Hi guys, I am newbie to web security and I recently bought a vps for my forum and trying to secure it as much as possible.
- I'm using Nginx server as frontend, apache as backend on Debian 8.
- I'm keeping up to date web servers and distro
- Not using so many 3rd party tools.
- Using cloudflare to harden security:
1) Bought a SSL certifiacate and using it with Cloud Flare's Full strict Security
2) Set security level to High on CloudFlare
3) I'm trying to hide my real ip. So I deleted default A record on DNS page and redirected all of my subdomains to CloudFlare. Deleted MX records(not using mail system at all) You can't get my ip with pinging direct-connect.domain.com etc. But DNS lookups history leaks my ip. Since I'm fully on CloudFlare I will change my ip and as default change mail server ip to prevent leaking real ip by DNS lookups history.
4) I'm using DNSSEC which protects against forged DNS answers
5) I set up the HTTP Strict Transport Security (HSTS)
Even though I hide my IP behind CloudFlare there stil are some ways to get real ip. So I still had to secure my vps in case of the IP leakage.
- I don't want to redirect to http to https since it's vulnerable to lots of attacks. I've added some commands to .htaccess rewrite url path and write a special plugin for my config to create real https url's
- I installed modsecurity for both apache and nginx
- I'll add ipignore list for my vps when I get static IP from my IPS. So only me and cloudflare IP's may have connection to my vps. But there have to be some way to spoof ip, since CloudFlare IP's are public.
- I ran nikto and I got lots of vulnerability. I fixed almost all of them:
X-XSS protection header,
Etag,
OSVDB-3233
phpmyadmin path etc.
Here how nikto test result looks like now:
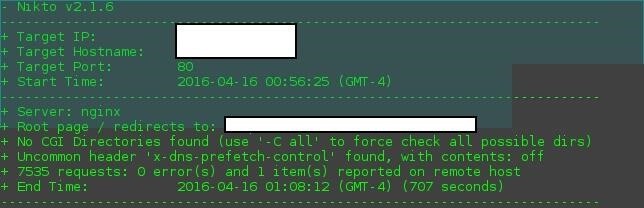
I also ran with -C all so nothing to worry about it.
- Added fail2ban to prevent ssh bruteforce
- I'm not using anything to secure FTP but generally I'm trying to use SFTP.
- I didn't do anything about ports but will filter some of the and close the unnecassary ones.
- Using CSRF protection which is implemented using a randomly-generated token.
- I added a sanitization for sensitive data
That's all I've done so far. The subject name is "Could you hack my server" but I'm not claiming that I'm unhackable, No! Evrything is hackable with required skills and effort. But I'm just curious that how would "you" hack my server with given information. What shuold I do to harden my secuirty?
Edit:
I forgot to say, I have two-factor auth for literally everything, Cloudflare login to Gmail. And every night before sleeping. I check logins for my accounts, logs etc.
Also I have LogDog installed on my phone. And I'm not using anything beside Linux for myself.







































8 Responses
It'd probably be easier to hack you instead of hacking your server.
I forgot to say, I have two-factor auth for literally everything, Cloudflare login to Gmail. And every night before sleeping. I check logins for my accounts, logs etc.
Also I have LogDog installed on my phone. And I'm not using anything beside Linux for myself.
Looks like you have a nice security plan, but why do you use services like gmail?
If you would'nt use services like gmail you would have less trouble and you wouldn't need things like logdog.
It's my personal e-mail. Since I don't have mail server(to avoid leak real ip adress to script kiddies)I use gmail. With LogDog and Two Factor Auth together, it's pretty secure I guess. What should I use instead of gmail for my personal e-mail?(also CloudFlare registered on it)
Every other email provider is better than gmail from google.
Here a short list of some:
https://en.wikipedia.org/wiki/Comparison_of_webmail_providers
This is great and all, but be sure your nullbyte account is in no way linked to you personal details. Because basicly you gave up info that requires extensive reconnaisance and enumeration normally.
I can simply ask my wife to get your whole Gmail inbox delivered to me as she is a GC support engineer and you can go ahead waste your time by meaningless 3rd party googling software installation.
Here is my answer, no one would able to hack you. only 0.1% in the world can probably unlock a couple of your free version software. and they are not interested in these toys. Also, anyone can hack your whole life very easily with money, even undercover cops can find you within a few days. Money talks. not skills.
Money can decrypt 512bit VPN in a day.
Bought a SSL certifiacate. (why? does it gives you 2048 or 4096bit encryption?)
and using it with Cloud Flare's Full strict Security (since when CF became full strict security?)
Added fail2ban (fail 2 ban lol) to prevent ssh bruteforce (uh what?! HAHAHA)
I'm not using anything to secure FTP but generally I'm trying to use SFTP. (it's all same tunnel protocol on top of the same "S"ecurity before ftp, sh, etc
I didn't do anything about ports but will filter some of the and close the unnecassary ones.
Using CSRF protection which is implemented using a randomly-generated token.
I added a sanitization for sensitive data.
Nginx in front and apache in the back for what purpose?
you gotta worry about your time kid.
I simply said "Hi guys, I am newbie to web security." Fix your ego and maybe you'll worth arguing with in the future.
Share Your Thoughts