Welcome back, my greenhorn hackers!
My preference for Linux as a hacking platform is well documented, and I have even created a series of tutorials to train new hackers. Without being proficient in Linux, you can't really call yourself a hacker.
Every once in while, though, a hacking tool comes out for Windows that makes me stand up and take notice. For instance, Cain and Abel is an excellent tool for password cracking and MitM attacks and is only available on the Windows platform. I could name a few others, but only Havij, the excellent SQL injection tool, comes immediately to mind.
FOCA was released in 2009 and is now in version three. Although a Linux version is included in Kali, it is outdated. Let's download the latest Windows version and use it here to perform some reconnaissance.
Good Reconnaissance Is Critical
FOCA is an excellent website reconnaissance tool with lots of interesting features and capabilities. Remember, before attacking any website or domain, it is critical to gather as much information as possible. From this information, you can determine the attack that is most likely to work against that site or network.
In this tutorial, we will looking at FOCA's ability to find, download, and retrieve files from websites with the file's metadata.
This metadata can give us insight into such information as the users (could be critical in cracking passwords), operating system (exploits are OS-specific), email addresses (possibly for social engineering), the software used (once again, exploits are OS-, and more and more often, application-specific), and if we are really lucky, passwords.
Step 1: Downlaod FOCA for Windows
First, let's download FOCA Free 3.0 for Windows.
Step 2: Choose Where You Save Results
When you install FOCA, you will greeted with a screen like that below. The first task we need to do is to start a new project and then tell FOCA where we want to save our results.
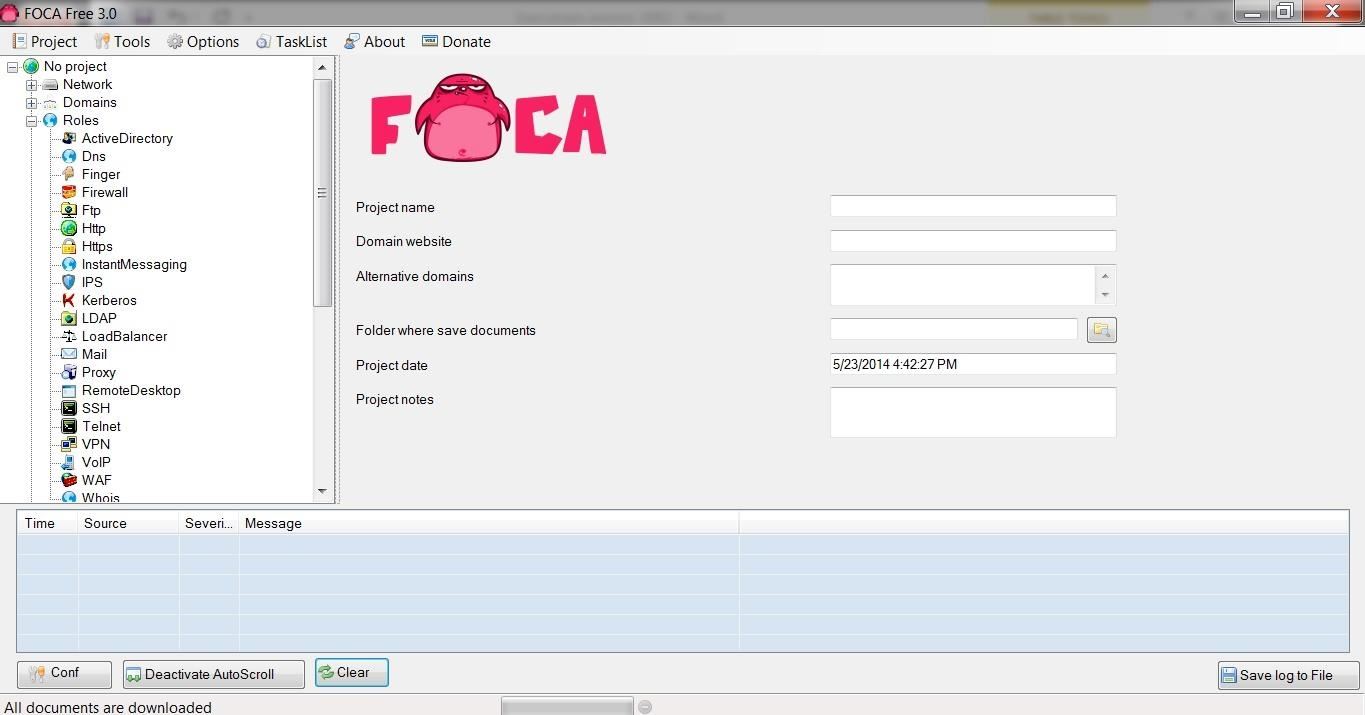
I created a new directory at c:\foca and will save all my results there. Of course, you can save your results wherever is convenient for you, or use the default temp directory.
