There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.
It's puzzling to imagine about 100,000 .onion websites in existence. Readers who use Tor daily might think this number is inaccurate or exaggerated, but it's important to remember that the Tor network isn't comprised solely of HTTP web servers.
There are tens of thousands of SSH, FTP, SMTP, Bitcoin, XMPP, Ricochet, and IRC servers using onions for anonymity or convenience. The majority of these servers are password-protected or not publicly disclosed, therefore can't be accessed by all.
We also have to take into account the estimated two million users accessing Tor every day. If just five percent of Tor users created an .onion service in the last 24 hours, that's over 100,000 unique onion addresses. Suddenly, 100,000 .onion services doesn't seem unrealistic anymore.
Who Is Using Tor?
Tor has been endorsed by the EFF, The Guardian, Forbes, and Gizmodo, and Null Byte frequently encourages it for browsing or hosting. The misconception that Tor is only used by criminals is completely false. So who are these two million users accessing the Tor network every day? According to Tor:
- Normal people. The two most common reasons regular people use Tor is to circumvent censorship and broad mass surveillance. World news, culture, health issues, religions, and other types of information can be locked behind a national firewall that Tor can break through. Also, internet service providers (ISPs) sell our browsing records to marketers or anyone willing to pay for it, and Tor can help prevent that.
- Journalists and their audience. "Tor is part of SecureDrop, an open-source whistleblower submission system that media organizations can use to securely accept documents from and communicate with anonymous sources. Many reputable news organizations use SecureDrop."
- Law enforcement officers. Tor allows law officers to engage in online "undercover" operations to catch drug dealers, hackers, and criminals. It also makes it possible to accept tips more anonymously about criminal actions.
- Activists and whistleblowers. "Human rights activists use Tor to anonymously report abuses from danger zones. Internationally, labor rights workers use Tor and other forms of online and offline anonymity to organize workers in accordance with the Universal Declaration of Human Rights. Even though they are within the law, it does not mean they are safe. Tor provides the ability to avoid persecution while still raising a voice."
I'll be talking about a handful of .onion web servers that are publicly accessible. Some of the featured sites are also available as normal (clearnet) sites and accessible without the Tor network. My goal when compiling this list wasn't to scour the darknet for the strangest, scariest, and most unusual websites online, but rather to find the most useful and practical .onions that users can actually utilize on a day-to-day basis to improve their anonymity in this age of mass surveillance.
Disclaimer: No website featured in this article has been verified as legitimate. Users should proceed with caution when viewing any website or download anything on the internet. Furthermore, these are not endorsements for any particular .onion website or service. All websites were discovered via the open internet and various .onion directories.
1. Tor Network Search Engines (6)
There are many search engines that allow users to search for content in the Tor network. Much like Google, these search engines index other .onion websites and add them to a private database.
- Candle: A minimalist .onion service search engine without support for parentheses, Boolean operators, or quotes; You just use words and that's it.
- Grams: Searches markets only for labor, digital, and physical items you can purchase with Bitcoin and other currencies.
- Haystack: Searches .onion services and claims to have 1.5 billion pages indexed in its database from 260,000 websites (which includes .onion websites that no longer exist).
- Not Evil: Search engine with an index of over 32 million .onion links.
- Torch: Search engine with 450,000 indexed .onion services.
- Tor Onionland: Search engine with over 57,000 .onion websites discovered and nearly 5 million indexed pages.
2. Internet Search Engines (3)
Google's collection and aggregation of user data through the various tools (Google Analytics, Google Fonts, etc.) enable's them to determine a user's route through the internet by tracking IP addresses and cookies (cross-domain tracking). However, there are several privacy-focused search engines available that allow users to query the web anonymously without linking searches to their Google account or identity.
Below are just some example .onion clearnet search engines that allow users to anonymously find resources on the internet.
- DuckDuckGo: A Google-like internet search engine dedicated to protecting user privacy.
