Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.
In previous guides on phishing, one of the most common questions has been about how easy it would be to adapt the default page to look like a particular login. SocialFish can clone a social media website to create a password-harvesting attack link in only a few clicks, eliminating the need to create such a template yourself. While there is also a previous version of SocialFish that featured Ngrok integration, we'll be taking a look at the new version.
The Next Generation of SocialFish
While the previous versions of SocialFish were impressive, the latest update includes a clean web interface to create and manage phishing links. The shift to web-based interfaces for tools like Kismet has helped to make SocialFish more accessible to beginners, and the refined simplicity makes cloning nearly any website incredibly simple.
One downside to the new SocialFish is that the documentation is sparse or nonexistent for many features. That means that many of the features like the attached Android application are not simple to use, and troubleshooting can be difficult as the Wiki contains a minimal amount of information.
- Don't Miss: How to Clone Any Website Using HTTrack
Still, as a bleeding-edge tool with a straightforward interface and well-thought-out controls, SocialFish is an easy way to demonstrate how simple customized phishing links are to make. One important note for this article is that, due to the potential for misuse and sketchy documentation, we'll only be deploying this link on our internal network, not to a target on the external internet.
What You'll Need
To use SocialFish, you'll need to have Python3 or higher installed on your computer. You'll also need PIP3, Python3's package manager, installed as well. In addition, several libraries are required for this tool to run. We'll cover installing them in the next steps, but keep in mind this can take quite some time to download and set up over a slow network.
Step 1: Download SocialFish
To start using SocialFish, we can check out the GitHub repository for information on previous versions and the mobile app that goes with the primary tool. Getting it running requires quite a few dependencies to be installed, so on a good internet connection, we can install everything with a few lines in a terminal window.
In a new terminal window, type the following commands to install the necessary dependencies, clone the repository, and run the set-up script.
~$ sudo apt-get install python3 python3-pip python3-dev -y
~$ git clone https://github.com/UndeadSec/SocialFish.git
~$ cd SocialFish
~$ python3 -m pip install -r requirements.txtOnce it is finished running, you should be ready to use SocialFish. We'll be using our browser to interact with it, so open a FireFox window before proceeding to the next step.
Step 2: Log in to the Web Interface
Now, let's create a web interface that will help manage our phishing links. To do this, open a terminal window and type the following to change into the SocialFish folder. Pick a username and password to log in to the web interface, and substitute that for the "youruser" and "yourpassword" fields.
~$ cd SocialFish
~$ python3 SocialFish.py youruser yourpasswordOnce it's finished setting up, we should be able to access the web interface by navigating to the URL 0.0.0.0:5000 in our browser. Enter the username and password you set up, and click "Login" to access the SocialFish portal.
Step 3: Select the Target to Clone
Inside the SocialFish portal, we can see some important information. At the top, we see the field for the website we want to clone, the website we want to redirect to, and the URL for our attack.
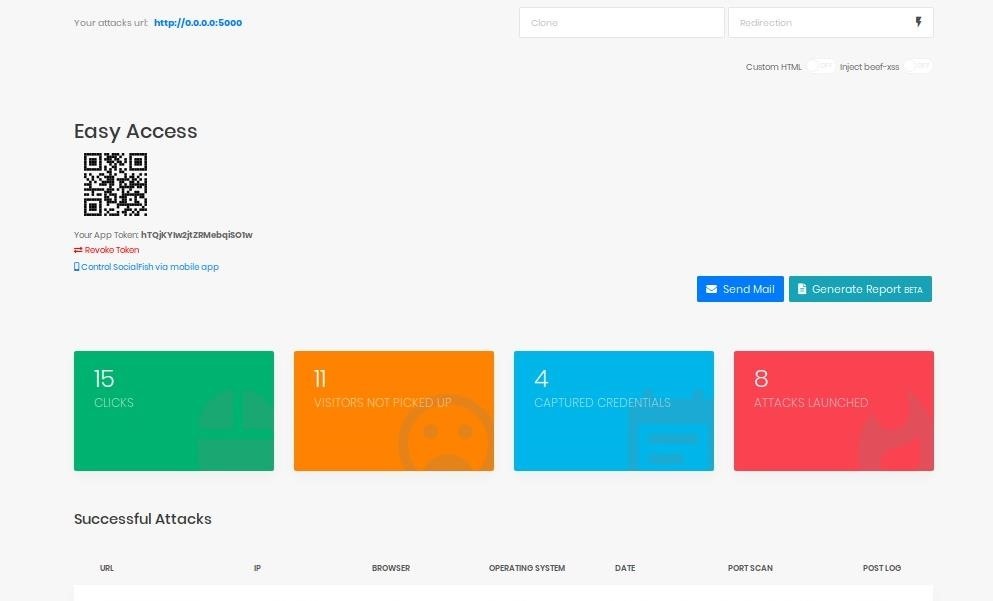
We can also see some information about links we've already created. In my case, I've already created eight attack links, which have attracted 15 clicks and four sets of captured credentials.
