Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.
Most Linux distributions are highly customizable. This makes personalizing your penetration testing distribution a bit daunting. With just a few commands, we can automate tasks, install our favorite software, create additional user accounts, properly configure anonymity software, and optimize our interactions with terminals. There are just a few things we can do to improve our interactions with the operating system.
1. Install Git
Git is an open-source software version control application. It can be used for collaboratively sharing and editing code but is commonly referenced here on Null Byte as the primary tool for copying (or "cloning") code repositories found on GitHub. Git is a must have tool for penetration testers looking to expand their toolset beyond what's available in the default Kali repositories.
Git can be installed using the below apt-get command.
apt-get install git2. Configure Bash Aliases
Bash aliases are fantastic for creating customized command line shortcuts. For example, we can reassign the ls command to automatically use our favorite arguments. Below is an example of a normal ls output.
ls
androidbins.txt folder-pictures.png smtp.cracked text-x-generic.png
bogus_gmail.creds folder.png smtp.list Windows-10
dumpzilla-b3075d1960874ce82ea76a5be9f58602afb61c39 package-x-generic.png text-x-generic.ico 'Windows 10 Icons'Here it is again after creating an ls alias.
ls
total 220K
-rw------- 1 root root 15K Aug 24 2015 folder-pictures.png
-rw------- 1 root root 8.7K Aug 24 2015 folder.png
-rw------- 1 root root 11K Aug 24 2015 package-x-generic.png
-rw------- 1 root root 5.5K Sep 3 2015 text-x-generic.png
drwxr-xr-x 12 root root 4.0K May 31 00:44 'Windows 10 Icons'/
drwxr-xr-x 18 root root 4.0K May 31 00:44 Windows-10/
-rwxr-x--- 1 root root 103K May 31 00:49 text-x-generic.ico*
drwxr-xr-x 5 root root 4.0K Jun 11 21:57 dumpzilla-b3075d1960874ce82ea76a5be9f58602afb61c39/
-rw-r--r-- 1 root root 52 Jul 5 18:13 bogus_gmail.creds
-rw-r--r-- 1 root root 15K Jul 5 18:28 smtp.list
-rw-r--r-- 1 root root 181 Jul 5 18:43 smtp.cracked
-rw-r--r-- 1 root root 23K Jul 23 18:18 androidbins.txt
drwxr-xr-x 5 root root 4.0K Jul 23 19:22 ./
drwxr-xr-x 23 root root 4.0K Aug 9 04:25 ../We're getting a much more verbose output. The ls command is now using the -l, -a, -t, -h, and -r arguments automatically. All of these arguments will instruct ls to use the listing (-l) format, list all (-a) files — including hidden files — and print the file sizes in human-readable (-h) formats (e.g., 1K, 234M, 5G).
My alias will also sort the output by modification time (-t), and reverse (-r) the order of the list so recently modified files appear at the bottom of the terminal. This collection of arguments is my personal ls preference, but yours may be different.
To create aliases, open the /root/.bash_aliases using nano or your favorite text editor. Add the following line to create an alias.
alias ls='ls --color=always -rthla'We can also go a bit further and add more complex functions to the .bash_aliases file. Below is a simple example of a function designed to keep Kali fully up to date.
function apt-updater {
apt-get update &&
apt-get dist-upgrade -Vy &&
apt-get autoremove -y &&
apt-get autoclean &&
apt-get clean &&
reboot
}After saving changes made to the .bash_aliases file, open a new terminal for the changes to take effect. Running the newly created apt-updater function will invoke a series of apt-get commands that will automatically update and maintain your system. The ampersands (&&) ensure that the function doesn't continue to the following command if a prior command fails.
apt-updaterFor more on Bash aliases, check out Kody's "Set Up a MacOS System for Wi-Fi Packet Capturing" article.
3. Create a New Low Privileged User
Many applications like the Chromium Browser and the Tor Browser should never be opened or used as a root user. Such applications rely heavily upon low-level permissions to deliver some degree of security. It might be beneficial to some users to create a low privileged user account for such activities.
This concept is covered in greater detail in Takhion's "Lock Down Kali Linux for Safe Desktop Use" article, so make sure to check that out for help.
