Since Ive started to learn about nmap and metasploit and other tools I was learning well but I had one problem,
I had nothing to practice it on.
As a result I asked someone about my problem and they told me about Vulnhub. It's a great way to practice.
Its good beginners and people practicing for real ctf competitions alike.
It was difficult to find how to set it up on Kali Linux so I decided to make this tutorial.
Step 1: Downloading the Virtual Machine and Installing It
You will have to be on 64-bit for this.
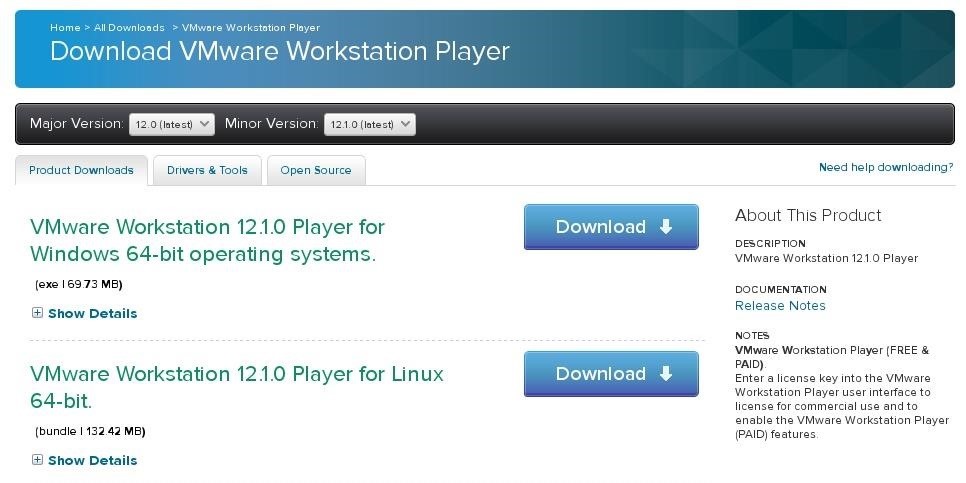
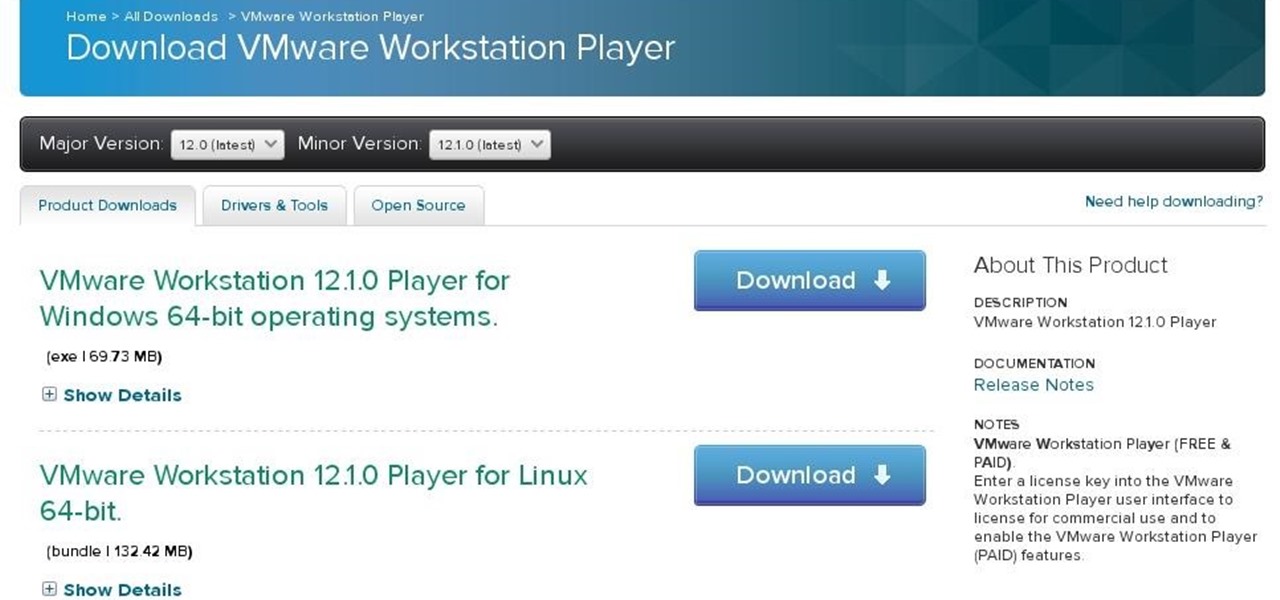
1.First download VMware Workstation player from here (its free) VMware Workstation Player.
2.Next once you have that downloaded open a terminal and navigate to where you saved it (Default is cd Downloads).
