Welcome back, my novice hackers!
In a recent tutorial, I showed how the SNMP protocol can be a gold mine of information for reconnaissance on a potential target. If you haven't already, I strongly suggest that you read it before progressing here, as little of this will make much sense without that background.
Cracking SNMP Passwords with Onesixtyone
The MIB database, created by SNMP, contains extensive information on every device on the network. While SNMPv1 is very insecure and SNMPv3 is very secure, many companies still use SNMPv1. As such, the community public string (password) that provides access to SNMP and its MIB database is susceptible to cracking. Once the hacker has the SNMP community public string, they have access to all the info available in the SNMP MIB.
Better yet, if we can crack the private community string (password), we can change the settings on any network device—even take it off line. We could then potentially change the configuration settings on switches and routers to our advantage.
In this tutorial, we will be cracking the SNMPv1 community string (password) with one of the best SNMP cracking tools, onesixtyone (SNMP runs on port 161, hence its name).
Step 1: Find Onesixtyone
Onesixtyone—like so many of the best hacking tools—is built into BackTrack, so no need to download and install if you're running BackTrack. We can find onesixtyone by going to BackTrack -> Information Gathering -> Network Analysis -> SNMP and then onesixtyone, as shown in the screenshot below.
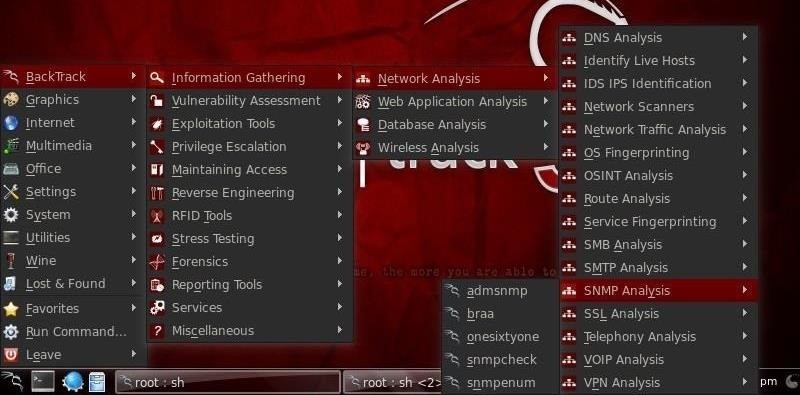
Step 2: Open Onesixtyone
When we click on onesixtyone, we will be greeted with a screenshot like that below.
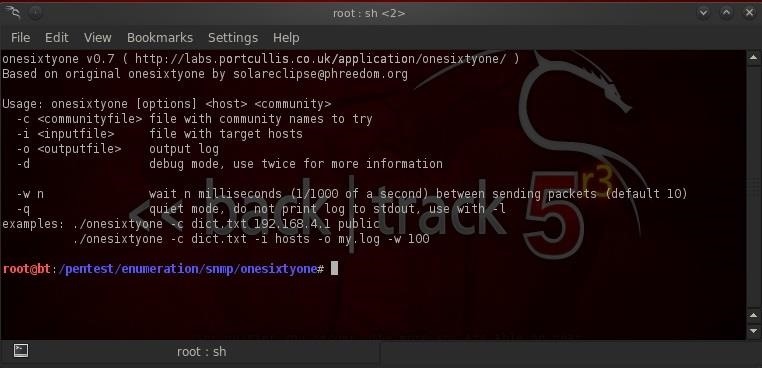
Notice in the third line that the basic syntax for usage of onesixtyone.
- onesixtyone (options) <host> <community>
Where:
- host is the IP address of the system we are targeting
- community is either public or private
Like any password-cracking software (that is not using brute-force), it's only as good as its wordlist. Onesixtyone comes with a built-in wordlist of commonly used passwords on SNMP, but if your password isn't in the list, you can use any word list you want.
Very often, if a sysadmin changes the SNMP community string, they will change it to something simple like the companyname-public or companyname-private. It's always worth trying these or similar combinations before attempting a password crack.
