My question has 2 parts:
I used sqlmap to get an operating system shell on an old windows xp running Windows SQL Server 2005. I escalated privileges and granted myself full read, write, execute in all folders under C. So running --os-pwn shouldn't be a problem, but I can't get it to work.
I'm thinking it's because my port forwarding. Port forwarding won't work when I am running private internet access to hide my identity. So I decided to install ngrok as a way to port forward. Ngrok sets up a secure tunnel to localhost to expose my local server behind NAT.
Using the operating system shell I've established using sqlmap, I ran a command to list all the connections and ports that were being used. I find dozen of connections between myself and my target. I used port 6996, for example when I was trying to establish a connection with metasploit yesterday but on metasploit it said it failed, but look:
AND LOOK AT ALL THESE CONNECTIONS!! They're all from me!
So how do I access them? I don't get it. Do I use netcat to get the connection or what? When I run netcat nothing happens. I'm really confused and just don't understand how reverse connections and all that stuff works. Can someone please help?? Thanks!!
Secondly after dicking around with the configuration I've been able to create 8 sessions on my target but each closes immediately. How come?? How do I get it to stay open?
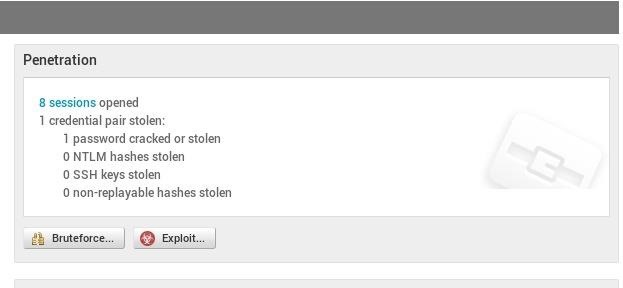
Thanks for anyone who can help! xoxo








































Be the First to Respond
Share Your Thoughts