4. Install a Terminal Multiplexer
A multiplexer is a tiling terminal emulator that allows us to open several terminal sessions inside one single window. The major benefit to this is being able to see all of our open terminal sessions at once and not layer the windows on top of each other. Below is a multiplexer example.
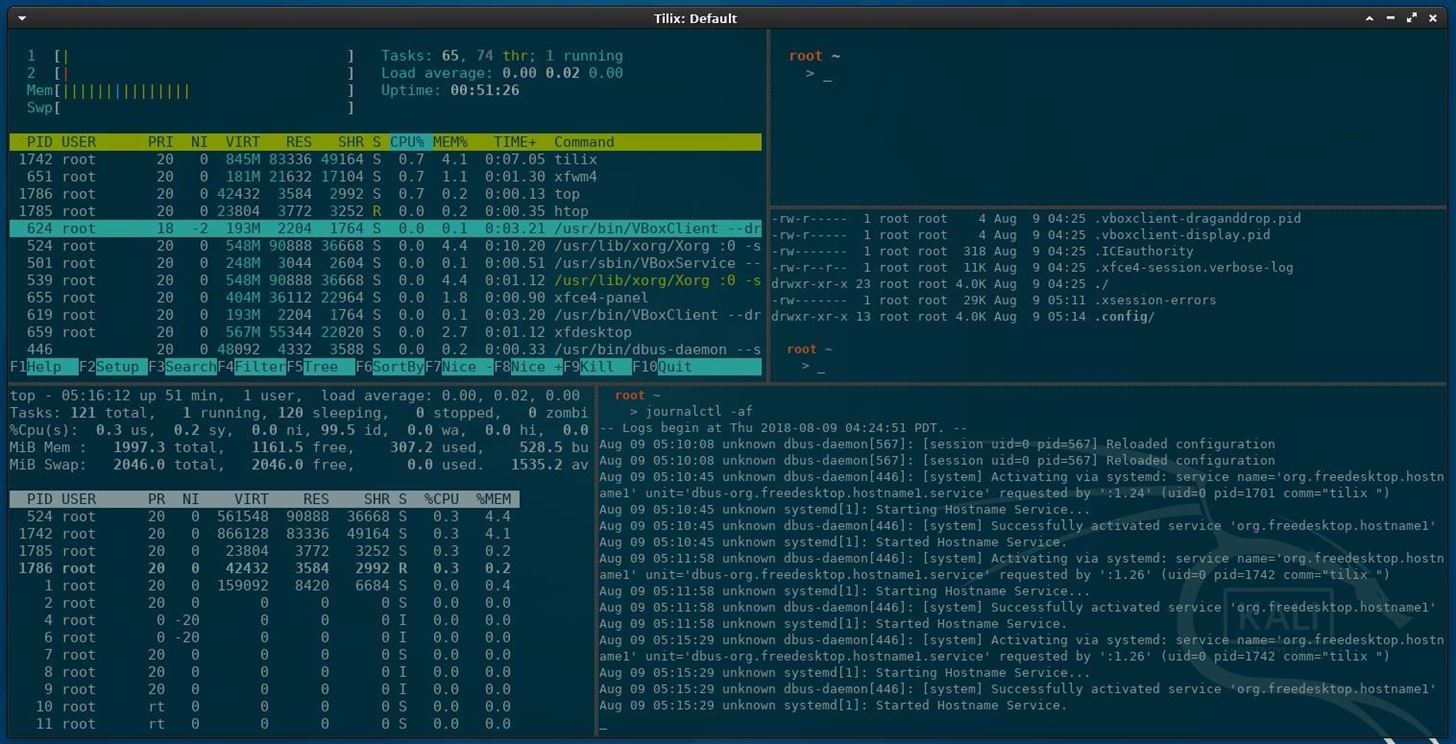
There are many noteworthy multiplexers. Tilix, as seen in the above screenshot, is an open-source and reliable option. Alternatives include tmux and screen.
Tilix is available in Kali's APT repositories and can be installed using the below command.
apt-get install tilix
Reading package lists... Done
Building dependency tree
Reading state information... Done
The following additional packages will be installed:
libgtkd-3-0 libphobos2-ldc-shared78 libvted-3-0 tilix-common
Suggested packages:
python-nautilus
The following NEW packages will be installed:
libgtkd-3-0 libphobos2-ldc-shared78 libvted-3-0 tilix tilix-common
0 upgraded, 5 newly installed, 0 to remove and 466 not upgraded.