Step 3: Create a Project
In this tutorial, I will be starting with a project named after the information security training company, SANS, which is located at sans.org, and I will be saving my results to c:\foca.
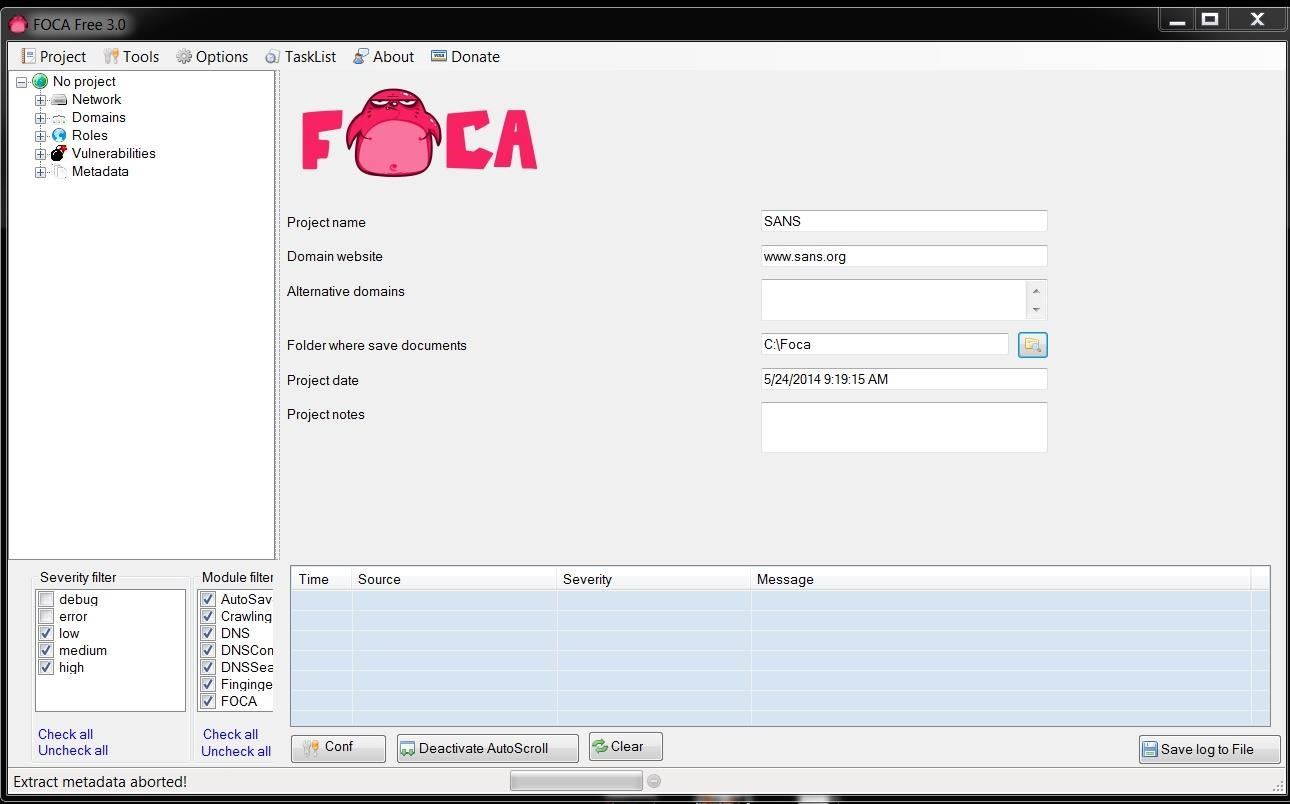
Step 4: Getting the Metadata
Once I create my project, I can go to the object explorer to the far left and select Metadata. This enables us to pull the metadata from the files on the website that contain metadata. Files such as .pdf, .doc, .xls, etc. all contain metadata that could be useful in your hack of your target.