- SearX: A highly customizable, meta-search engine. This means it queries dozens of other search engines simultaneously to produce the best possible results. There are over one hundred available search engines available to Searx including DuckDuckGo, Bing, and StartPage. Best of all, Searx supports operators (aka "Google Dorks") for advanced search queries.
- TPB: An index of digital content of software and media. TPB allows visitors to search and download content at no cost.

3. Security & Privacy (8)
These resources provide helpful guides for protecting ourselves from electronic surveillance. Many of the guides will be useful to people with little technical knowledge, while other resources are aimed at audiences with considerable technical expertise with privacy and security concepts. Some of these .onions provide useful information for evading surveillance and improving operational security (OPSEC).
- GnuPG: Also known as GPG, this allows users to cryptographically sign and encrypt data and communications. The GnuPG website providers excellent documentation and how-to tutorials.
- OnionShare: An open-source tool that allows users securely and anonymously share a file of any size using the Tor network.
- OpenPGPKeysever: A PGP keyserver that will enable users to anonymously acquire keys for secure communications as well as download verifications.
- Privacy International: A London-based charity that challenges government powers by advocating for strong digital protections and human rights.
- Security in a Box: Offers how-to instructionals to help users install and use the essential digital security software and services.
- SKS OpenPGP: Another PGP keyserver that allows users to anonymously acquire keys for secure communications as well as download verification.
- TorProject: A network of volunteer-operated servers that helps organizations and individuals to share information anonymously.
- Whonix: An .onion where users can interact with developers and other members of the privacy community via its forum. It also hosts a lot of OPSEC guides.
4. Pastebins (6)
Pastebin's are useful for publicly (or privately) sharing code and data with friends and colleagues. Unlike pastebin.com, most pastebins found in the Tor network automatically delete pastes after several weeks.
- DeepPaste: A simple pastebin that offers self-destructing pastes and claims never to delete or censor them.
- Felixxx: Little is known about Felixxx, but it's another option you can use.
- Riseup Paste: Pastes are automatically deleted within a week and cannot exceed 50 MB in size.
- Pasta: An open-source pastebin with a 10 MB upload size limit and self-destructing features.
- Stronghold Paste: Created by Sayak Banerjee, an open-source pastebin web application and among the most popular and longstanding .onion pastebins.
- ZeroBin: A minimalist, open-source pastebin. Pastes are encrypted on the ZeroBin servers so the systems administrators cannot read your content.
5. News (4)
Internet access is highly restricted in certain countries, so the ability to access news outlets can be extremely difficult for some.
- Dark Web News: A resource for dark web news, anonymity tools, and .onion links.
- Deepdotweb: Primarily dark web news related to arrests of criminals abusing Tor resources.
- The New York Times: This news site made headlines in October 2017 when they announced nytimes.com would be available as a Tor .onion service.
- Propublica: A nonprofit and independent collective of journalists that covers a range of topics such as technology, government, business, criminal justice, the environment, and immigration.
6. Email (7)
There are several reasons why people might want to access their email over Tor. Routing traffic through the Tor network makes it difficult for an adversary wiretapping internet connections to know what you're doing online. Tor also hides your true IP address and location from the email provider itself.
- Confidant: An open-source, spam-resistant alternative to regular email. Email messages are stored encrypted so the Confidant administrators cannot access any message contents.
- Daniel Email: A free and anonymous email provider that allows up to 25 MB of email storage on their servers.
- Elude: User accounts feature encrypted storage of email messages with a web client only accessible using the Tor network.
- GuerrillaMail: A free, anti-spam, disposable email address service.
- Mailpile: A modern web client with integrated PGP encryption features that makes securing email communications simpler.
- ProtonMail: An open-source and easy-to-use email client with a modern web interface. All emails between ProtonMail clients are automatically encrypted.
- Riseup: Riseup is a Seattle-based collective that supports freedom of expression and combats oppression. Their email service is accessible using the Tor network.
7. Blogs & Personal Sites (4)
There are many .onion service developers and enthusiasts that regularly publish their research and discoveries on their personal blogs.
