.. The domains, ... usually deliver a lot of information and sometimes more than due. When it comes to services, domains, websites and more, often escape details such as the configurations in DNS servers , so we will see what is the zone transfer to DNS and how this can expose information and infrastructures
... DNS servers are basically computers that are responsible for resolving domain names to IP addresses. This allows users to access services in a user-friendly way, since remembering IP addresses would be more complex.
However, they are often used by attackers to collect information about the infrastructure and subdomains of the potential victim - although there are automated tools for doing so, such as Dnsnum . From the latter we see a screenshot below:
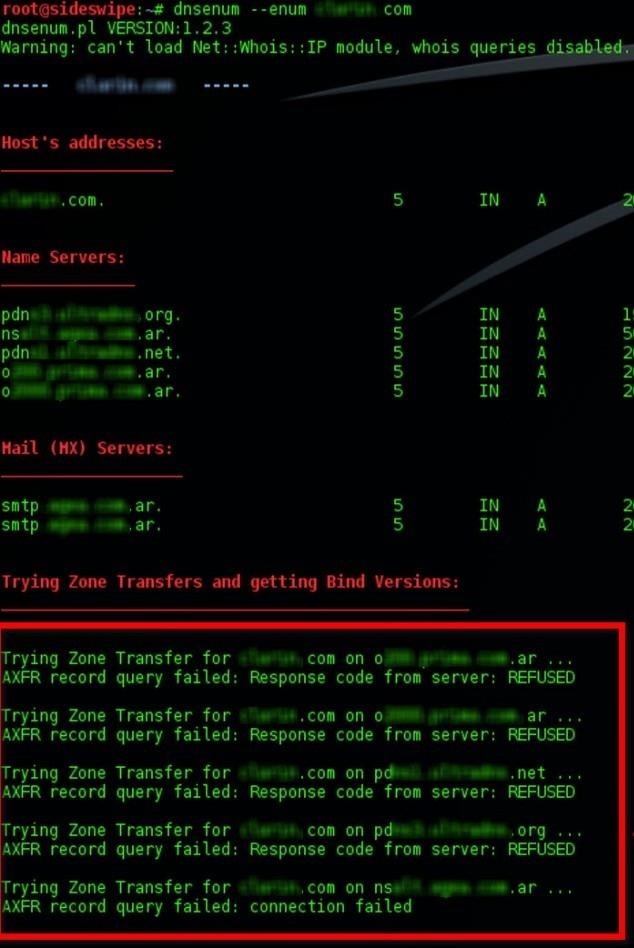
You can clearly see how just by giving you a few parameters (in this case - in order to list the information) already starts with gathering information, not only from DNS servers but also doing Internet searches. While he does everything on his own by simply telling him the domain, he must understand how it works from behind.
To obtain this type of information you can use the dig command in the systemsLinux and OS X ; is a tool for querying DNS servers , as we will see below:
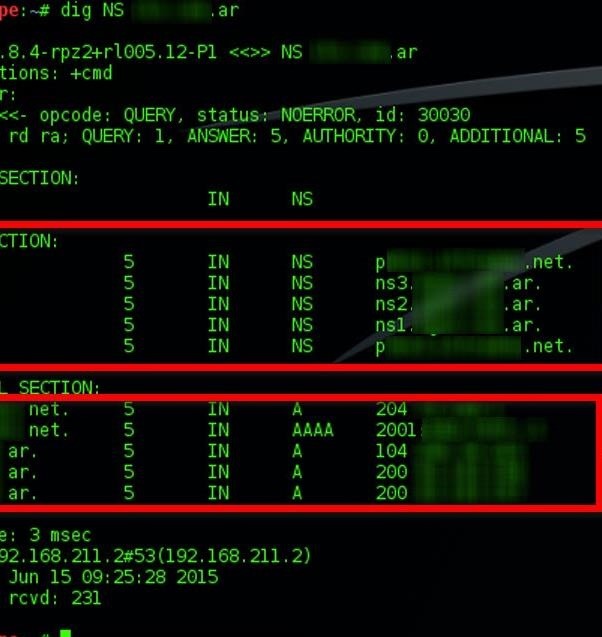
We see that when the query, automatically the DNS servers that are responsible for resolving the queries are listed. To do this, use the following command:
Code: Bash
dig NS mydomain.net
Once the command is executed in a Linux environment , it will display the list of the corresponding servers responding to requests for that domain.
Why would an attacker want to perform zone transfer and collection records from DNS servers?
It happens that through them you get to collect information from a corporate network , sometimes exposing their internal IP addresses, servers and computers. To collect this information, use the parameter "axfr" (this type of attack is also called AXFR) where the command is as follows:
Code: Bash
dig @ ns1.mydomain.net axfr mydomain.net
The parameter "axfr" is the one that allows the zone transfer of said DNS , since it is used to synchronize and to update data of the zone when changes occurred. Although the transfer can be done via"axfr" , it is also possible to do it incrementally, then called "ixfr" - when the request is executed the transfer of the entire zone is obtained as a response. Without proper configuration, this allows an attacker to replicate the DNS database , obtaining sensitive information.