Need to get 10.7 MB of archives.
After this operation, 49.1 MB of additional disk space will be used.
Do you want to continue? [Y/n] y5. Install Your Favorite Hacking Tools
Some versions of Kali are geared toward minimalist pentester's who prefer not to have hundreds of hacking tools preinstalled. This means we'll have to install our favorite tools manually. The types of tools we use vary based on our skill set and areas of expertise, but below are some popular hackings tools.
- Aircrack-ng: Wireless WEP/WPA cracking utilities.
- BeEF: Browser exploitation framework via web applications.
- Burp Suite: Graphical application designed for web application security.
- Hydra: Login password brute-forcing utility.
- Nikto: Web server security scanner.
- Maltego: Open-source forensics and intelligence gathering.
- Nmap: Port scanner and network mapper.
- Wireshark: Graphical application for network traffic analysis.
These tools can be installed using the below command.
apt-get install maltego metasploit-framework burpsuite wireshark aircrack-ng hydra nmap beef-xss nikto
Reading package lists... Done
Building dependency tree
Reading state information... Done
hydra is already the newest version (8.6-1kali1).
The following NEW packages will be installed:
beef-xss binfmt-support burpsuite fastjar fonts-droid-fallback fonts-lato
fonts-noto-mono ghostscript gsfonts imagemagick imagemagick-6-common
imagemagick-6.q16 jarwrapper java-wrappers javascript-common libc-ares2
libcupsfilters1 libcupsimage2 libdjvulibre-text libdjvulibre21 libdouble-conversion1
libfftw3-double3 libgmp-dev libgmpxx4ldbl libgs9 libgs9-common libhttp-parser2.8
libijs-0.35 libilmbase23 libjbig2dec0 libjs-jquery libjs-jquery-easing
libjs-jquery-fancybox libjs-jquery-mousewheel libjs-jquery-ui libjs-source-map
libjs-uglify libjxr-tools libjxr0 liblqr-1-0 liblua5.2-0 libmagickcore-6.q16-6
libmagickcore-6.q16-6-extra libmagickwand-6.q16-6 libnetpbm10 libnl-route-3-200
libopenexr23 libpaper-utils libpaper1 libpcre2-16-0 libqt5core5a libqt5dbus5
libqt5gui5 libqt5multimedia5 libqt5multimedia5-plugins libqt5multimediagsttools5
libqt5multimediawidgets5 libqt5network5 libqt5opengl5 libqt5printsupport5 libqt5svg5
libqt5widgets5 libruby2.5 libsbc1 libsmi2ldbl libspandsp2 libssh-gcrypt-4 libuv1
libwhisker2-perl libwireshark-data libwireshark11 libwiretap8 libwmf0.2-7
libwscodecs2 libwsutil9 libxcb-icccm4 libxcb-image0 libxcb-keysyms1 libxcb-randr0
libxcb-render-util0 libxcb-xinerama0 libxcb-xkb1 libxkbcommon-x11-0 libyaml-0-2
maltego netpbm nikto nodejs nodejs-doc openjdk-8-jre openjdk-8-jre-headless
qt5-gtk-platformtheme qttranslations5-l10n rake ruby ruby-addressable ruby-ansi
ruby-atomic ruby-buftok ruby-celluloid ruby-celluloid-io ruby-daemons
ruby-dataobjects ruby-dataobjects-mysql ruby-dataobjects-postgres
ruby-dataobjects-sqlite3 ruby-dev ruby-did-you-mean ruby-diff-lcs ruby-dm-core
ruby-dm-do-adapter ruby-dm-migrations ruby-dm-serializer ruby-dm-sqlite-adapter
ruby-docile ruby-domain-name ruby-em-websocket ruby-equalizer ruby-erubis
ruby-eventmachine ruby-execjs ruby-faraday ruby-geoip ruby-hitimes ruby-http
ruby-http-cookie ruby-http-form-data ruby-http-parser.rb ruby-json ruby-librex
ruby-libv8 ruby-memoizable ruby-mime-types ruby-mime-types-data ruby-minitest
ruby-mojo-magick ruby-msfrpc-client ruby-msgpack ruby-multi-json ruby-multipart-post
ruby-naught ruby-net-telnet ruby-nio4r ruby-oj ruby-parseconfig ruby-power-assert
ruby-public-suffix ruby-qr4r ruby-rack ruby-rack-protection ruby-ref ruby-rqrcode
ruby-rspec-expectations ruby-rspec-support ruby-rubydns ruby-simple-oauth
ruby-simplecov ruby-simplecov-html ruby-sinatra ruby-sqlite3 ruby-term-ansicolor
ruby-test-unit ruby-therubyracer ruby-thread-safe ruby-tilt ruby-timers ruby-tins
ruby-twitter ruby-uglifier ruby-unf ruby-unf-ext ruby-xmlrpc ruby-zip ruby2.5
ruby2.5-dev ruby2.5-doc rubygems-integration thin wireshark wireshark-common
wireshark-qt zip
The following packages will be upgraded:
aircrack-ng libcups2 libnl-3-200 libnl-genl-3-200 libxkbcommon0 metasploit-framework
nmap nmap-common
8 upgraded, 182 newly installed, 0 to remove and 458 not upgraded.