When you select metadata, you will pull up a screen like that below. In our case here, we will be searching sans.org for .doc files, so the syntax to be placed in the search window is:
site:sans.org filetype:doc
This will search the entire sans.org website, looking for .doc files. When I hit the Search button next to the window, it will begin to search and find all the .doc files at sans.org.
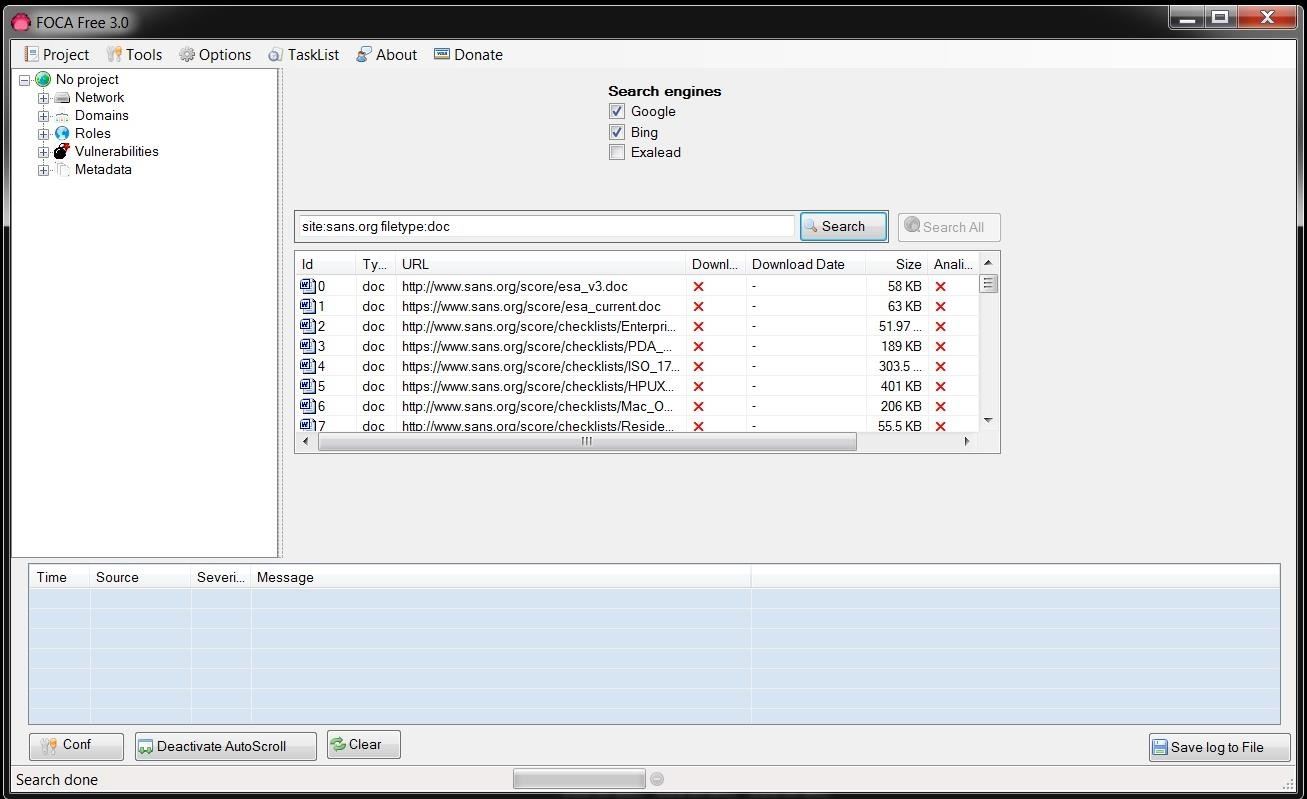
Of course, if you were searching for .pdf files or other filetypes, you would put in that filetype. You can also search for multiple filetypes by listing them after filetype, such as:
site:sans.org filetype:pdf,doc,xls
Step 5: Download the Files
Once FOCA is done retrieving a list of all the .doc files, we can then right-click on any file and download the file to our hard drive, download all the files, or analyze the metadata. I chose to download all the .doc files I found at sans.org.