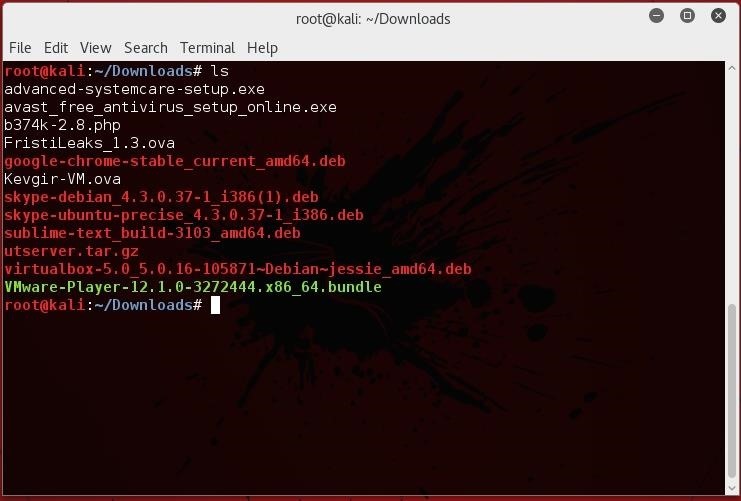
3.Then your going to want to make it executable by using this command
chmod +x name of file.
4.Now your going to have to download and install the packages needed by the installer apt-get install build-essential linux-headers-`uname -r`.
5.Finally run and complete the installer ./Name of file (if it asks for a license key choose I will fill it in later or something like that).
Step 2: Setting Up a Ctf and Finding the Ip
So your going to have to set the Vm up so only you can access it and no "l33t Hax0rz" on your network hack it.
1.Download a practice ctf from Vulnhub a good starter one is SickOs 1.1.
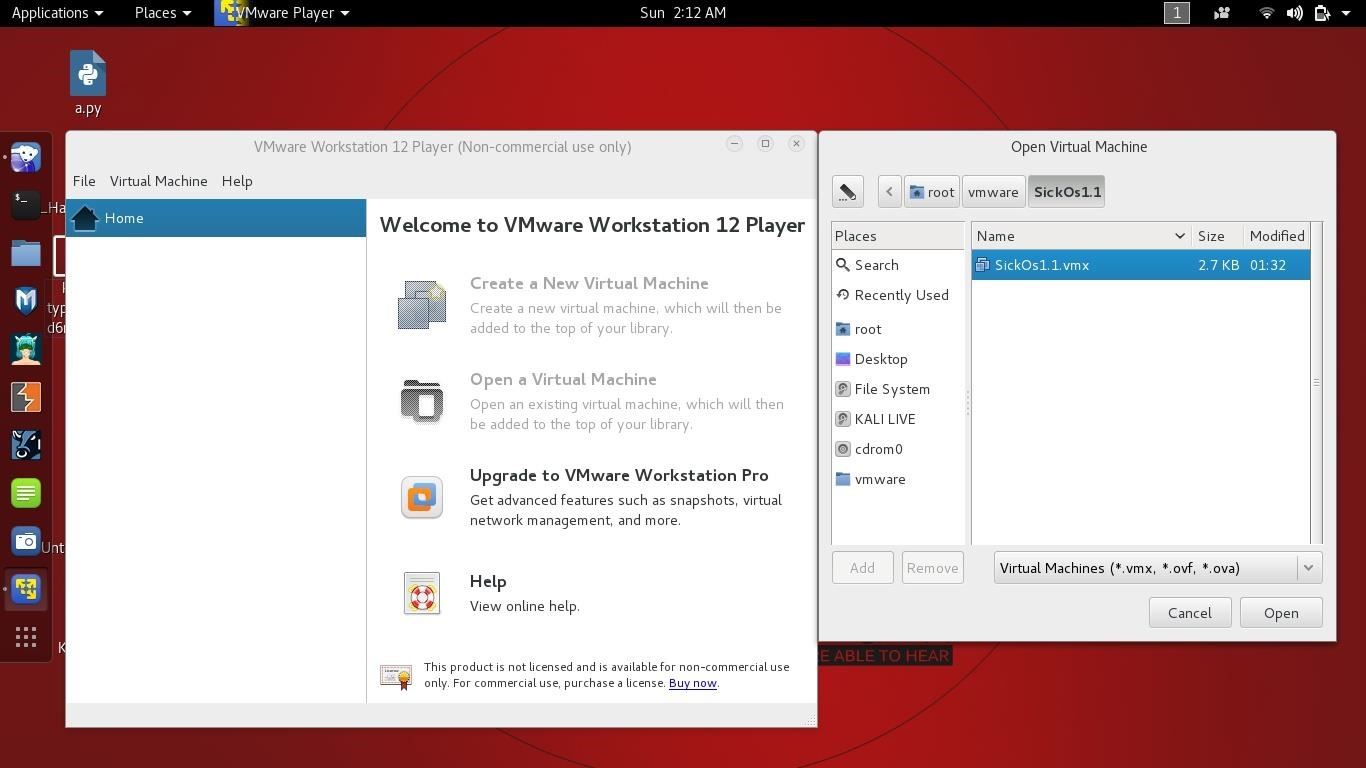
2.Open Vmware and click open a machine and pick one of the files your Vulnhub Vm it comes with.
