the credit card numbers he could. He then sold them for $5 to $50 each bringing him a tidy return for each hack.
How to Scan for Vulnerable Ports
In this tutorial, we'll write a short script that does exactly what Max Vision was doing and send a report with every IP address of the vulnerable system.
Step 1: Open a Text Editor
To create our script, we need to open a text editor. Any of the Linux text editors will work; vi, emacs, gedit (in the GNOME), Kate, or KWrite. In this guide, we'll use the KWrite editor built into BackTrack5v3 KDE. We simply type in a terminal:
- kwrite globalportscan.sh
We can name our script anything, but I have chosen to call it globalportscan.sh.

This will open a blank file editor for our script.
Step 2: Create the Script
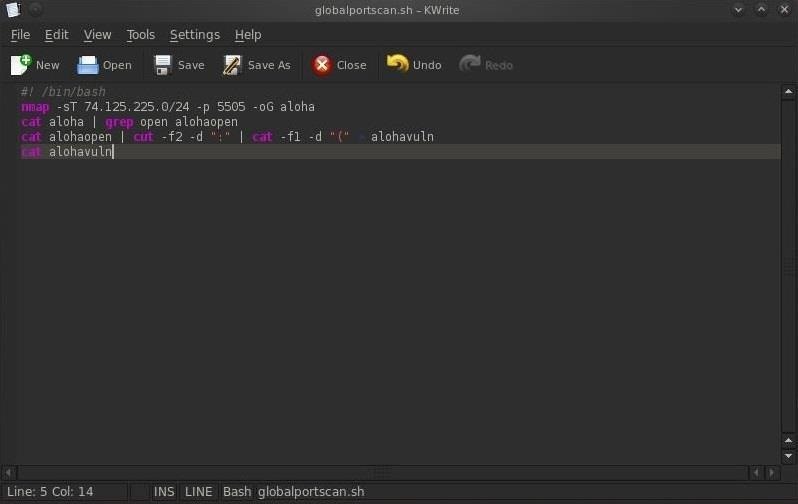
Now we need to type the following lines in our script file.
- #!/bin/bash
The required opening of all BASH scripts.
- nmap -sT 74.125.225.0/24 -p 5505 -oG aloha
Does an nmap connect scan (-sT) to the subnet of google.com and looks for the port 5505 open and sends the output (-oG) to a file called aloha.
- cat aloha | grep open > alohaopen
Opens the file aloha and filters (grep) for lines that say open, and stores those lines in a file called alohaopen.
- cat alohaopen | cut -f2 -d ":" | cut -f1 -d "(" > alohavuln
Opens the file alohaopen and cuts it at the second field (-f2) defined by the delimiter (-d) semicolon (":"), then pipes that to a second cut command that cuts the file at the first field (-f1) defined by the delimiter (-d) paren ("(") and saves it into a file named alohavuln.
- cat alohavuln
Finally, we open and display the file that contains all the IP addresses of systems with port 5505 open.
Step 3: Run the Script
Now that you have saved the script, it's time to run it.
- sh globalportscan.sh
Now, sit back and wait for your results. It could take a while depending upon how many IP addresses you're scanning. In our example, we're only scanning 255 addresses, so it only takes a few minutes, but you could very well set this up to scan millions of addresses, in which you might wait days for results.
Step 4: Final Results
We can run this script on any IP address or network. I just used google.com as an example (you're not likely to find port 5505 open at google.com). You should see results that look something like this:
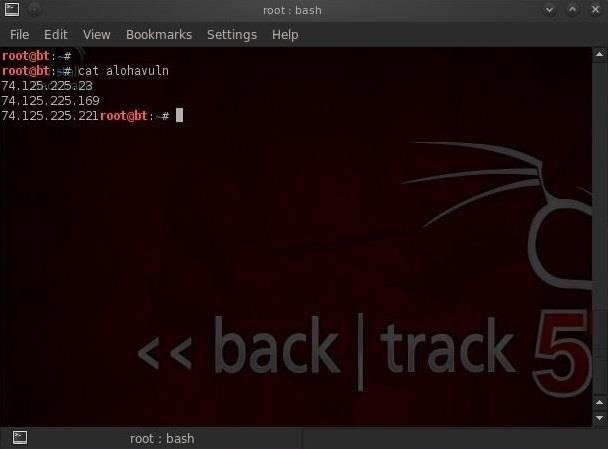
Of course, this vulnerability is likely closed in nearly all systems now, but this script can easily be edited to scan for other ports and other IP addresses depending upon your needs.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























21 Comments
Great tutorial! Kudos! Is there a way to set this to scan for multiple ports? For example, ports 1-500 or something like that.
Joshua:
Yes, but why would you want to do that? The whole point here is to find a port that reveals a particular vulnerability. If you just wanted to get a list of open ports, you could change the second line to read;
nmap -sT 74.125.225.0/24 -p 1-500 -oG aloha
OTW
hello admin, you website is interesting and the posts are very fascinating. but the problem is , i'm a new bee and i couldn't figure out where to start. could you suggest some posts for a beginner, related to hacking. And also , i couldn't remember them after a day. what do you think should i do to learn them perfectly.
Jason:
Welcome to Null Byte!
First, I put to together a number of tutorials on using Linux titled "Linux Basics for the Aspiring Hacker". Start with those. In addition, I have some tutorials here on installing BackTrack, starting out with WiFi hacking, starting out with Metasploit. Read and do those first and then advance to the more advanced hacks.