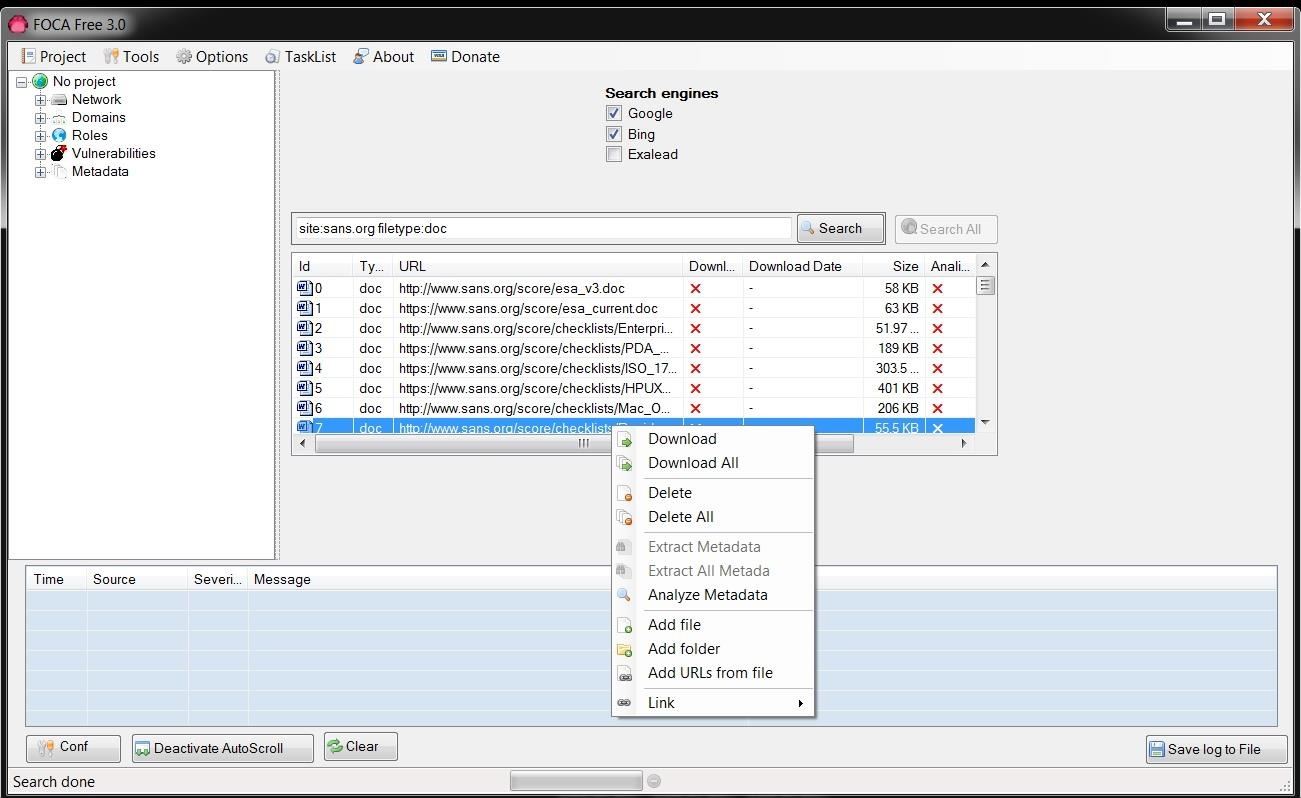
Step 6: Collect & Analyze the Metadata
Now that we have downloaded all the .doc files, I chose to analyze all the metadata in them. Microsoft's Office files collect significant amounts of data as they are being created and edited that we can then extract.
When we expand the Metadata folder in the object explorer, you can see that we have 156 .doc files and 2 .docx files.