Once this is done, if the attack is successful, you can see how much information is exposed, as we will see in the following screenshot
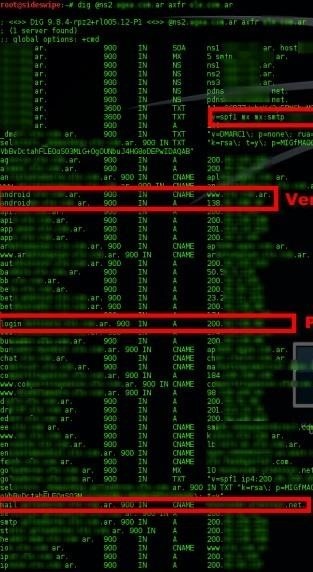
It can be seen in the example shown that IP addresses are listed, services that are surely of internal use as login portals, mail services and even the portals available for the mobile versions.
How can I view this information from Windows?
In the same way that we can obtain this information with the command dig from Linux systems, we can also obtain this information from Windows systems with Nslookup . Let's see in the following screenshot how to do it:
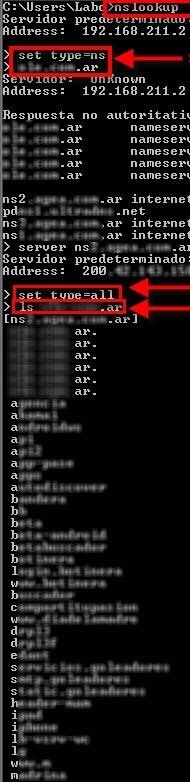
Although from Windows change the commands and parameters a little, it can be done in the same way. First it is necessary to open the Windows console (it is also possible to use console here); to do it just write"Cmd" in the search bar in the Start menu and press the Enter key.
Once the console is opened, as shown in our previous example, you can start the script:
1- The first to execute is nslookup followed by the Enter key; this initiates the tool to make queries to DNS servers
2- The second one is: set type = ns (here it is specified that the type of query in this case Name Server); once pressed enter, in the following line should be placed the domain to consult, for example com.ar
3- The third one to execute is: set type = all followed by the Enter key (this specifies that all possible queries are performed)
4- The fourth and last is: ls example.com.ar , which will be responsible for listing the available information.
So what do we do to prevent the leakage of this kind of information?
It is very important to understand that all this information could be exploited by a cybercriminal to compromise a complete computer or network. Knowing this in advance, we have the tools to carry out the proactive analysis for its prevention.
To avoid these headaches of information leakage, from the Research Laboratory of ESET Latin America we recommend to review the configuration files on the DNS servers.
It should be noted that depending on the software being used for this service, will be where its configuration file is located to allow or deny the equipment or authorized to perform such transfer.
For example, to solve this problem in bind9 , you must access the named.conf.local file (located by default in / etc / bind) and edit it, in order to support zone transfer only to IP addresses of secondary DNS servers of trust. To do this you must modify the file as follows:
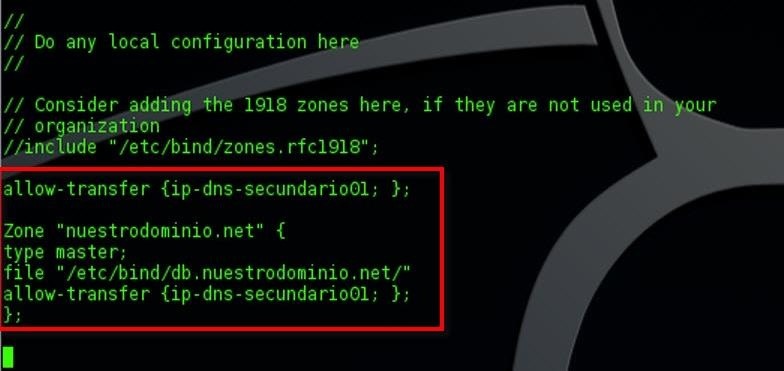
It is important to keep in mind that this file can vary its configuration and location depending on which softwareis used. We recommend to understand how the one that is being used works and to make the corresponding configuration.
As we have seen, something that may seem so simple represents a serious security risk. We saw how using tools of the operating system, in conjunction with bad configurations on the other side, we managed to collect a lot of sensitive information.
Through the information obtained, the attacker can understand the topology of the network and in this way try to violate it. Therefore, it is necessary to work proactively to detect these types of situations and correct them, before it is exploited by an attacker. Applying the necessary corrections to these problems proactively we can use the technology safely and without so many worries.
-welivesecurity









































Be the First to Respond
Share Your Thoughts