Step 3: Take It Out for Spin
Now that we understand the basics of how onesixtyone works, let try it out.
- ./onesixtyone -c dict.txt 192.168.1.119
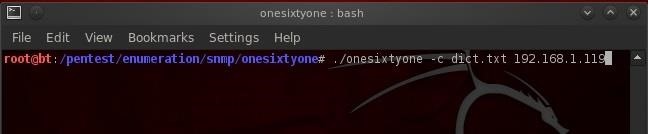
Now, all we need to do is hit enter and let onesixtyone do its job!
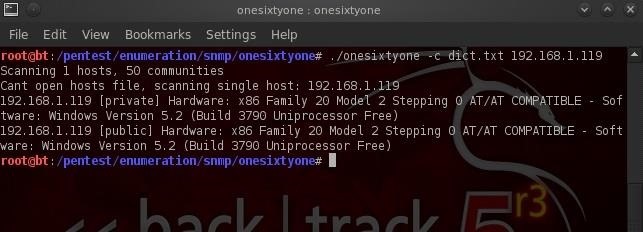
When using the built-in wordlist dict.txt, onesixtyone finishes its work in short order. Obviously, with longer word lists, this process can be more time consuming. To use another word list, simply replace the dict.txt with the full path to the file, such as:
- ./onesixtyone -c /root/anotherwordlist 192.168.1119 public
As you can see, onesixtyone was able to find the both the public and private community strings. The network administrator left both strings at their default values, which is common.
Other possible sources for potential word lists can be found here, among other places on the web, and some are as big as 50g!
Keep coming back for more adventures in Hackerland!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























9 Comments
master otw:
how can i know tht network is using SNMP 1 ....and the same SNMP works for whole network or same wifi????????????
Secret:
First, you are misunderstanding SNMP. It is not for wifi communication, but rather communication between devices for management of those devices.
Generally, when SNMPv3 is implemented, SNMPv1 is left in place to communicate with older devices that are not version 3 compatible. Go ahead and try to crack the strings and you will usually be successful.
OTW
thnx master very clear now.. :)
sir, ma using kali os, but when i run this command on my target ip "./onesixtyone -c dict.txt ip" here is what i get bash: ./onesixtyone: No such file or directory
Horls:
Welcome to Null Byte!
I'm pretty sure onesixtyone is built into Kali. Type "locate onesixtyone" and it will tell you its location. Then navigate to that directory and try again to run it
OTW
thanks for the reply realli appreciate your quick response, God bless you. here is the result i have: /usr/bin/onesixtyone
/usr/share/applications/kali-onesixtyone.desktop
/usr/share/doc/onesixtyone
/usr/share/doc/onesixtyone/README
/usr/share/doc/onesixtyone/changelog.Debian.gz
/usr/share/doc/onesixtyone/changelog.gz
/usr/share/doc/onesixtyone/copyright
/usr/share/doc/onesixtyone/dict.txt
/usr/share/kali-menu/applications/kali-onesixtyone.desktop
/usr/share/man/man1/onesixtyone.1.gz
/var/lib/dpkg/info/onesixtyone.list
/var/lib/dpkg/info/onesixtyone.md5sums
Horls:
As a newcomer to hacking, I recommend this article titled "Hacking for Newbies". It lays out a plan for learning the basics of hacking from my tutorials.
Best of Luck!
Otw
Sir. the ip entered in this article is of what..
Because i m going to try this in my college.
And college network is too big so, what target IP should i input?
And really great article.
Hi I've been trying all kinds of snmp enumeration tools. I have a Kali Linux VM, and I'm targeting a vulnerable machine I got from offensive-security.com called "metasploitable2" and I'm doing all this on my home network with my own router, etc. But all I get when I run these tools is something like: "Scanning 1 hosts, 49 communities"
and then the tool returns with no other output. Do you know what's going on? I opened dict.txt and it has stuff in it. Does some snmp service need to be running on my Kali VM? Or do I need to change some config file or something? I'm totally stuck and I can't figure out if it's my network or my VMs or what.
Share Your Thoughts