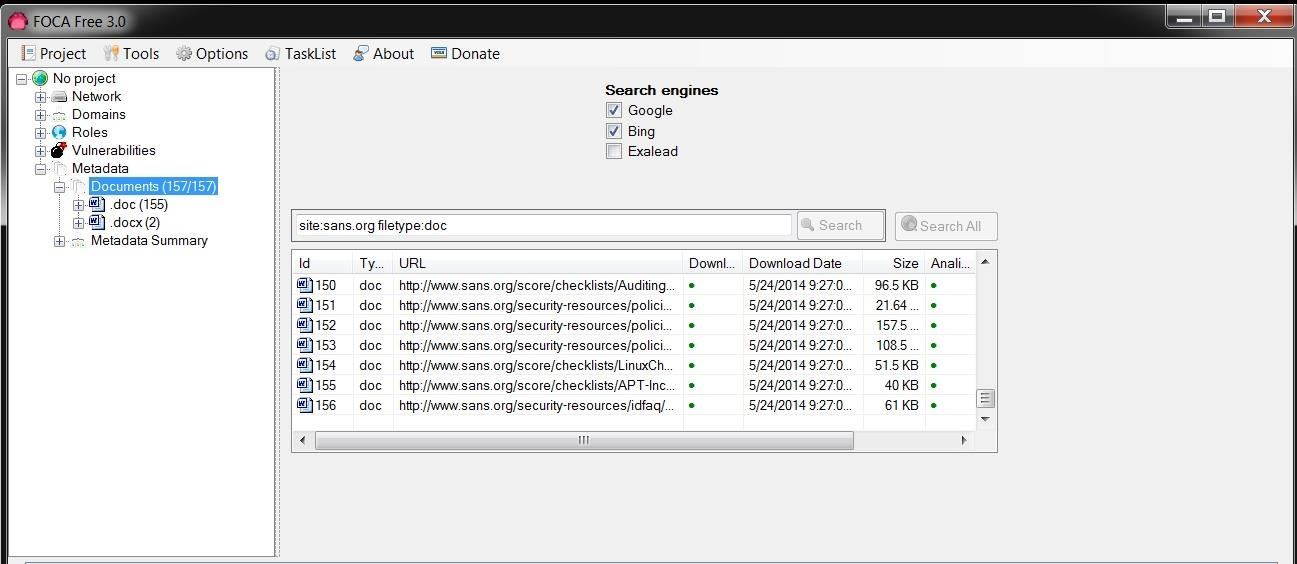
The Types of Metadata Collected
Just beneath the Metadata documents folder is another folder titled, Metadata Summary. We can click on it and it reveals the type of metadata is has collected from the files. This metadata is broken into eight (8) categories:
- Users
- Folders
- Printers
- Software
- Emails
- Operating Systems
- Passwords
- Servers