- drksh: A hackers personal blog and Git repository.
- Jamie Scaife: Provides blog posts on using public Wi-Fi securely, website encryption, .onion services, operating system reviews, and Linux installation guides.
- Sarah Jamie Lewis: Sarah has contributed to several projects such as OnionShare (listed above in the Security & Privacy section), Ricochet, and a large body of research that helps Tor developers better understand the Tor network and .onion services.
- Traudt: A Naval Research Lab researchers' personal blog that covers Tor development and general internet topics.
8. Libraries (3)
Most libraries found in the Tor network allow for unlimited downloads without restrictions. This can be very liberating for people in many countries. However, it can also be illegal. The sites below list public domain content, unlicensed shared content, Creative Commons content, and other freely available media. However, some of it may be lifted from elsewhere, so be cautious and make sure to pay for items in a way where the original company or author gets their payday. We don't condone piracy.
- Comic Books: Lists a ton of downloadable comics that have lost their copyright and have hit the public domain. However, there may be copyrighted material here too, so be careful to avoid that.
- Imperial: An open-source, DRM-free repository of ebooks with the ability to upload books to the website to help grow the collection. Again, there may be copyrighted material here, so watch out.
- Z-Library: Z-Lib is the self-proclaimed "world's largest ebook library," with over 3.4 million books readily available for download. Yet again, there may be copyrighted material here, so watch out.
9. Social (8)
Signing up anonymously with social networks like Facebook can be extremely difficult. This is primarily why many Tor network social networks are created. With the ability to register anonymously, they allow users to communicate freely.
- Cyph Messenger: An open-source video chat and file transfer solution comparable to services like Skype.
- DNM Avengers: A forum for drug market discussions and reviews.
- Dread: A Reddit-like community for drug market discussions and reviews among other internet-related topics.
- Facebook: Tor network access to the most significant social network in the world.
- Hidden Answers: One example of a Stack Overflow-like platform that allows people to anonymously ask questions related to hacking, security and privacy, cryptography, marketplaces, government, and more. First appearing in the middle of 2015, they're one of the veteran onion services still available today.
- Smuxi: A free, user-friendly chat (IRC) client.
- Suprbay: The official TPB forum.
- TheHub: A forum for drug market discussions, news, and operational security guides created by anonymous individuals.
10. Hosting (10)
There's no shortage of hosting services in the Tor network. There are hundreds of websites dedicated to hosting images, notes, files, pastebins, and entire .onion websites.
- Black Cloud: A file upload service that claims to keep files encrypted on their servers.
- Daniel Uploads: An upload service with a 10 GB maximum file size limit. Uploaded content is publicly viewable.
- dhosting: A free and anonymous website hosting service. This service provides support for PHP, MySQL, FTP, and custom .onion addresses.
- Felixxx: An image hosting services with 30 days of storage time before content is purged from their servers.
- Image Hosting: A free image hosting service with no time limit. Files that exceed 5 MB in size are not allowed.
- Kowloon: A virtual private server hosting service with support for PHP, MySQL, PHPMyAdmin, encrypted server storage, customizable .onion domains, and up to 2 GB of storage.
- OnionContainers: Secure website hosting service with support for Nginx, PostgreSQL, and WordPress blogs.
- 0ut3r Space: Uploaded files are automatically deleted from their servers after 14 days. Files must be smaller than 200 MB in size.
- PopFiles: A simple file hosting service with the ability to create custom URLs. Uploaded files must not exceed 500 KB.
- Riseup Etherpad: A highly customizable and open-source editor designed for real-time team collaborations.
11. Operating Systems (3)
There are a handful of privacy-focused operating systems that can be downloaded anonymously.
- Debian: The Debian project is a collective of individuals who are committed to providing a free and easy-to-use operating system.
- Qubes: A free and open-source, security-focus operating system. Qubes takes an approach called "security by compartmentalization," which allows users to separate the various parts of their digital lives into securely isolated compartments called qubes.