Need to get 381 MB of archives.
After this operation, 616 MB of additional disk space will be used.
Do you want to continue? [Y/n] y6. Install the Latest Version of Tor
Tor is available in Kali's repositories, but anonymity software should be acquired directly from the source (torproject.org). Furthermore, Kali's version of Tor is not reliably maintained or updated. This means we could be missing critical stability and security updates.
Add the Tor Project repositories to your APT repository list.
echo 'deb https://deb.torproject.org/torproject.org stretch main
deb-src https://deb.torproject.org/torproject.org stretch main' > /etc/apt/sources.list.d/tor.listThen, download the Tor Project package signing key and import it into your APT keyring.
wget -O- https://deb.torproject.org/torproject.org/A3C4F0F979CAA22CDBA8F512EE8CBC9E886DDD89.asc | sudo apt-key add -
--2019-02-18 19:28:23-- https://deb.torproject.org/torproject.org/A3C4F0F979CAA22CDBA8F512EE8CBC9E886DDD89.asc
Resolving deb.torproject.org (deb.torproject.org)... 138.201.14.197
Connecting to deb.torproject.org (deb.torproject.org)|138.201.14.197|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 19665 (19K) [text/plain]
Saving to: ‘STDOUT’
- 100%[=================================================================================================>] 19.20K 47.5KB/s in 0.4s
2019-02-18 19:28:25 (47.5 KB/s) - written to stdout [19665/19665]
OKYou'll see the "OK" output when the signing key has been added to your keyring. Next, update APT using the below apt-get command.
apt-get update
Hit:1 http://downloads.metasploit.com/data/releases/metasploit-framework/apt lucid InRelease
Get:2 https://deb.torproject.org/torproject.org stretch InRelease [4,965 B]
Get:4 https://deb.torproject.org/torproject.org stretch/main Sources [1,169 B]
Get:5 https://deb.torproject.org/torproject.org stretch/main amd64 Packages [2,400 B]
Hit:3 http://archive-3.kali.org/kali kali-rolling InRelease
Fetched 8,534 B in 8s (1,091 B/s)
Reading package lists... DoneInstall Tor using the below command, and you're done.
apt-get install tor deb.torproject.org-keyring
Reading package lists... Done
Building dependency tree
Reading state information... Done
Suggested packages:
mixmaster torbrowser-launcher socat tor-arm apparmor-utils obfs4proxy
The following NEW packages will be installed:
deb.torproject.org-keyring
The following packages will be upgraded:
tor7. Configure File Sharing with Syncthing
Syncthing, created by Jakob Borg, is a cross-platform, private, lightweight file-syncing (Dropbox) alternative. As a penetration tester, transferring keystroke logs, screenshots, webcam recordings, and sensitive loot files between virtual private servers and local Kali machines can be a frustrating task. Syncthing makes secure file-sharing totally painless.
I've covered the Syncthing installation and configuration in a previous article. Readers should reference that for a detailed step-by-step guide.