- Once it boot's click Virtual Machine and go to Virtual Machine settings then switch the network adapter to host only.
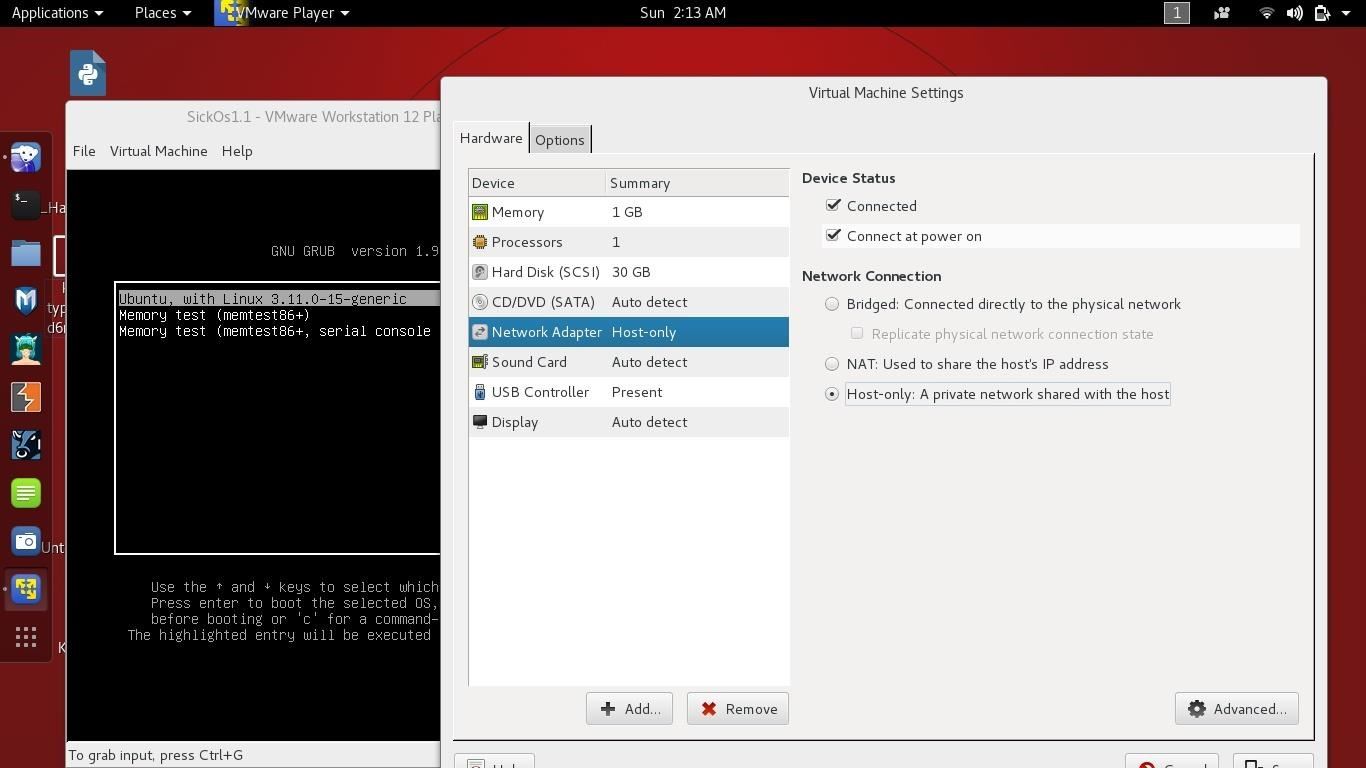
4.Restart the Virtual Machine by clicking Virtual Machine and then power then finally click restart guest.