Step 4: Select the Redirect Link
For our attack, we'll need to decide what website we want to clone. In this case, we'll pick twitter.com/login. To make things simple, we'll redirect back to twitter.com afterward. If they are already logged in, it will just look like a normal login was successful.
Enter the URL you want to clone and the URL you want to redirect to into their respective fields on the top right of the page. Click the lightning bolt to activate the link.
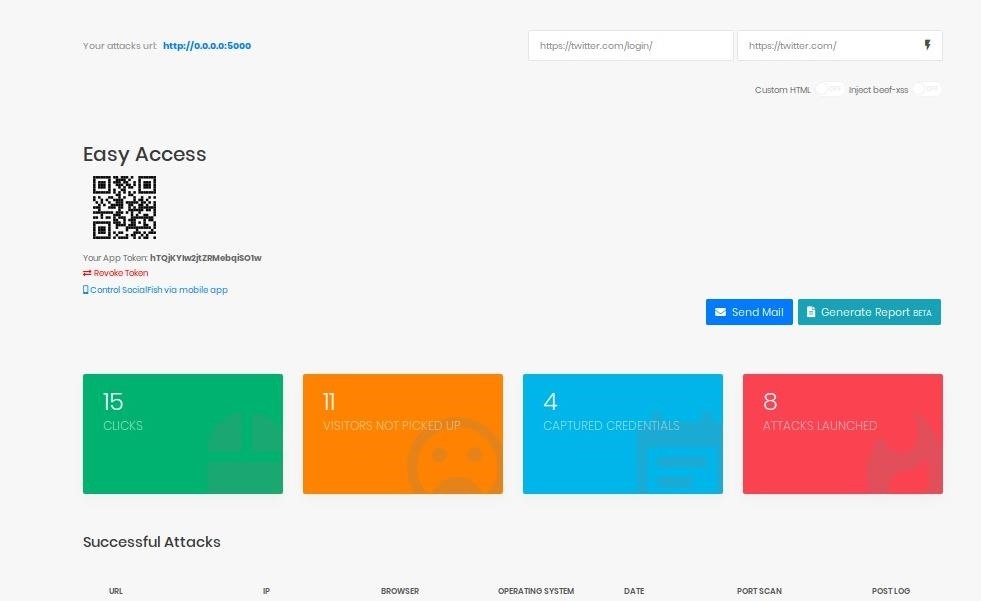
Step 5: Deploy the Phishing Link
Now, in a separate browser window, navigate to the attack link — the link we would be serving to the victim during a real attack. You will be directed to a real-looking phishing site, and you can enter a username and password to test it.
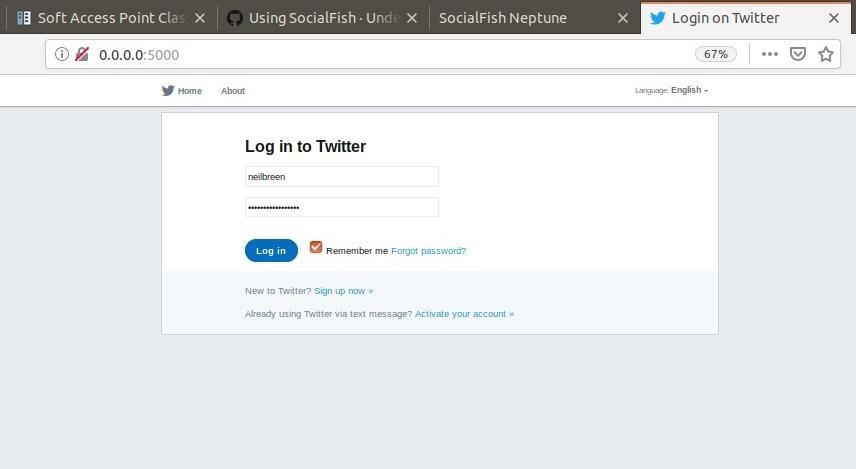
During a live deployment, you would need to redirect the target to this URL. The current documentation is sketchy on this, and I'm also leaving it out as to reduce the risk of malicious use of this script. For now, we can access it on our internal network.
- Don't Miss: Automating Wi-Fi Hacking with Besside-ng
Once we enter our test credentials, we should be redirected to the link we specified. Now that we've captured some credentials let's explore how SocialFish logs them.
Step 6: Analyze the Captured Credentials
Back on the main menu, we can see that the number of captured credentials has gone up. We can also see that listed under "Successful Attacks" are a number of logs we can access.