Let's take a look at Users first. When we click on users, we can see that FOCA has collected the names of every user that worked on those files.
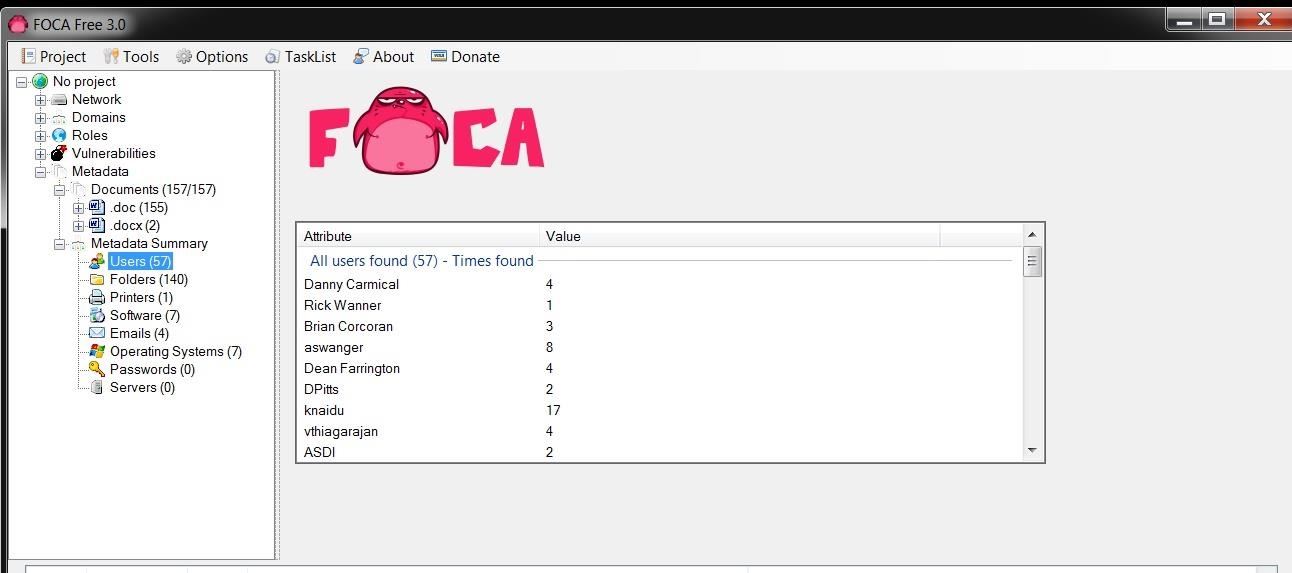
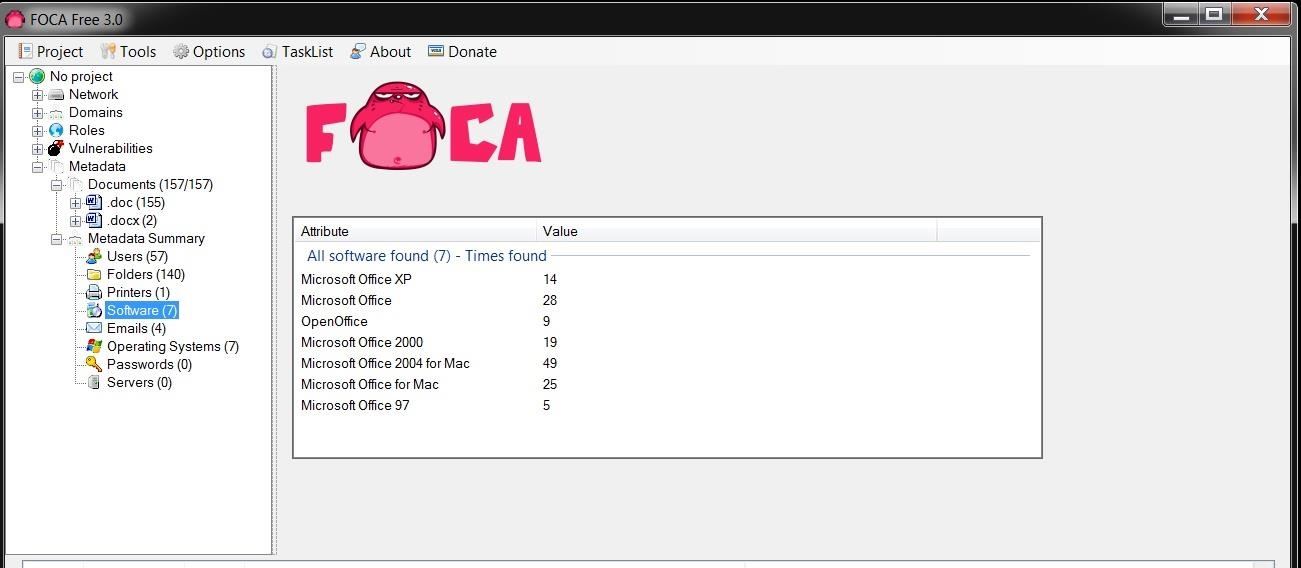
When we click on Software, we can see the various editions of Microsoft Office that has been used, including five (5) users that created their documents with Office '97 (hmm...wonder if there are any Office '97 vulnerabilities still out there?).