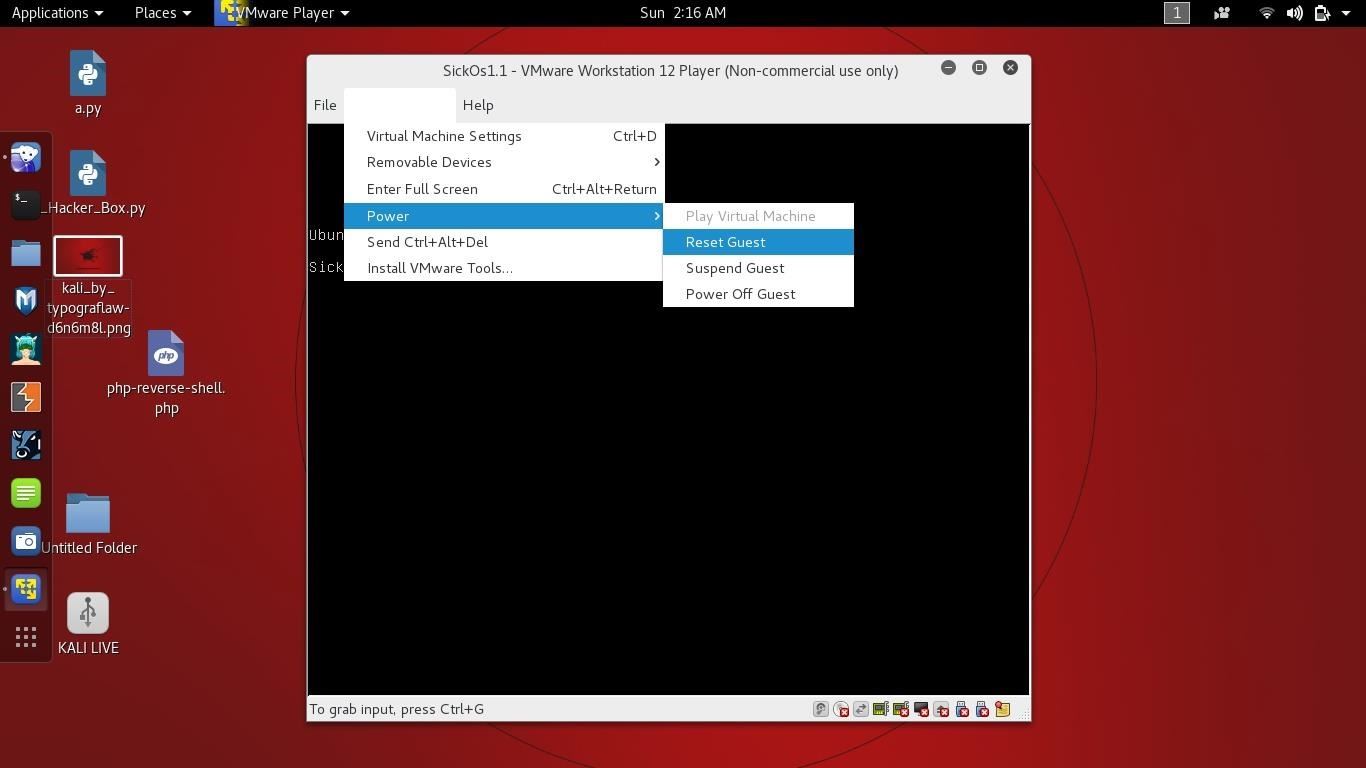
5.Open a terminal and type arp -a and pick the vmnet8 or vmnet1 ip (only one will work).
Step 3: Hack It
Well your free to practice on it. Remember if you get stuck then you can look at the walkthrough-The 0ne
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















11 Comments
I just finished hacking SickOS1.1.
I was able to do most of the recon on my own, but needed a walkthrough for the rest.
From the point where the password is found I could do it on my own again.
I am still new to this, so I learned a lot! Thanks!
Any further recommendations for beginners?
Thanks, Kioptrix Level 1 Kioptrix Level 1.1 Kioptrix Level 1.2 Kioptrix Level 1.3 are good places to start.
Nice tutorial +1, remember folks that step 2.3 in this tutorial is VERY important, if you mess up this step your vulnerable machine will be accesible trough WAN (the internet).
who doesnt want a bunch of hackers attacking their CTF box through the internet ;P
Well, I am actually running it on my old Laptop in VMware Player, and the attacker is a Kali install on my new Laptop... Maybe not the best idea... Running both systems on just one of the Laptops would be too much, though.
After nmap scan on my VM only port 902 seems to be open, it says ssl/vmware-auth as service. I'm trying to get through SickOs 1.1
What should I do to find more ports? I've seen many walkthroughs with squid proxies, ssh...
use --open to scan for only open ports
I mean that only port 902 is open and I can't find any kind of exploit
port 902 is usually used to host some kind of server. Already now you should have numerous methods at your disposal.
I created a new VM and now i cant find it in my network. what do i have to do? thanks for all
you wont be able to see a virtual machine on your network, it needs to be booted as a live OS.
Share Your Thoughts