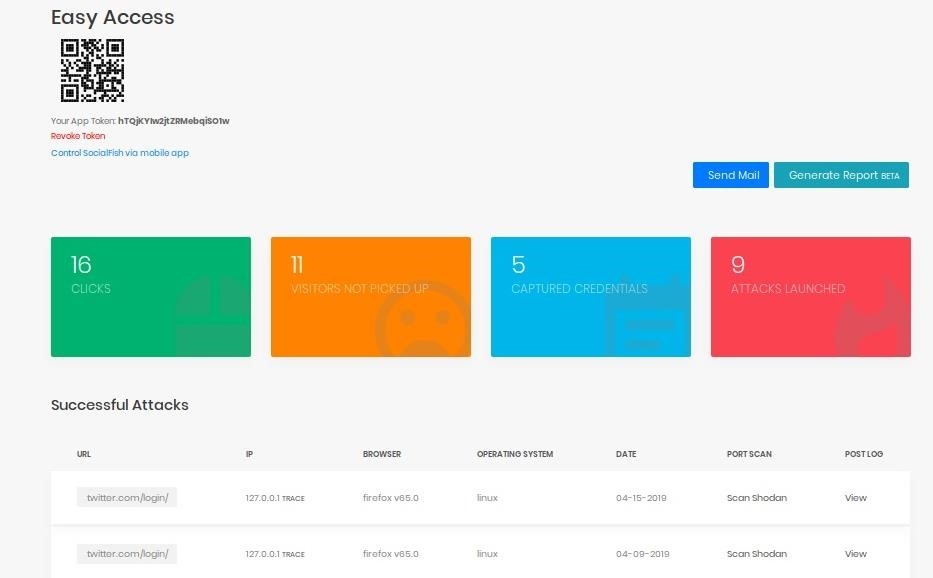
Click "View" on the most recent log to see the credentials we intercepted. It should open a page that dumps the collected information in a format like below.
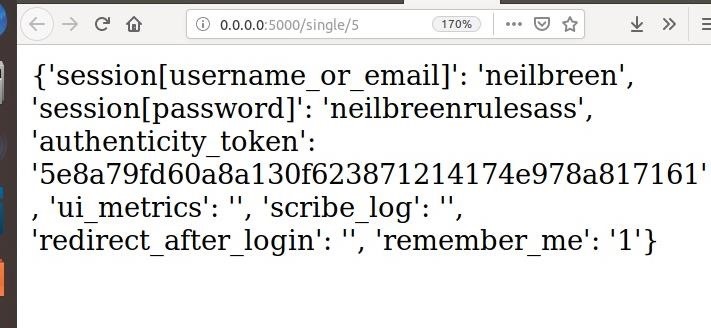
That was easy! With only a couple of clicks, we were able to create a website that looks virtually identical to the real Twitter.com. As soon as we entered our credentials, SocialFish captured them and saved them to an interactive log, allowing us to manage phishing campaigns easily.
SocialFish Makes Phishing Easy
Though SocialFish has gone through many iterations, it continues to be a powerful tool for creating convincing phishing pages for social media websites. We haven't gone into how to deploy SocialFish across a network in this article, but as you can see in our example, the hardest part of creating a convincing fake on the fly is actually easy to do. One limitation of SocialFish as a tool is its current lack of documentation, but in the future, I expect this to improve to make the companion mobile app more useful.
I hope you enjoyed this guide to phishing social media websites! If you have any questions about this tutorial on phishing social media, leave a comment below, and feel free to reach me on Twitter @KodyKinzie.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























14 Comments
Do the client have to be near us so we can fish them
if they don't then everyone in the world shares the same url 0.0.0.0:5000 then everyone will see the data that someone else fish
You got to be on the same network and you have to use DNS spoofing to redirect the domain name to the adress you used.
thank you, but I am a new to internet can you explain what DNS spoofing is?
what is the problem here?
At the end of that url put /neptune
ex: 0.0.0.0:5000/neptune
DNS (Domain Name Service) is a service for connecting an IP adress like 192.168.1.1 to a certain domain. So instead of typing the IP adress you can type the URL an you get directed to the IP adress of the website/webservice. And dns spoofing is just dns but abusing it for your purposes. With dns spoofing you can direct people on your network to the site you want. So if someone types in thit url of wikipedia you could direct them to facebook instead. From that on its your fantasy, what yo can do with this.
how to hack watsapp.
That's a pretty broad ask did you have something in particular in mind? Or have a particular attack for us to cover?
It is only working in same browser when entering same url (http://0.0.0.0:5000/) in any other device or any other browser than this is showing
I am facing this problem while write command python3 - m pip install - r requirements. txt
give me solution
I'm having this issue where the attack link doesn't show the proper cloning page. I followed each step exactly as shown, everything was working until then, and I clicked the little lightning bolt to apply the links. I don't know how to fix it
have you installed python3 and pip on termux?
It's probably cause you're using Userland/Termux, it doesn't normally work the best with network related things
will this phishing site will be always open like an website (000webhosting like phishing) or it will end once i disconnect from socialfish>??
Share Your Thoughts