The only way you will remember is to practice everyday!
OTW
Eh... You are hardly "scanning the globe" by scanning a 24 bit subnet, there does appear to be quite a few valid IP addresses in that scope..
e.g. To get a list of valid hostnames in that subnet of 254 addresses do:
for i in $(seq 1 254); do nslookup 74.125.225.${i} >> scan.txt; done && grep name scan.txt | awk {'print $4'} | cut -d"." -f1,2,3
Nashville:
You are correct. I used that subnet, just as an example. Obviously, we can expand the IP address range to whatever scale we want. The larger the range, the more time it will take. If we expand the range to the whole globe it will take nearly forever. Its best to pick a small subnet and get a report and then scan another subnet, get a report and repeat...
If you try to scan the entire globe, we will likely be dead before it has completed. Then our heirs could read the report, I suppose.
OTW
i simply scanned my friends ip address, ofc with permission. by that i found an vulnerability, which has the following name: = FTP service AUTH TLS plaintext command injection.
service version
ftp pure-ftpd
as mentioned, i found it as a vulnerability. but the sad news is that metasploit dont have an exploit which match thesse requirments. i also found an exploit that support other language.
but i just want to know if there is another thing i can do, which i can use an exploit in any matter.
Iraq:
You might find this info useful;
The TLS protocol encrypts communication and protects it against
modification by other parties. This protection exists only if a)
software is free of flaws, and b) clients verify the server's TLS
certificate, so that there can be no "man in the middle" (servers
usually don't verify client certificates).
The problem discussed in this writeup is caused by a software flaw.
The flaw allows an attacker to inject client commands into an SMTP
session during the unprotected plaintext SMTP protocol phase (more
on that below), such that the server will execute those commands
during the SMTP-over-TLS protocol phase when all communication is
supposed to be protected.
The injected commands could be used to steal the victim's email or
SASL (Simple Authentication and Security Layer) username and password.
This is not as big a problem as it may appear to be. The reason
is that many SMTP client applications don't verify server TLS
certificates. These SMTP clients are always vulnerable to command
injection and other attacks. Their TLS sessions are only encrypted
but not protected.
A similar plaintext injection flaw may exist in the way SMTP clients
handle SMTP-over-TLS server responses, but its impact is less
interesting than the server-side flaw.
SMTP is not the only protocol with a mid-session switch from plaintext
to TLS. Other examples are POP3, IMAP, NNTP and FTP. Implementations
of these protocols may be affected by the same flaw as discussed here.
OTW
Kwrite isn't currently installed, what to do then?
It says to write apt -get install kwrite but that doesn't do the trick. I guess folder name or something has to be given. Help appreciated.
Got it, I installed the GNOME version, downloading the KDE version now.
Well the command was apt-get install kwrite (without the space).
Thanks anyways. :)
Sahir;
The GNOME version has gedit. It works just as well.
OTW
This was an EXCELLENT tutorial!! I actually learned much more than I expected -- a few simple commands of moving, copying files and backing stuff up. It turned out to be more than I expected. I think the most valuable part of the lesson was the concept of using variables and scripting something that interacts with the inputted data from a user for random needs. It's such a simple script, yet so POWERFUL for reconnaissance and information gathering. I already know every respectful hacker has a script like this ready for launch at a moments notice in their toolbox. It's so simple. The 'echo', 'read', '$', '>', and '-oG' commands. CHeers!! I'm going to write myself a script tonight when I grab my laptop back!!
John:
Glad you like it! You might like some of my newer tutorials on scripting as well.
OTW
Is doing a scan like this likely to land you in any trouble, or even raise some sort of alarm that you're up to something? I have read that some scans using nmap are considered invasive, and are illegal. Still haven't actually figured out where the line is drawn, though I guess it probably varies from land to land. I don't like the idea of doing a scan and having someone take notice. I know it's obviously advisable to always use 'cover' when possible, like proxychains or something, but what say you? I thoroughly love your tutorials btw, lucky to have found them.
Wiley:
Although some might find the scans intrusive, generally they are not illegal or even noticed. Every IP gets scanned 1000's time per day.
I'm glad you are enjoying my tutorials.
OTW
I want to learn more.. This is an interesting site. And i cant wait to surf for more infornation and tutorials. Even do i only have tablet for now.. I will still visit this site.. Good thing i found this type of site, so that i can expand my knowledge :).
Welcome Reinz!
I get an error message when I run this script;
thebestaround@TheBestAround:~$ sh globalportscan.sh
globalportscan.sh: 2: globalportscan.sh: nmap: not found
cat: aloha: No such file or directory
Here is the file name and script;
globalportscan.sh (written in gedit)
#!/bin/bash
nmap -sT 74.125.225.0/24 -p 5505 -oG aloha
cat aloha | grep open > alohaopen
cat alohaopen | cut -f2 -d ":" | cut -f1 -d "(" > alohavuln
cat alohavuln
Nmap is not installed on your system - that's why it says "nmap: not found".
Install it by running this command in the terminal :
sudo apt-get install nmap
Hello Sir OTW
I dont understand the following command even with your explanation
I would be thankful if you explained more of it.
$ cat alohaopen | cut -f2 -d ":" | cut -f1 -d "(" > alohavuln
Thanks.
Install kwrite
sudo apt-get install kwrite
Share Your Thoughts