- Whonix: An operating system designed for advanced privacy and security. Whonix users the Tor network and stream isolation to evade mass collection of internet traffic and user data. (Also appears in the Security & Privacy section above.)
12. SecureDrops (4)
SecureDrop is an open-source whistleblower submission system news organizations can install to safely and anonymously receive documents and tips from sources. It is used at over 50 news organizations worldwide, including The New York Times, The Washington Post, ProPublica, The New Yorker, and The Intercept.
- The Guardian: A British daily newspaper outlet, named "Newspaper of the Year" four times at the annual British Press Awards, the most recent in 2014 for being among the first to report on government surveillance.
- The Intercept: Launched in 2014, The Intercept initially served as a platform to report on the documents released by Edward Snowden. They've since dedicated their efforts to what it describes as "adversarial journalism."
- NPR: An American nonprofit media organization. NPR serves over 1,000 public radio stations.
- VICE: A digital media content and broadcasting company which covers a variety of topics such as politics, entertainment, drugs, and technology.
13. Bitcoin & Mixers (6)
There's no such thing as a truly untraceable bitcoin (BTC) transaction. Mixers are used to mix your BTC with other people's BTC, with the intention of obfuscating the trail back to its original source, aka you. When mixing BTC, your money is sent to an anonymous service and they essentially send you other people's BTC for the same amount. Mixers may aid in making transactions more difficult for companies and authorities to track.
Disclaimer: I'd like to remind readers that none of the .onions featured in this article have been verified as legitimate. Proceed with extreme caution when "anonymizing" bitcoin with mixers.
- Bitblender: Claims to have low, randomized fees, a bonus program, referral program, two-factor authentication with PGP, up to five simultaneous deposit addresses, fast processing, no saving of logs, and auto-withdrawal.
- BitCloak: Has a free API. Also randomizes fees at around two percent, though there is also a 0.0004 bitcoin fee for each payout address.
- Blockchain: Not much is known about Blockchain yet.
- CryptoMixer: Instant mixing, no logs, a minimum transaction size of .001 BTC, referral program, and variable fees depending on the size of the transaction.
- Elude: The service fee is set randomly between 1–3% from total amount.
- PrivCoin: A mixing service with support for a variety of cryptocurrencies.
14. Miscellaneous (12)
TorMetrics is just one of many useful sites provided by TheTorProject, Debian, and Riseup. There are too many categories and obscure websites to cover in this article. Below is a variety of websites accessible over Tor that readers may find interesting.
- CloudFlare: A privacy-focused DNS resolver that pledges to never sell or abuse user data.
- ExpressVPN: A VPN provider.
- ExoneraTor: A database containing IP addresses that are (or have been) associated with the Tor network.
- Fingerprint Central: A browser fingerprinting tool designed to help developers better defend against browser de-anonymization techniques.
- jRAT: A cross-platform malware. (Currently offline.)
- Keybase: A public key (GPG) database, private messaging application, and code-sharing (Git) service.
- Njalla: A privacy-focused domain name registar that allows anonymous registrations and cryptocurrency purchases.
- Ooni: An anti-censorship and anti-surveillance tool designed to observe and identify websites being blocked on a global scale.
- SMSPrivacy: An anonymous SMS service that allows users to register and purchase subscriptions with bitcoin.
- TorMetrics: An analytic tools designed to gather and visualize Tor network statistics to help developers understand traffic and patterns that occur in the network.
- Tor Nyx: A command-line tools that helps individual Tor users configure and access information about Tor instances running on their computers and servers.
- 0day: An exploit database with exploits for sale that can be purchased with bitcoin.
15. Onion Directories (6)
The trick to maintaining a relevant list of active .onions is knowing the .onion crawlers and directories. Onion crawlers regularly scan their databases to identify which websites have gone offline. Onions offline for a prolonged period are actively removed from databases and omitted from the open directories.
Below are a few directories for keeping up to date with the latest onions.