8. Install a Code Editor
Atom is a free, open-source, feature-rich, and highly customizable text editor. Its features include the ability to collaboratively share code in real time, intuitive coding autocompletion, and the ability to install packages which further enhance Atom's versatility. Other noteworthy text editors include Geany and Gedit.
To install Atom, head over to their website and download the latest Debian installer. Next, open a terminal and install the required dependencies using the below apt-get command.
apt-get install gvfs gvfs-common gvfs-daemons gvfs-libs gconf-service gconf2 gconf2-common gvfs-bin psmisc
Reading package lists... Done
Building dependency tree
Reading state information... Done
Correcting dependencies... Done
The following NEW packages will be installed:
gconf-service (3.2.6-4.1)
gconf2 (3.2.6-4.1)
gconf2-common (3.2.6-4.1)
gvfs-bin (1.36.2-1)
libgconf-2-4 (3.2.6-4.1)
psmisc (23.1-1+b1)
The following packages will be upgraded:
gvfs (1.36.1-1 => 1.36.2-1)
gvfs-common (1.36.1-1 => 1.36.2-1)
gvfs-daemons (1.36.1-1 => 1.36.2-1)
gvfs-libs (1.36.1-1 => 1.36.2-1)
4 upgraded, 6 newly installed, 0 to remove and 462 not upgraded.
1 not fully installed or removed.
Need to get 3,317 kB of archives.
After this operation, 8,909 kB of additional disk space will be used.
Do you want to continue? [Y/n] yFinally, use dpkg, a command line package manager, with the install (-i) argument.
dpkg -i ~/Downloads/atom-amd64.deb
(Reading database ... 191882 files and directories currently installed.)
Preparing to unpack atom-amd64.deb ...
Unpacking atom (1.29.0) over (1.29.0) ...
Setting up atom (1.29.0) ...
Processing triggers for desktop-file-utils (0.23-3) ...
Processing triggers for mime-support (3.60) ...When that's done, Atom will be available in your Applications menu.
9. Clone Rubber Ducky Encoder
The USB Rubber Ducky is the notorious keystroke injection tool. Creating ducky payloads is easy using the DuckToolKit website, but as a penetration tester, it's unsafe to share client information with random websites. Uploading payload contents to a third-party website can be dangerous.
Instead, we can use Git to clone the USB Rubber Ducky repository and encode payloads locally.
git clone https://github.com/hak5darren/USB-Rubber-Ducky
Cloning into 'USB-Rubber-Ducky'...
remote: Counting objects: 1657, done.
remote: Total 1657 (delta 0), reused 0 (delta 0), pack-reused 1657
Receiving objects: 100% (1657/1657), 31.88 MiB | 162.00 KiB/s, done.
Resolving deltas: 100% (745/745), done.
Checking out files: 100% (1509/1509), done.Then, change (cd) into the USB-Rubber-Ducky/Encoder/ directory and use the following java command to start encoding ducky payloads without third-party websites.
cd USB-Rubber-Ducky/Encoder/
java -jar encoder.jar -i input_payload.txt -o inject.bin10. Change SSH Keys & Default Password
The default password for every Kali Linux installation is the same (toor) which makes it very easy to automate attacks. Also, the default SSH keys can allow an attacker to intercept your communications when you're controlling something like a Raspberry Pi via SSH.
To change the SSH keys, first, change into the directory. Doing the below two commands will reset the SSH keys from the default ones.
cd /etc/ssh/
dpkg-reconfigure openssh-server
rescue-ssh.target is a disabled or a static unit, not starting it.Now, for your Kali system's password, enter passwd root, then enter in your new password. Afterward, retype it to confirm. If you're not logged in as root, you may be asked for your current password before doing this.
passwd root
Enter new UNIX password:
Retype new UNIX password:
passwd: password updated successfullyWhat's the First Thing You Do After Installing Kali?
We all have varying degrees of interests, skill sets, and levels of experience. Which makes compiling a well-rounded list of post-installation steps tricky. Did I miss any critical steps? How do you personalize and customize new Kali installations? Be sure to leave a comment below.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















28 Comments
It had to do with a legal issue: Firefox is too closely associated with commercial code to satisfy Debian's administrators–they hesitated to incorporate undesired changes to Firefox, Debian thus was forced by Mozilla to change the names of Firefox, Thunderbird, and Seamonkey. (See Wikipedia: "Mozilla Corporation software rebranded by the Debian project." Debian is more slow and deliberate concerning changes to the distro.)