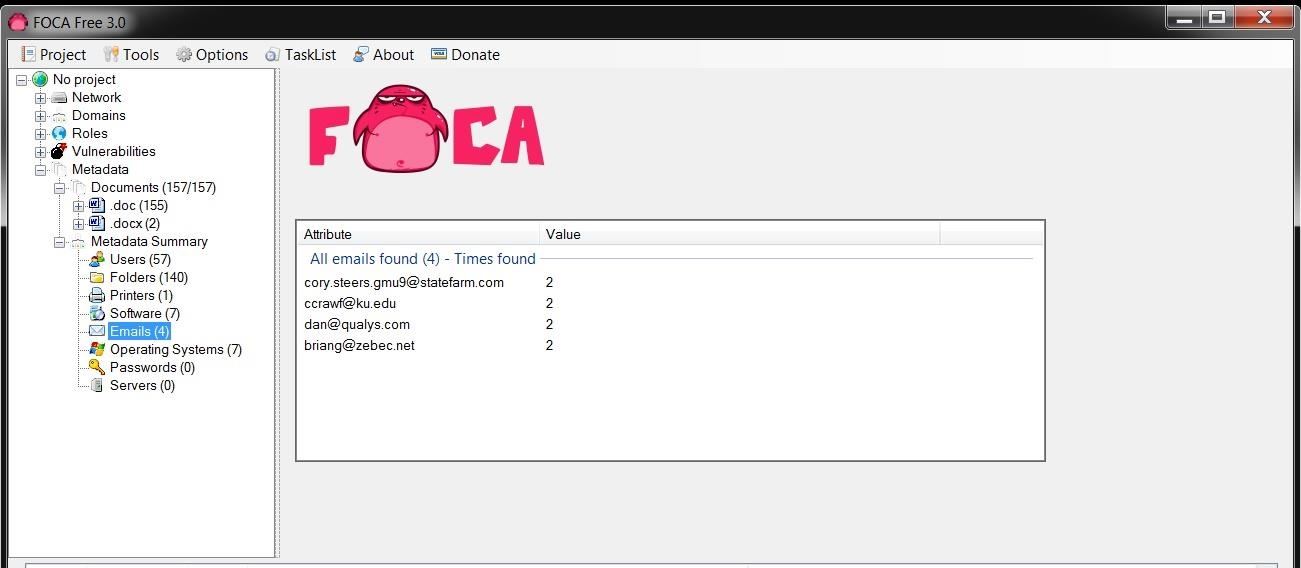
We can also look for email addresses that are embedded in the documents as displayed below. Obviously, these folks are making themselves available to a social engineering attack.
We can also gather printer, folder, passwords, and servers from this metadata depending upon the documents we recover. All of this information can then be used to determine what is the best attack against this organization/website.
In future tutorials, we will continue to explore the capabilities of FOCA, so keep coming back, my greenhorn hackers!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























22 Comments
Can you run FOCA in wine?
Jesse:
It will probably work in wine, but I wouldn't suggest it. Instead, just use the Linux version.
OTW
Owt:
I thought you said it was outdated. So you would feel comfortable using it over the windows version?
No, I didn't say I preferred it, but it is available if he doesn't have Windows.
No it will not run in wine, at leasts not natively.
Jesse Jesse Jessee, you should have at least one vm setup with xp. Install into that'
Personally I have vms of xp, win200, vista, debian cli. How else are you gonna test exploits. But I will test it in wine and let your know, or better yet you can do it.
I love that you chose SANS as the target !! That's awesome.
another great tutorial.
Just for info guys,
I have been doing some work on getting foca to run in wine. If your using Ubuntu,mint etc you can do it fairly easily with wine tricks. there are several guides if you do a search.
If your using Kali, there is something its missing which will not let it run properly. I may take the time to find it and fix it, but I am finding it runs fine in xp vm.
Great article.
I tried using it with a proxy via a SSH tunnel to obfuscate my IP but it wouldn't route to Google or Bing, any idea why?
I need to configure a proxy in my system to use FOCA? I mean. This make noise?
No, you don't need a proxy to use FOCA.
Oh ok. Ty OTW ^^
Hmm spanish stuff! +1
Great Tool ! Thanks for Posting OTW.
Great tool
Looks great but I can't seem to get it to work on any website :
"16:44:23 MetadataSearch debug Web Search, GoogleWeb Google Captcha needed! "
And Bing doesn't find a single file.
Any Ideas ?
Try giving us a screenshot so that we can help you.
thanks for answering so quickly, you've been really on fire these days
Here's a shot
http://imgur.com/HGUohPw
And the full log:
http://pastebin.com/79zq0TKy
seems Google just captcha-blocked the request ?
@WireWise : Thanks but I'm not using any proxy nor VPN
did U managet to overcome the G Captcha issue?
nope
I have the exact same problem.
These sites don't normally require captcha, search engines are doing this automatically? Obviously this doesn't occur for everyone, so why do they know only when some people are automating a search in this manner and blocking it?
For that matter why should a search be blocked anyway if it is only a single query?
I believe if your using a proxy google doesn't let you use google normally unless you have a API. So if your using a proxy you need to use a google API. I'm not sure if this also happens with VPN's.
Share Your Thoughts