- CB3ROB: A database of nearly 4,000 active .onion services. (Currently offline.)
- Daniel's onions: A database of over 7,000 .onion services.
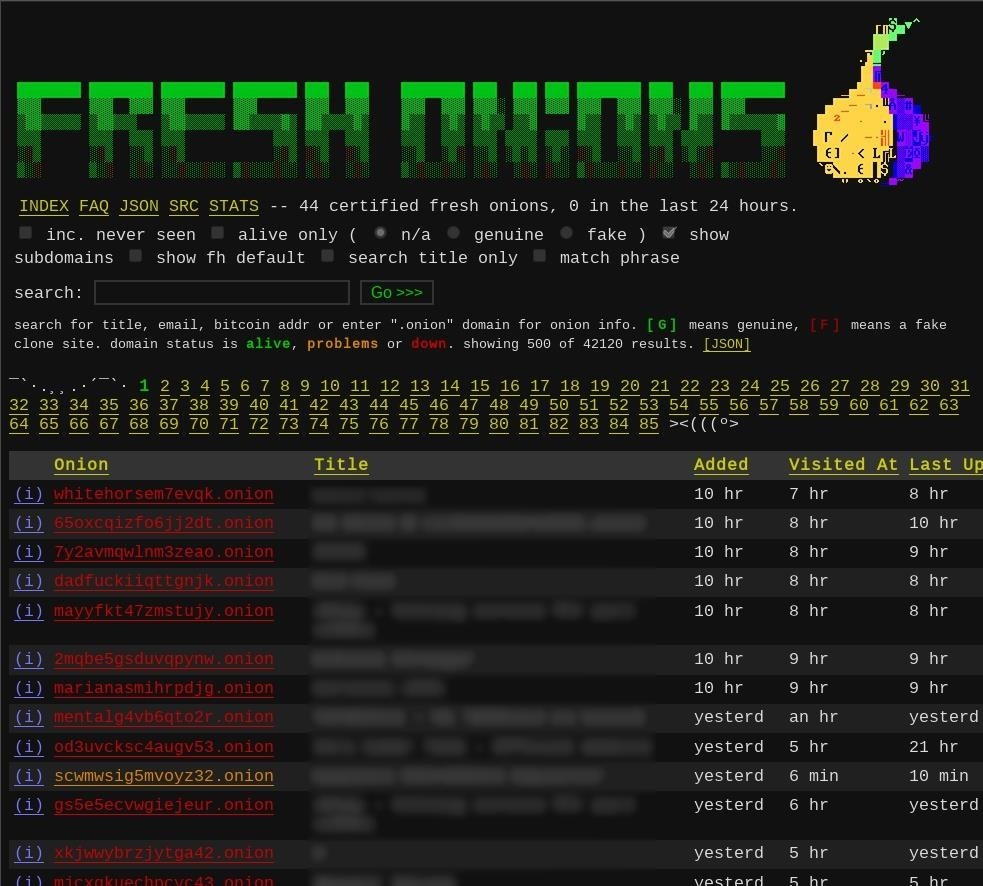
- Fresh Onions: An open-source database with over 5,000 unique .onion services listed.
- onionsoup: A curated selection of dozens of .onion services.
- UnderDir: A database of over 25,000 .onion services. Most are no longer online or accessible.
- VisiTOR: A database of over 5,000 .onion services.
Conclusion
Most .onion services disappear within hours of being spotted. This is likely the result of random individuals testing and experimenting with Tor. This is part of what makes .onion services unique and powerful for people who need to quickly share information anonymously. It's also what makes .onion services terrible for anyone seeking reliable, legitimate content. Anyone, anywhere in the world, with an inexpensive Android or Raspberry Pi can anonymously cut out their own private corner on the internet — all without submitting personal information, signing up for a subscription, or paying a dime to third-party providers.
If you have any questions or concerns, be sure to leave a comment below.
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.























Be the First to Comment
Share Your Thoughts