For one thing, changing the name to Iceweasel prohibits users from querying Debian developers concerning changes to Firefox. Upon running Iceweasel, "Firefox" and "mozilla" do turn up in error messages, etc., nonetheless.
Such an animal actually does exist: It appears to be similar to a small, white fox.
I just change the wallpaper. ;)
Anyways, is there any possibility another post can be done about how to create your own custom Kali OS using the Kali Live Scripts? Just a thought.
Many thanks for this excellent article. I did have some problems which I'll pass on.
I'll proceed with your other 'How tos' and see how I go. I'm using Linux Mint 18.3 as my base as I don't want to install Kali on my laptop.
You're attempting to follow along with these Kali tutorials using Linux Mint? Kali is based on Debian, which isn't Mint/Ubuntu. You will continue to experience many issue as you follow along. I recommend installing Kali in Virtualbox, on a USB, or on a Raspberry Pi. There are guides for all of these on Null Byte.
Please give me the json for the tilix colors u are using.
I would add that after installing with full encryption, to set up the nuke option and make an encrypted header backup (put in a safe place or 2).
Hey so quick question ,
on 6.Install the Latest Version of Tor
on the part when you paste the "signing key"
and it gets to
"HTTP request sent ,awaiting response...(i get) 408 request timeout."
I'm not sure what I'm doing wrong if you could please help me out that would be great. thx
Looks like MIT's PGP server is behaving unusually. The key can be acquired directly from the torproject now:
This article isn't strictly for Kali Linux on RPi3B+, correct? I like using Atom on my mac, however, Atom doesn't support ARM systems, or to my knowledge. That is unless you have a work-around.
You do realize Mac is merely a fancy window manager running on top of a special version of FreeBSD right?
hello there,
according to stage 2 about configure bash alias...i have a problem attempt to write the command hackwifi as shown at the explain video of null byte. the output that i get after write (at a new terminal window) is:
"root@kali:~# hackwifi
nl80211 not found.
Interface wlan0:
ioctl(SIOCGIFINDEX) failed: No such device
besside-ng: wi_open(): No such device
root@kali:~# "
someone can help me please?
You have to have an RF (WiFi card or dongle) device
When creating new sshd keys ensure they are actually recreated, if they do not have current date then most likely they did not. I took a look here forums.kali.org/showthread.php?5723-Change-your-Kali-default-ssh-keys and basically one step that was done extra was move old keys to different folder, then it recreated keys.
root@kali:/etc/ssh# dpkg-reconfigure openssh-server
Creating SSH2 RSA key; this may take some time ...
3072 SHA256:xxxxxxxxxxxxxxxxllaouarere root@kali (RSA)
Creating SSH2 ECDSA key; this may take some time ...
256 SHA256:xdaalalfjlaflafjalfjalf root@kali (ECDSA)
Creating SSH2 ED25519 key; this may take some time ...
256 SHA256:lajlfajflajflajflajflafjalfjalfjaljlaf root@kali (ED25519)
rescue-ssh.target is a disabled or a static unit, not starting it.
error:
root@kali:~# apt-get install tor-geoipdb
Reading package lists... Done
Building dependency tree
Reading state information... Done
Some packages could not be installed. This may mean that you have
requested an impossible situation or if you are using the unstable
distribution that some required packages have not yet been created
or been moved out of Incoming.
The following information may help to resolve the situation:
The following packages have unmet dependencies:
tor-geoipdb : Depends: tor (>= 0.4.1.6-1~d9.stretch+1) but it is not going to be installed
E: Unable to correct problems, you have held broken packages.
Hey community,
I walked through this tutorial but had some issues with some installations. Could someone help me figure out what I need to do to get these messages resolved?
"dpkg: error processing archive /root/Downloads/atom-amd64.deb (--install):
package architecture (amd64) does not match system (arm64)
Errors were encountered while processing:
/root/Downloads/atom-amd64.deb"
Thanks!
Hey there Mitch,
Well the error message of your atom installation is quite clear: This software was created for systems which use the amd64 architecture, but your system is using arm64. So the version of atom you downloaded is not compatible with your system architecture --> it does not run. I heard there are workarounds, but since it did not affect me personally I didn't dive too deep into the topic and I really doubt there is something reliable out there. There is a visual studio code port for arm64 though so I could recommend that. VS Code is also highly customizable (idk if it has less features on arm64) and could suit your purposes. You can check it out and let me know if it works/ is something for you :)
I hope I could help at least a little bit
i need a little bit help
if i close the terminal, is there any way to retrieve it?
and.... is it going to close or destroy the processes which was running on it
i swear to christ, i have reinstalled Kali Linux at LEAST 15 times, and ive tried EVERY DAMN tutorial i have found on google on how to fix the "update" issue. i just cant make any headway here. Have any of you had this problem? after flashing kali to SD, and running it, try to "update & Upgrade" then screen goes blank, curser flashes and its not really functional ... can somebody please helppppp meeee!!!
First off. Uninstall Kali. Problem 1. Solved. It is a garbage distro. Use Debian base. Put it together yourself. I know, its alot of work. So is installing a bunch of times. Kali is nice in concept but really its not very good. Even Kali devs recommend you don't use it. Unless I am greatly mistaken, Every piece of software on kali is found in other debian repos. I know that most are. Also a big theme of this article is getting software not from kali as its usually poorly maintained. They, kali, have a great website full of things to install on a better distro. Just don't get it from them. If you got Debian your good, I am sure. You could probably find similar for others like arch, and perhaps better maintained. Kali is a fad because its a good idea. But I have even tried it and its junkware. Make life easy on yourself and install MX and start hunting the packages. Or base Debian if you want to work a little for it.
you should use gparted to re-partition you sd card before you do apt-get upgrade since this will cause issues because of insufficient space for the updates.
Step 1: Install Gparted
apt-get install gparted
Step 2: Run Gparted
gparted
Step 3: Resize Partition
select your ext4 partition and click "Resize/Move" button move slider all the way to the right your "free space following (MiB):" should be 0. Then you click the "Resize" button and the "Apply" button.
AND
For anyone with a slower-than-desired network connection, you may want to disable the auto-sleep/shutdown timers in Kali, cause the apt-get upgrade can take a long time over a crappy wi-fi connection, and mine crashed the first time cause Kali is set to turn itself off after 15 minutes of no-contact.
This is super easy to do from the GUI in Kali, go to:
Applications (Top left) > Settings > Power Manager > System (tab - set the "When inactive for" slider to "Never") > Display (tab - Set all sliders to "Never") > Security (tab - Set it to Never automatically lock the session).
I'm unable to install 'tor'as you directed in the article.
I installed rubberducky in my kalilinux android
But after opening it is saying bash:java:command not found
Help me anyone plzzzzzzzzzzzzzzz
Java isn't installed. Might be a problem with using it on android. Is it trying to run a script?
Please help i tried to install tor as shown on the video.
Now i whana launch it but when i type tor on the terminal this comes up.
I can't open tor.
I am facing the same problem!
=> Just tell me what is this error and how to solve it ?
Hello everybody! I'm trying to setup my Kali distro on VMware Workstation 16 Pro but i've an error occuring while the installation of USB Rubber Ducky...
I've an issue occuring while i'm trying to encode my payload locally. I've this traceback so if someone can help me out with this problem please? The message appearing in the STDout is:
root@kali:/home/naga/USB-Rubber-Ducky/Encoder# java -jar encoder.jar -i input_payload.txt -o inject.bin
Hak5 Duck Encoder 2.6.4
Error with input file!
Exception in thread "main" java.lang.NullPointerException
at Encoder.main(Encoder.java:127
PS: Thank you very much by advance for your help guyz/girlz! I'll highly appreciate your help. Maybe another time i'll be able to help ya in return... Who knows lol! Thanks! ^_*
Quick question if anybody can shed some light. Using VirtualBox - installed iso from kali site verified. Tried the Live, The ova, and finally the full distro. Upon firing up I get the Kali screen choose Kali and then get screen black - flashing cursor - no CMD Line? Any Ideas
Sorry, forgot Linux MInt 19.3 Tricia
VirtualBox Graphical User Interface Version 5.2.42_Ubuntu r137960
Share Your Thoughts